Microsoft Endpoint Configuration Manager is an on-premises management solution to manage desktops, servers, and laptops that are on your network or are internet-based. You can cloud-enable it to integrate with Intune, Azure Active Directory (AD), Microsoft Defender for Endpoint, and other cloud services.
A few days ago, Microsoft Endpoint Configuration Manager was found to have an important level of security
vulnerability, and the vulnerability has been made public. Microsoft said that no attacks against the vulnerability have been found for the time being. The company has credited
Brandon Colley of Trimarc Security for reporting the flaw.
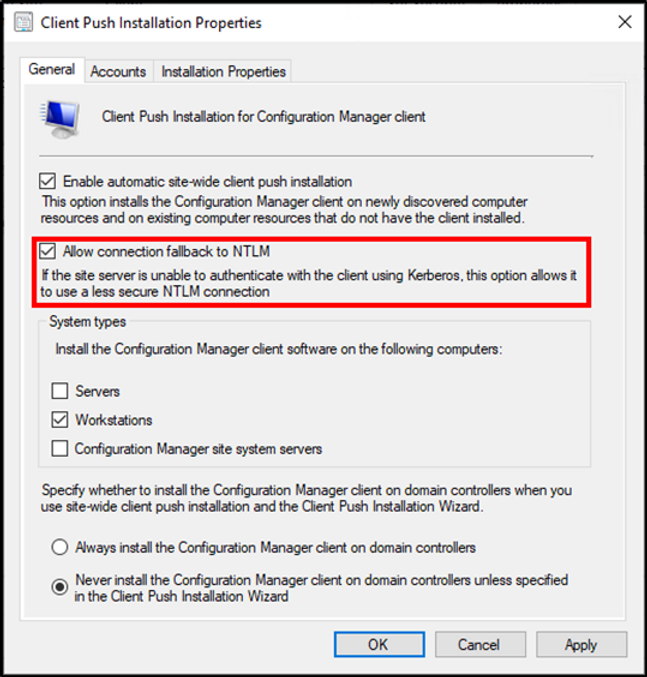
Image: trimarcsecurity
The vulnerability number is CVE-2022-37972, which is located in the Microsoft Endpoint Configuration Manager. This service is mainly used to manage intranet devices in batches. According to the description that the vulnerability level is important and the CVSS score is 7.5/10, Microsoft did not explain the details of the vulnerability but said that the vulnerability has been disclosed in advance.
Researchers speculate that the vulnerability may be related to the NTLM connection fallback because Microsoft has previously
introduced an update to modify the security process of NTLM authentication. Specifically, Microsoft provides a new option to actively disable allowing any connection through NTLM to be destroyed, which can improve corporate intranet security after disabling.
To resolve the CVE-2022-37972 flaw, Microsoft has launched an emergency update (KB 15498768) to fix this vulnerability to improve the security of the enterprise intranet. It is recommended that all enterprise administrators check the latest version of the configuration manager.
Microsoft wrote: “Environments using versions of Configuration Manager current branch prior to 2103 are encouraged to update to a later supported version. Administrators can also disable use of automatic and manual client push installation methods to remove the risk of exposure to this issue. “







