CVE-2022-38556: TRENDnet TEW733GR Static Default Credential Flaw
A vulnerability in certain TRENDnet routers can be exploited by remote attackers to gain full control of an affected device without any authentication, researchers claim.
The vulnerability exists because a system account has a default and static password. An attacker could exploit this vulnerability by using this default account to connect to the affected system. A proof-of-concept (PoC) exploit was recently made public by researchers for static default credential vulnerability affecting many TRENDnet TEW733GR routers.
TRENDnet’s N300 Wireless Gigabit Router, model TEW-733GR, offers proven high-performance 300 Mbps Wireless N networking and gigabit wired Ethernet ports. Embedded GREENnet technology reduces power consumption by up to 50%. For your convenience, this router comes pre-encrypted and features a guest network. Seamlessly stream HD video with this powerful router.

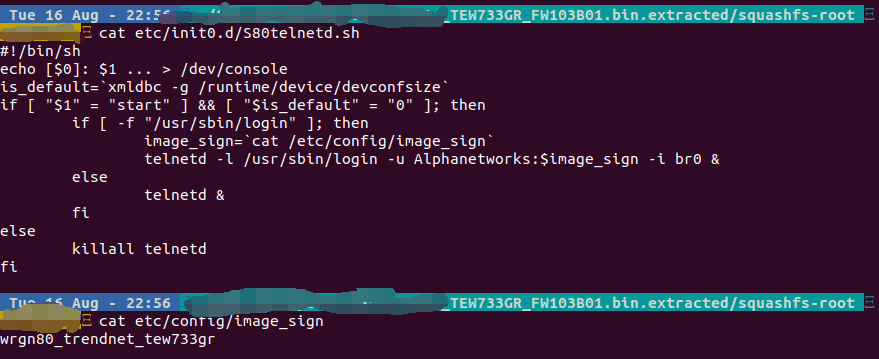
The static default credential vulnerability, tracked as CVE-2022-38556, exists in the Telnet service of Trendnet 733GR and it can allow an unauthenticated, remote attacker to take full control of the device to take control of vulnerable devices.
CVE-2022-38556 affects TRENDnet TEW733GR v1.03B01. The static default credential is in /etc/init0.d/S80telnetd.sh file. TRENDnet TEW733GR has reached end-of-life, so hardware and software engineering support are no longer provided for this product.
A search conducted with Shodan has shown that there are more than 183 potentially vulnerable devices accessible from the Internet, and most of them are located in the United States, followed by the United Kingdom.