CVE-2022-39944: Apache Linkis RCE Vulnerability
Recently, Apache Linkis fixed a deserialization vulnerability. The bug exists in the JDBC EngineConn module, an attacker could exploit this vulnerability to deserialize and thus achieve remote code execution. Track as CVE-2022-39944, the flaw severity is important.
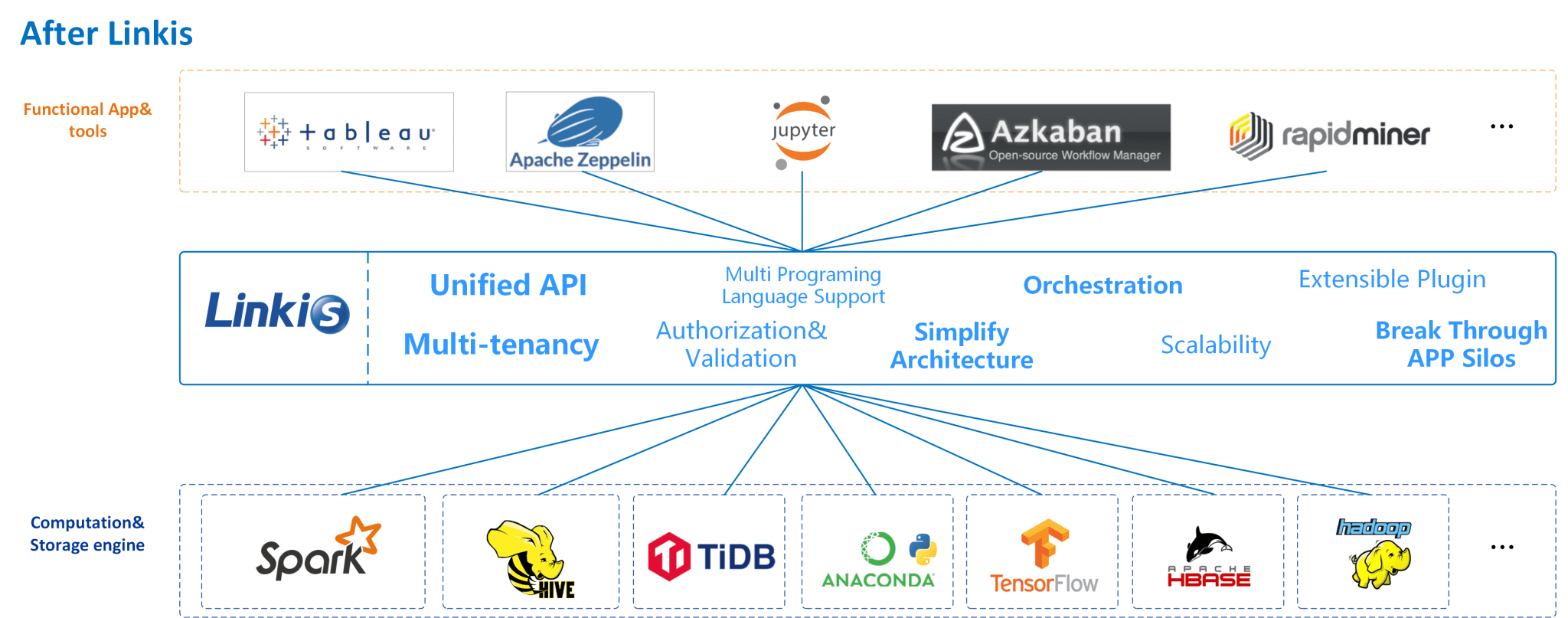
Apache Linkis builds a computation middleware layer to decouple the upper applications and the underlying data engines and provides standardized interfaces (REST, JDBC, WebSocket, etc.) to easily connect to various underlying engines (Spark, Presto, Flink, etc.) while enabling cross engine context sharing, unified job& engine governance and orchestration.

“In Apache Linkis <=1.2.0 when used with the MySQL Connector/J, a deserialization vulnerability with possible remote code execution impact exists when an attacker has to write access to a database and configures a JDBC EC with a MySQL data source and malicious parameters. Therefore, the parameters in the jdbc url should be blacklisted,” read the mailing list.
Security researcher 4ra1n and zac from ZAC Security Team have been credited with reporting the CVE-2022-39944 flaw.
Affected version
- Apache Linkis prior to 1.3.0
Unaffected version
- Apache Linkis 1.3.0
Solution
At present, Apache Linkis has fixed the vulnerability in the latest version. Users are advised to install please the unaffected version as soon as possible or upgrade the materials of JDBC EngineConn separately, you can refer to here.





