CVE-2022-40955: Apache InLong Remote Code Execution Vulnerability
Recently, Apache InLong fixed a deserialization vulnerability. This bug is caused by a flaw when MySQL JDBC connection URL parameters are deserialized by Apache InLong, an attacker could exploit this vulnerability to deserialize and thus achieve remote code execution. Track as CVE-2022-40955, the flaw severity is important.
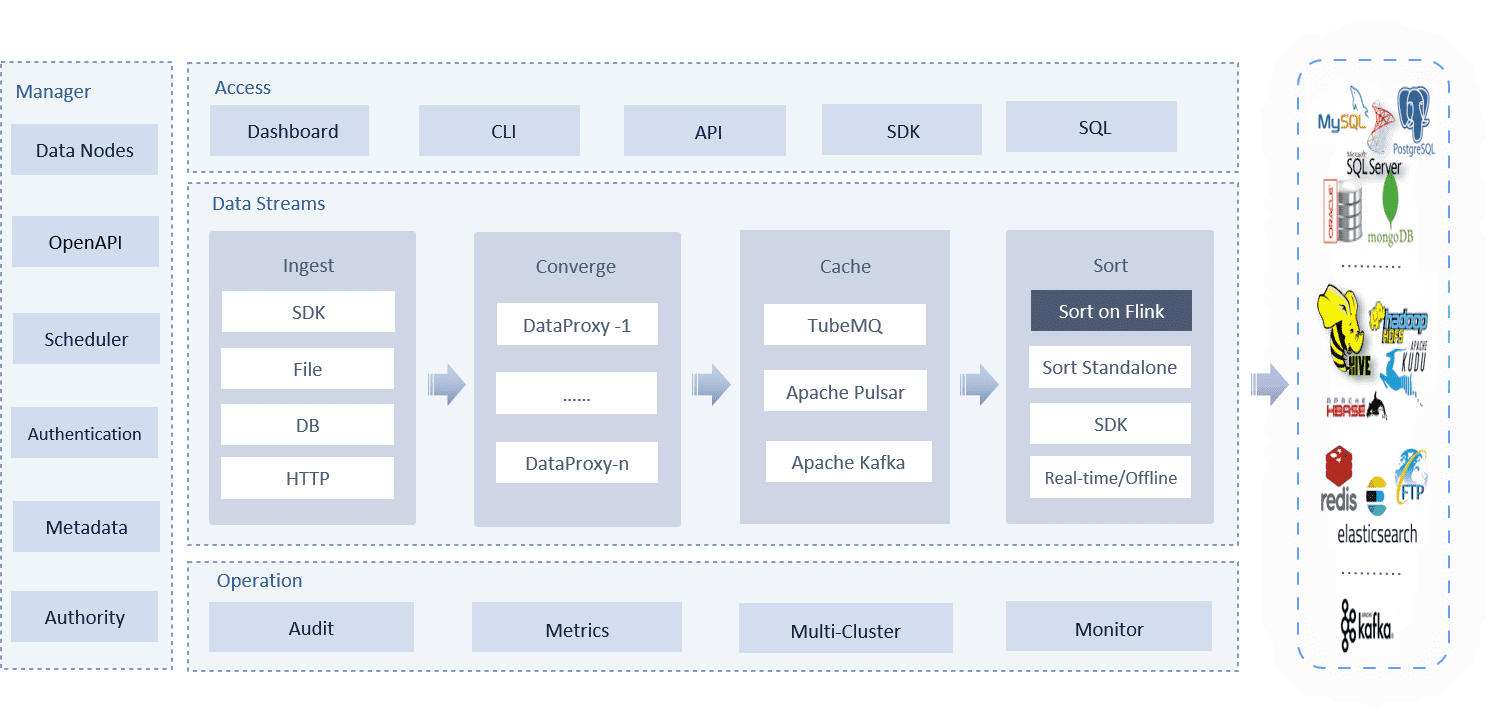
Apache InLong is a one-stop integration framework for massive data that provides automatic, secure, and reliable data transmission capabilities. InLong supports both batch and stream data processing at the same time, which offers great power to build data analysis, modeling, and other real-time applications based on streaming data.

“In versions of Apache InLong prior to 1.3.0, an attacker with sufficient privileges to specify MySQL JDBC connection URL parameters and to write arbitrary data to the MySQL database, could cause this data to be deserialized by Apache InLong, potentially leading to Remote Code Execution on the Apache InLong server,” read the security bulletin.
Security researcher 4ra1n of Chaitin Tech has been credited with reporting the CVE-2022-40955 flaw.
Affected version
- Apache InLong prior to 1.3.0
Unaffected version
- Apache InLong 1.3.0
Solution
At present, Apache InLong has fixed the vulnerability in the latest version, Users are advised to install please the unaffected version as soon as possible.





