CVE-2023-26035: RCE flaw in open-source software application ZoneMinder
ZoneMinder developers last week shipped patches to address a new round of critical security vulnerabilities affecting its application that could be exploited by an attacker to read system files and execute arbitrary code.
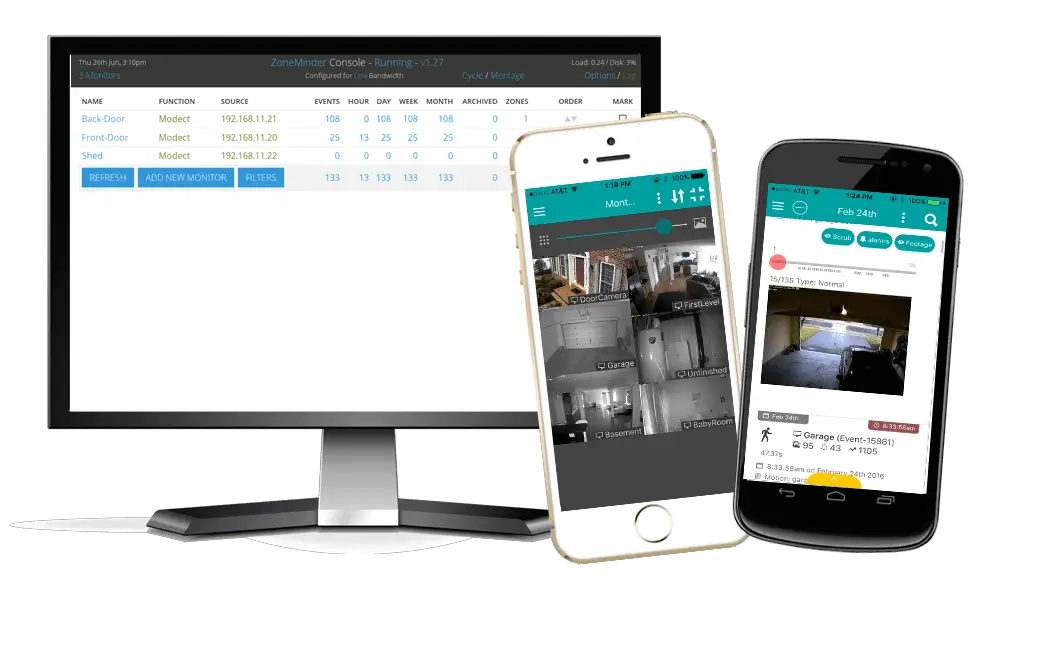
ZoneMinder is an integrated set of applications that provide a complete surveillance solution allowing capture, analysis, recording, and monitoring of any CCTV or security cameras attached to a Linux-based machine. It is designed to run on distributions that support the Video For Linux (V4L) interface and has been tested with video cameras attached to BTTV cards, and various USB cameras and also supports most IP network cameras.

The most critical flaw affecting ZoneMinder tracked as CVE-2023-26035 (CVSS score: 10), stems from an insufficient validation of permissions check to the snapshot.php file of the software.
“There’s no permissions check on https://github.com/ZoneMinder/zoneminder/blob/master/web/includes/actions/snapshot.php#L25 and https://github.com/ZoneMinder/zoneminder/blob/master/web/includes/actions/snapshot.php#L36 is expecting an id to fetch an existing monitor but you can pass an object to create a new one instead. TriggerOn ends up calling shell_exec here
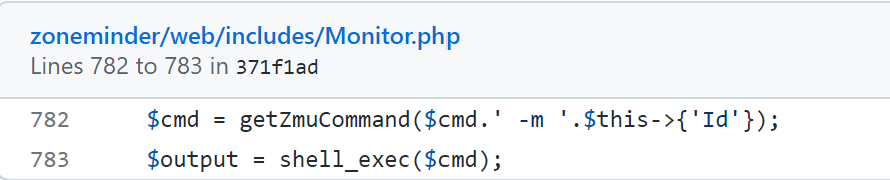
using the supplied Id,” the developer said in an advisory.
CVE-2023-26035 affects Zoneminder versions prior to 1.36.33, and prior to 1.37.33.
Tracked as CVE-2023-26034 (CVSS score of 9.6), CVE-2023-26032 (CVSS score of 8.9), and CVE-2023-26037, the vulnerabilities could allow an attacker to view, add, modify, or delete information in the back-end database.
The developer said three issues stem from insufficient input validation of user-supplied command arguments, which existed in the filter[Query][terms][0][attr] query string parameter of the /zm/index.php endpoint, username field of the JWT token, and minTime and maxTime requests parameters.
Also addressed by ZoneMinder are four other flaws –