CVE-2023-29007: Git Users Beware of Arbitrary Configuration Injection Vulnerability
Git, the popular version control system, is at the center of a newly identified security vulnerability that has the potential to compromise user data and execute arbitrary code. Designated as CVE-2023-29007 and assigned a CVSS score of 7.0, this vulnerability arises from a logic error in Git’s implementation for renaming or deleting sections of a configuration file.
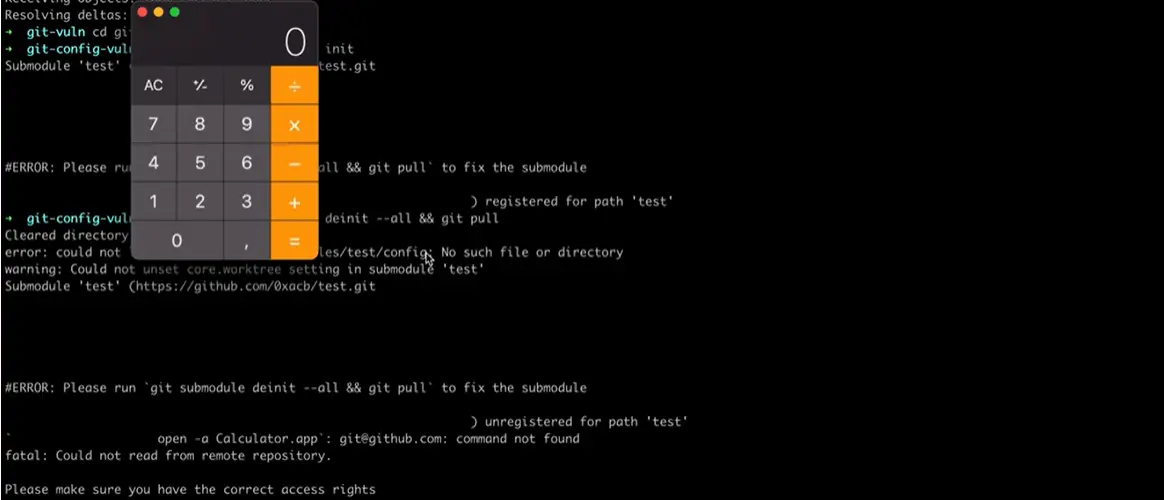
The issue stems from Git’s improper handling of configuration values longer than a fixed length, causing it to treat these values as new sections. Consequently, an attacker can exploit this vulnerability to inject arbitrary configuration settings into a user’s $GIT_DIR/config file when renaming or removing a malicious configuration section. This can lead to arbitrary code execution through configuration values that specify executables, such as core.pager, core.editor, and core.sshCommand.
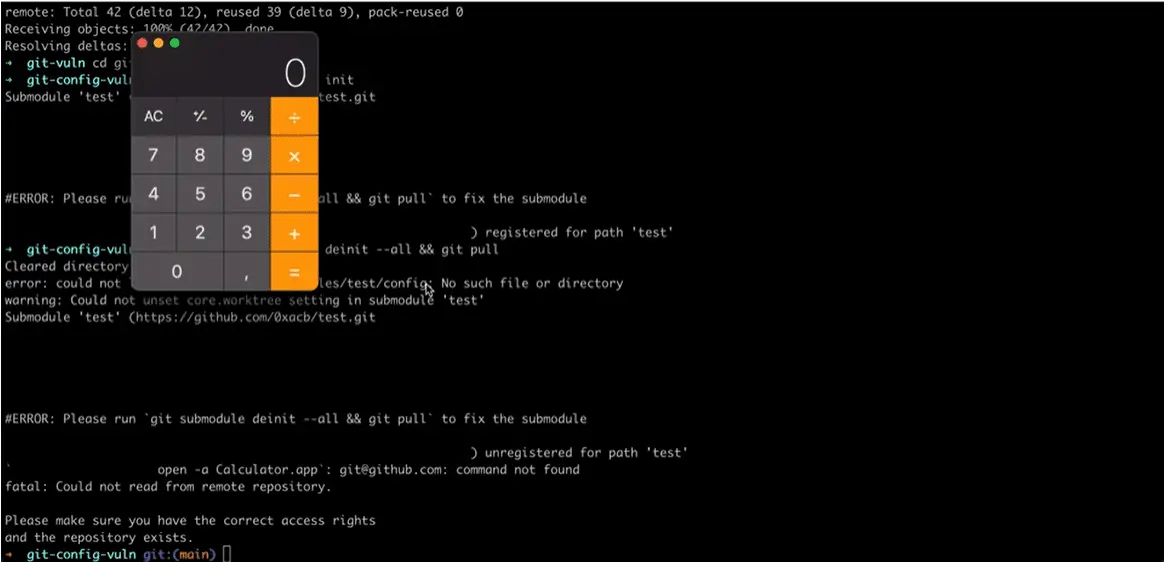
CVE-2023-29007 can be exploited using overly-long submodule URLs, which are stored in a user’s $GIT_DIR/config upon initialization. When removing those sections with commands like “git submodule deinit,” these URLs may be misinterpreted as containing new configuration material. This vulnerability affects Git versions 2.40.0 and older, and while exploiting it can be complex, it still poses a significant threat as it requires user interaction through legitimate Git commands.
The impact of this vulnerability is substantial, as it can lead to arbitrary code execution by injecting values for executables like core.pager, core.editor, and core.sshCommand. The proof of concept for this submodule attack vector is available here.
Thankfully, patches have been prepared to address this issue and will be included in Git versions v2.30.9, v2.31.8, v2.32.7, v2.33.8, v2.34.8, v2.35.8, v2.36.6, v2.37.7, v2.38.5, v2.39.3, and v2.40.1. As a temporary workaround, users are advised to avoid running “git submodule deinit,” “git config –rename-section,” or “git config –remove-section” on untrusted repositories or without prior inspection of their $GIT_DIR/config.
In conclusion, Git users should remain vigilant about this security vulnerability and update their software as soon as the patches are released. By staying informed and exercising caution, users can safeguard their data and prevent the arbitrary execution of malicious code.






