CVE-2023-31505: Schlix CMS Flaw Exposes Websites to RCE, No Patch Available
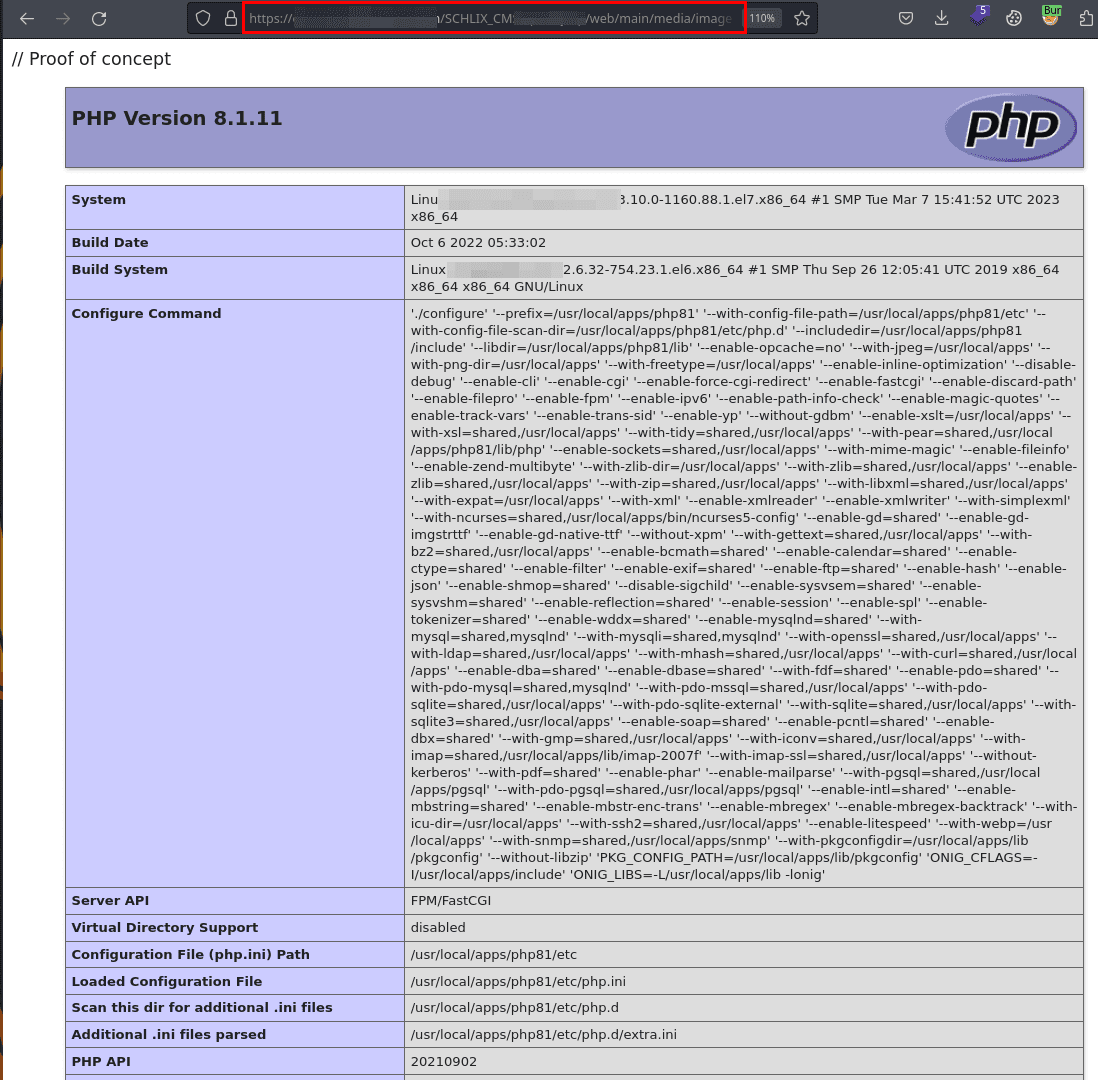
In the dynamic world of content management systems (CMS), Schlix CMS has stood out as a high-performance, multi-site solution that empowers users to create websites and blogs effortlessly. Renowned for its openness, extensibility, scalability, and ability to handle high-traffic loads, Schlix CMS offers an intuitive interface that streamlines website management. However, a recent discovery has exposed a critical vulnerability, CVE-2023-31505, which grants unauthorized users the power of remote code execution (RCE) on the server.
The vulnerability in question, identified as CVE-2023-31505, poses a severe threat to Schlix CMS users. An authorized user can exploit this flaw by uploading a file with a “.phtml” extension to a location of their choosing. Once uploaded, they gain control over the file’s content, effectively allowing them to execute arbitrary code remotely on the server.

The consequences of CVE-2023-31505 are significant. This vulnerability affects the latest version of Schlix CMS, specifically version v2.2.8-1. As of the time of this article, there is no official fix or patch available to address this flaw, leaving Schlix CMS users exposed to potential exploitation.
Security researcher m3n0sd0n4ld is credited with uncovering this critical vulnerability within Schlix CMS. Notably, m3n0sd0n4ld has not only identified the flaw but has also published a proof-of-concept, providing insight into the potential exploit.
Understanding the exploitation process is crucial for users seeking to protect their Schlix CMS installations. The steps involved in exploiting CVE-2023-31505 are as follows:
1. Login to the Schlix CMS admin panel using legitimate credentials.
2. Navigate to the “Tools -> Media Manager” menu located on the left side of the interface.
3. Click on the “Upload File” option and attempt to upload a file to the “images” folder. Capture the associated request using tools like Burp Suite.
However, during this process, it becomes evident that Schlix CMS does not accept files of this type, thwarting the attempted upload. Yet, the critical revelation lies in the fact that the application does accept “.phtml” files. This crucial oversight opens the door for attackers to upload malicious code disguised as proof of concept, potentially leading to remote code execution on the server.
As Schlix CMS users await an official fix, it is imperative to exercise caution and vigilance. Practicing stringent access control, monitoring file uploads, and keeping abreast of security updates are essential steps to mitigate the risk posed by this vulnerability.





