CVE-2023-33241 allows an attacker to extract a full private key from wallet using the GG18 and GG20 protocols
The cybersecurity landscape is ever-changing, and vulnerabilities can emerge in even the most secure of systems. Such is the case with the CVE-2023-33241 vulnerability, a critical security flaw that has recently been discovered in the popular multi-party computation (MPC) protocols GG18 and GG20. These protocols are essential in the cryptocurrency wallet industry, and the vulnerability could potentially allow malicious actors to extract full private keys from any wallet utilizing these protocols. The discovery serves as a stark reminder of the relentless pursuit of security in the digital age.

Fireblocks’ research team identified this vulnerability at the pseudocode level in GG18 and GG20, protocols considered groundbreaking in the MPC wallet industry. Over 10 wallets and libraries, including Binance custody, were found to be susceptible to this flaw.
The vulnerability arises from parties failing to verify whether the attacker’s Paillier modulus (denoted N) contains small factors or if it is a biprime. By exploiting this flaw, a threat actor can interact with the signatories in the MPC protocol to steal their secret shards and eventually acquire the master secret key.

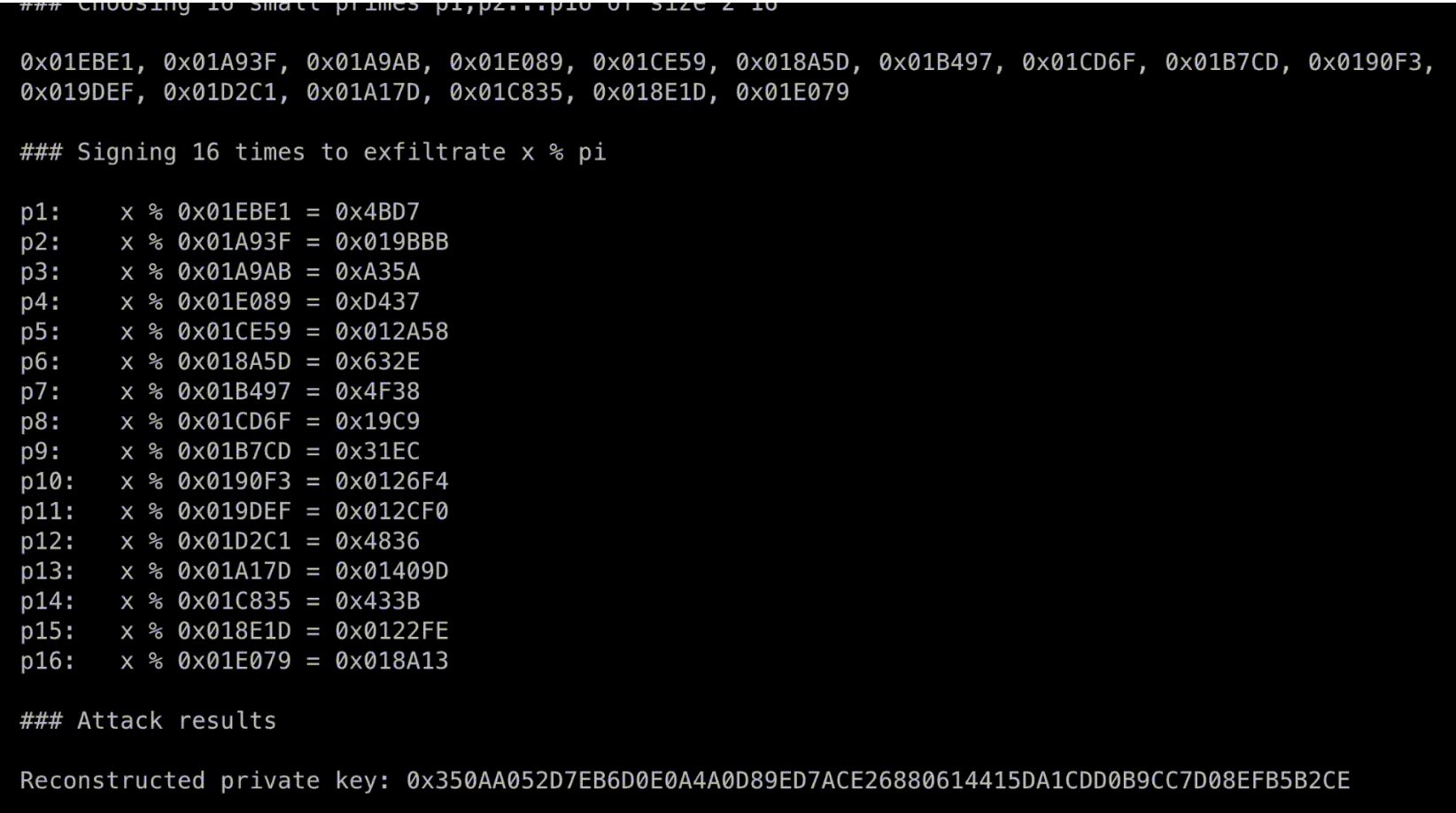
Different implementations result in different levels of vulnerability. While some implementations may allow key extraction in 16 signatures, others may necessitate up to 1 billion signatures. The vulnerability’s severity lies in its ability to grant an attacker access to all funds within a crypto wallet.
Two specific scenarios illustrate how this vulnerability can be exploited:
- Case 1: Using malicious messages, an attacker can obtain private key shards by interacting with the signatories in the MPC protocol’s first round. A specific instance of this was found in the Apache Milagro library.
- Case 2: Here, the attacker actively controls one of the signatories and interacts throughout the entire MPC protocol. Depending on the number of parties and the malicious Paillier modulus N, the number of (failed) signatures can range from 200K to 1 billion.
Given the widespread use of the GG18/20 protocols, understanding the parameters used and acting accordingly is of paramount importance. Some of the commonly utilized libraries are no longer actively maintained, increasing the risk.
To rectify the issue, the utilization of a key-generation process that can detect maliciously formed Paillier modulus using a suitable Zero-Knowledge (ZK) proof is recommended.
The CVE-2023-33241 vulnerability showcases the complex and constantly evolving nature of cybersecurity. Ensuring that systems are up to date and understanding the parameters involved in the use of these protocols is critical for the continued security of digital assets. The code for CVE-2023-33241 has been released for review, a step towards an increasingly transparent and collaborative effort in the relentless pursuit of digital security. The discovery of this vulnerability underscores the need for vigilance, continuous monitoring, and collaboration in the face of emerging threats.