CVE-2023-41330: Critical RCE Flaw Reported in Popular Snappy PHP Library

Snappy, an immensely popular PHP library, facilitates the creation of thumbnails, snapshots, and PDFs from URLs or HTML pages. Boasting over 11 million downloads, this software primarily relies on the trusted webkit-based utilities – wkhtmltopdf and wkhtmltoimage, available on a diverse range of platforms. But even the mightiest can falter, as a vulnerability with a high CVSS score of 9.8 has been discovered.
Earlier on March 17th, a vulnerability, coded as CVE-2023-28115, came into the limelight. This flaw gave cyber attackers a window to execute remote code through PHAR deserialization. Addressing this critical issue, Snappy rolled out version 1.4.2, implementing an additional check in the function in question to mitigate the usage of the `phar://` wrapper.

Rémi Matasse, a diligent security researcher from Synacktiv, unearthed the flaw CVE-2023-41330, which, in essence, is a cunning bypass of the previous patch. The twist? PHP wrappers, like the one used in Snappy, are case-insensitive. The patch designed to fix the original vulnerability only looked out for the lowercase `phar://` string, leaving it vulnerable to a more crafty, upper-case bypass, `PHAR://`.
Should this flaw be exploited successfully, the consequences are dire:
- Arbitrary code execution
- Unrestricted access to the underlying filesystem
To leverage the CVE-2023-41330 vulnerability, however, there are prerequisites. An attacker needs the ability to upload a file, and the server must be running a PHP version preceding PHP 8.
Diving deeper into the technicalities, if a user takes control of the second parameter of the `generateFromHtml()` function, this value then gets passed on to the `prepareOutput()` function as the $filename parameter. This was where the first vulnerability exposed its teeth, allowing filenames with a `phar://` wrapper to trigger a deserialization on any given PHAR files.
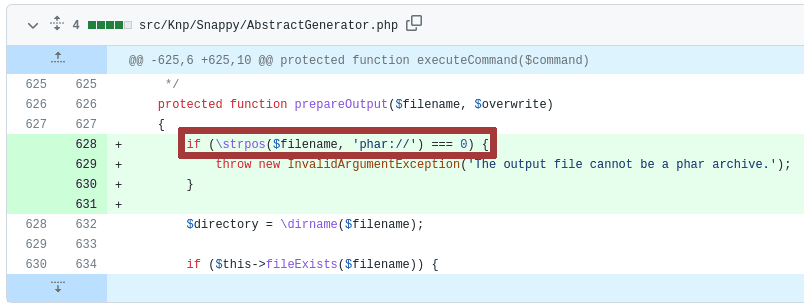
The patch tried to prevent this by using the `strpos()` function to check if the string started with `phar://`. However, the case-insensitivity loophole of PHP wrappers makes it possible for an attacker to bypass this patch using the uppercase `PHAR://`.
To counteract this flaw, Synacktiv has proposed a more robust solution. Instead of a blacklist approach, a whitelist approach should be considered. This would ensure that only the `http://`, `https://`, or `file://` wrappers are permitted in the `generateFromHtml()` function.
Affected Snappy versions include all versions up to and including 1.4.2. The subsequent version, 1.4.3, addresses this vulnerability.
For those who can’t immediately upgrade to the patched version, a suggested workaround is to maintain stringent control over user data submitted to the function `AbstractGenerator->generate(…)`.





