CVE-2023-43654: A maximum severity Pytorch TorchServe vulnerability
What comes to mind when you hear names like Google, Facebook, and Microsoft? Giants in the tech industry, right? And when such giants trust a particular tool, you’d expect it to be rock solid, especially when it’s about securing sensitive data and machine learning models. However, a recent vulnerability discovery has revealed that TorchServe is vulnerable to server-side request forgery (SSRF) attacks.
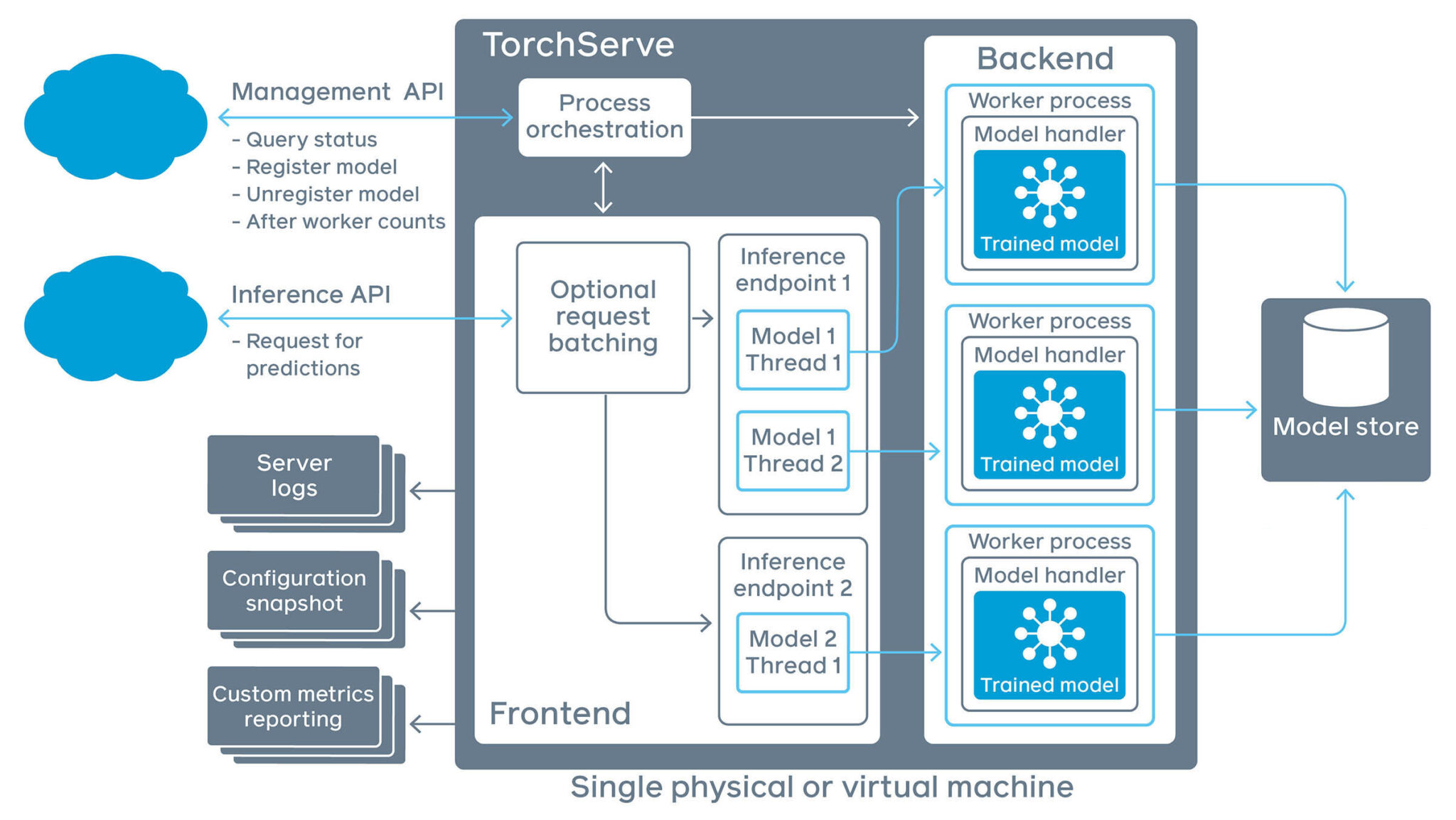
To begin, let’s understand the star of this show: PyTorch TorchServe. This is not just any serving tool—it’s a production-ready model serving and scaling framework designed exclusively for PyTorch models. In layman’s terms, it’s the bridge between your PyTorch model and the real-world users who need to interact with it. It promises flexibility and ease of use for those looking to deploy their models at scale.

ShellTorch isn’t a flashy new AI tool or some groundbreaking technique. Rather, it’s a collective name for a series of critical vulnerabilities in TorchServe. The most alarming of these vulnerabilities, CVE-2023-43654, boasts a chilling CVSS score of 10, marking it as “critical.”
At its core, ShellTorch offers malicious entities a golden ticket – access to proprietary AI models, the ability to inject malevolent models, and the chance to leak sensitive data. But its capabilities don’t stop there. It can even alter the results churned out by a model or, in the worst-case scenario, take over a server completely.
As a result of a flaw in TorchServe’s default configuration, ShellTorch takes advantage of poor input validation. By doing this, it paves the way for a server-side request forgery (SSRF) attack. To put it simply, attackers can send specially crafted requests to exploit this vulnerability. The fallout? The integrity of a system is compromised, and a goldmine of sensitive data lies exposed.
Researchers from Oligo Security were the first to unearth these vulnerabilities in July 2023. The most shocking revelation was that TorchServe’s management interface could be accessed publicly without any form of authentication. Worse, it allowed model uploads from any domain, no questions asked.
But perhaps the most concerning fact is the sheer scale of this vulnerability. Major players, including Amazon’s AWS SageMaker and Google’s Vertex AI, were left vulnerable. KServe, the Model Inference Platform standard for Kubernetes, too, didn’t escape unscathed.
It’s essential to grasp the magnitude of what ShellTorch can do. Beyond simply gaining access to a server, it allows attackers to manipulate, steal, and even delete AI models. The sensitive data that flows to and from a TorchServe server is also up for grabs. Considering that countless Fortune 500 companies use TorchServe, the implications are dire.
There are a few things that TorchServe users can do to mitigate the CVE-2023-43654 vulnerability:
- Upgrade to TorchServe release 0.8.2 or later.
- Configure the allowed_urls setting to only allow requests to trusted servers.
- Use a web application firewall (WAF) to block malicious requests.
It is also important to note that TorchServe users should not use the default configuration, as it is vulnerable to SSRF attacks. Users should carefully review the TorchServe documentation and configure the system to meet their specific needs.





