CVE-2023-46685 (CVSS 9.8) Leaves LevelOne Routers Open to Hackers, No Patch
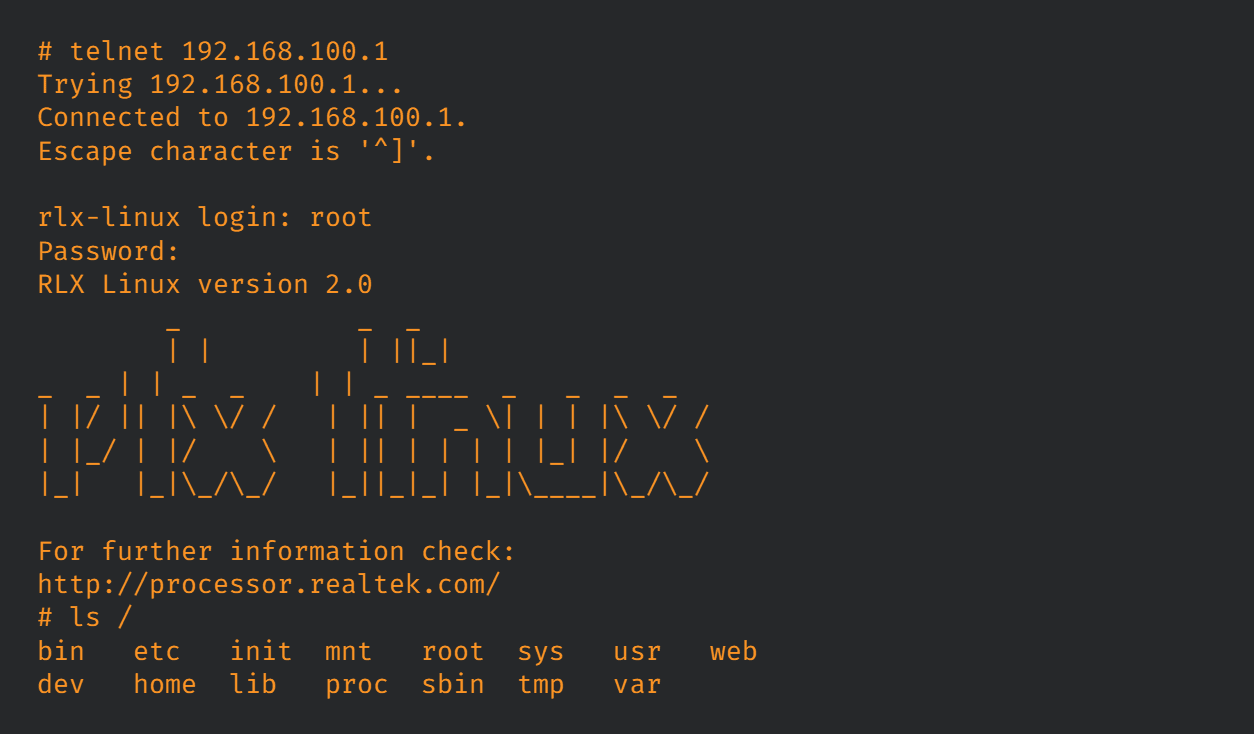
A recently discovered, severe security vulnerability (CVE-2023-46685) is putting thousands of LevelOne WBR-6013 routers at risk of complete takeover. Cybersecurity researcher Francesco Benvenuto at Talos has uncovered a hard-coded password lurking within the router’s telnet service – a backdoor that could grant attackers unfettered access.
The vulnerability, rated with a CVSS score of 9.8, resides in the telnetd service of the LevelOne WBR-6013 SOHO (Small Office/Home Office) wireless router, specifically in firmware version RER4_A_v3411b_2T2R_LEV_09_170623. The telnetd service, which listens for connections, is not mentioned in the router’s documentation, nor are the credentials required for login. This lack of transparency leaves users unaware of the potential risks.
The critical flaw stems from the use of hard-coded passwords stored in the /etc/passwd_orig file, which is utilized as the /etc/passwd file on the device. These credentials are weak and hardcoded, allowing an attacker to gain root access to the device by simply connecting to the telnetd service and providing the hard-coded root password. This access could lead to arbitrary command execution, giving the attacker complete control over the router.
Despite the critical nature of this flaw, LevelOne has declined to patch the vulnerability in their software. This decision leaves users of the WBR-6013 router vulnerable to potential exploits. Users are advised to consider alternative measures to protect their networks, such as replacing the router with a more secure model from a different manufacturer or implementing additional network security measures to mitigate the risk.
In addition to CVE-2023-46685, Francesco Benvenuto of Cisco Talos has also detailed another vulnerability, CVE-2023-49593 (CVSS 7.2), affecting the WBR-6013 wireless router.





