CVE-2024-0012 and CVE-2024-9474: Actively Exploited Vulnerabilities Impact Palo Alto Networks PAN-OS
Palo Alto Networks has issued critical advisories regarding two actively exploited vulnerabilities in their PAN-OS software, posing significant risks to organizations relying on the platform for network security. These flaws, identified as CVE-2024-0012 and CVE-2024-9474, target the management web interface and demand immediate attention.
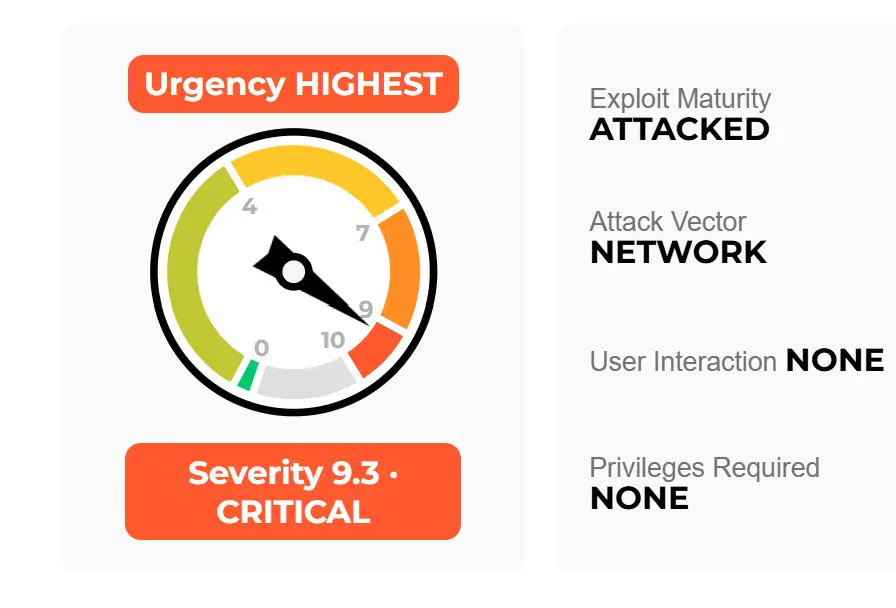
The CVE-2024-0012 (CVSS 9.3) vulnerability allows an unauthenticated attacker with network access to the management web interface to bypass authentication entirely. Exploitation of this flaw could grant administrative privileges, enabling malicious actors to “tamper with the configuration, or exploit other authenticated privilege escalation vulnerabilities,” as stated in the advisory.
PAN-OS versions 10.2, 11.0, 11.1, and 11.2 are vulnerable unless updated to patched releases (e.g., 11.2.4-h1 or later). Palo Alto Networks emphasizes, “The risk of this issue is greatly reduced if you secure access to the management web interface by restricting access to only trusted internal IP addresses.” Ensuring robust deployment practices is paramount to reduce exposure.
Threat actors have been observed targeting this vulnerability on internet-facing management web interfaces, amplifying the urgency for organizations to secure their assets immediately.
The second vulnerability, CVE-2024-9474, offers an opportunity for attackers with administrator-level access to escalate privileges, potentially obtaining root access on affected systems. While less severe than CVE-2024-0012, its medium-level CVSS score of 6.9 still warrants critical attention.
“Palo Alto Networks observed threat activity that exploits this vulnerability against a limited number of management web interfaces that are exposed to internet traffic coming from outside the network,” the company warns.
Similar to CVE-2024-0012, this issue impacts PAN-OS 10.1 through 11.2, requiring upgrades to versions such as 11.2.4-h1. Secure configurations and trusted IP restrictions are also essential mitigations for this vulnerability.
Palo Alto Networks strongly recommends following their best practices for securing administrative access:
- Restrict Interface Access: Limit management access to trusted internal networks.
- Patch Immediately: Upgrade to the latest secure PAN-OS versions, including 11.2.4-h1 for 11.2 users.
- Threat Prevention Subscriptions: Leverage Threat IDs (e.g., 95746, 95747) to block exploit attempts, provided your subscription and configurations support these defenses





