CVE-2024-20017 (CVSS 9.8): Zero-Click Exploit Discovered in Popular Wi-Fi Chipsets, PoC Published

Security researcher Hyprdude has published detailed information and a proof-of-concept (PoC) exploit for a critical vulnerability identified as CVE-2024-20017. With a CVSS score of 9.8, this vulnerability poses a severe risk, potentially allowing attackers to execute remote code on vulnerable devices without the need for user interaction.
The CVE-2024-20017 vulnerability is rooted in the wappd network daemon, a critical component of the MediaTek MT7622/MT7915 SDK and RTxxxx SoftAP driver bundle. These chipsets are widely used in Wifi6 (802.11ax) devices, including popular models from Ubiquiti, Xiaomi, and Netgear. The wappd service is designed to manage wireless interfaces and access points, particularly in configurations involving Hotspot 2.0 and related technologies.
This vulnerability affects a range of MediaTek chipsets, including MT6890, MT7915, MT7916, MT7981, MT7986, and MT7622. This means a vast array of devices, from routers to smartphones, are potentially at risk. The affected software includes MediaTek SDK versions 7.4.0.1 and earlier, as well as OpenWrt 19.07 and 21.02.
The vulnerability arises from an out-of-bounds write due to improper input validation within the wlan service. Specifically, it is caused by a buffer overflow in the IAPP_RcvHandlerSSB() function. This function processes data received from network sockets, and a lack of thorough bounds checking allows an attacker to craft malicious packets that can overflow a 167-byte stack-allocated buffer, potentially overwriting critical memory regions.
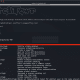
The vulnerable code snippet from IAPP_RcvHandlerSSB() is shown below:
The most concerning aspect of CVE-2024-20017 is its potential to enable remote code execution (RCE). This means that an attacker could exploit this flaw to run malicious code on a vulnerable device, potentially gaining full control over it. Since no additional execution privileges or user interaction are required, this vulnerability is particularly dangerous for embedded devices, such as routers and access points, which are often overlooked in security patching processes.
MediaTek patched this flaw in March, so the first step is to ensure all your devices are running the latest firmware and software updates. If you have a vulnerable device, check with the manufacturer for available updates.
With the PoC exploit for CVE-2024-20017 now available on GitHub, organizations, and individuals using affected devices must ensure their firmware is up-to-date to prevent potential compromises.
Related Posts:
- Veeam Backup & Replication Faces RCE Flaw– CVE-2024-40711 (CVSS 9.8) Allows Full System Takeover
- CVE-2024-38650 & CVE-2024-39714 (CVSS 9.9): Critical Flaws in Veeam Console Put Data at Risk
- Over 30% of Android devices have eavesdropping vulnerabilities, MediaTek is releasing an update to fix the vulnerabilities
- Mediatek Chipsets code execution vulnerability
- Critical Vulnerabilities Discovered in Ivanti Connect Secure and Policy Secure