CVE-2024-21320 PoC Published- How Microsoft Themes Can Compromise Your Credentials
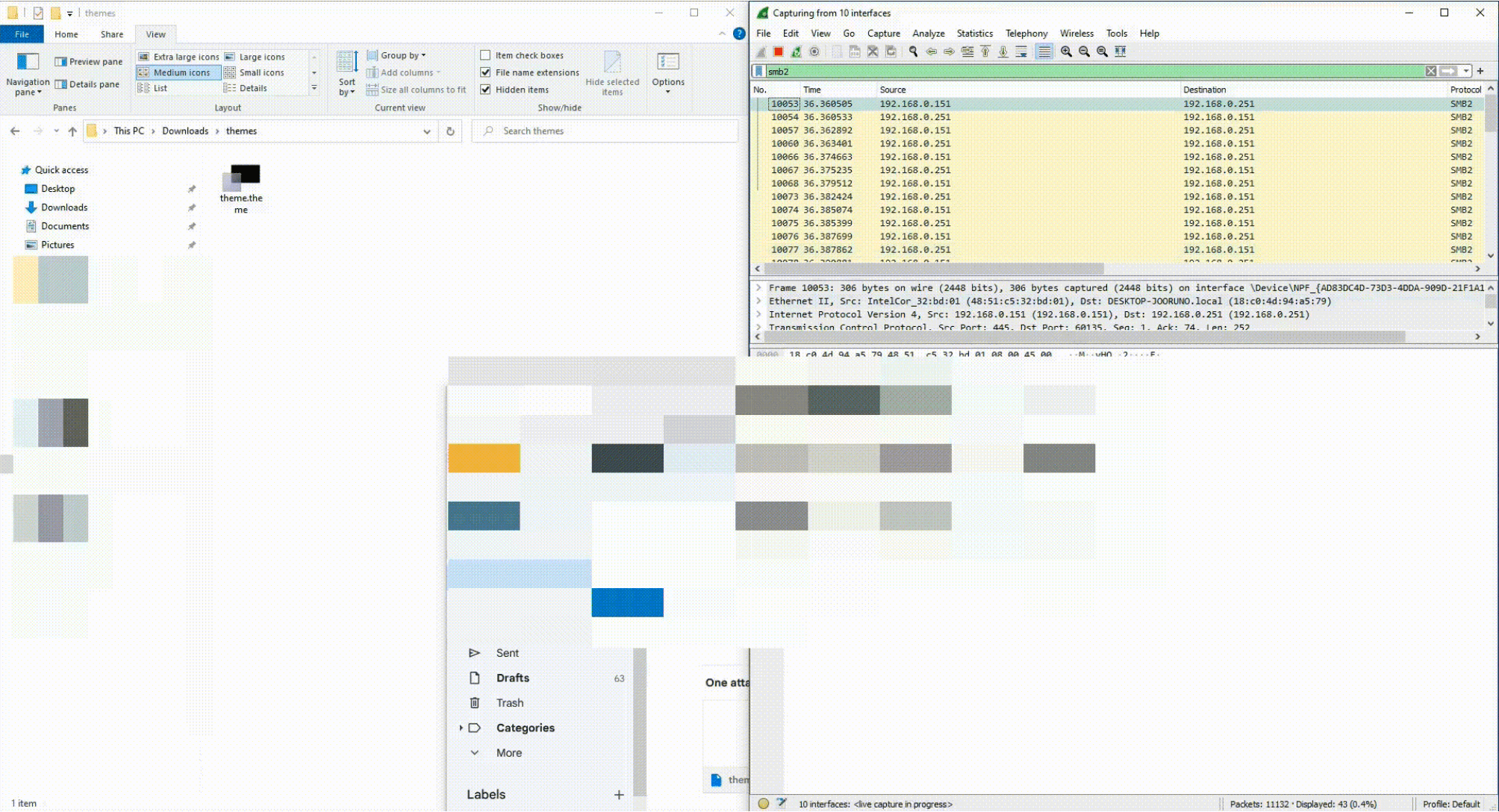
Akamai security researcher Tomer Peled recently unveiled the technical detail and proof-of-concept (PoC) for a vulnerability within Microsoft Themes (CVE-2024-21320). This vulnerability, with a CVSS score of 6.5, enables attackers to execute authentication coercion attacks. If successful, these attacks can lead to the theft of sensitive user credentials, posing a significant security risk.
The Exploit: How It Works
At the heart of this vulnerability lies the way Microsoft Themes handles certain file parameters. The BrandImage, Wallpaper, and VisualStyle parameters within a theme file can be leveraged by attackers to trigger malicious network activity. When a user views a compromised theme file (even without directly opening it), Windows automatically attempts to generate a thumbnail preview. During this process, if the aforementioned parameters have been tampered with to point to a remote UNC path under the attacker’s control, the victim’s machine will unknowingly transmit its NTLM credentials over an SMB connection.

Image: Akamai
Akamai offers a proof-of-concept (PoC) Theme file and video, aiding in understanding and replicating the CVE-2024-21320 vulnerability.
Real-World Risk: The Power of NTLM Credentials
Obtaining a user’s NTLM credentials presents attackers with a dangerous toolkit:
- NTLM Relay Attacks: Relaying pilfered NTLM hashes allows attackers to mimic the victim’s identity on the network. This grants them unauthorized access to sensitive systems and resources.
- Offline Password Cracking: Attackers have the option of employing password-cracking software to attempt to brute-force the victim’s actual password using the NTLM hash as a starting point.
Historical Precedents and Mitigation
This Microsoft Themes vulnerability is worrisome because it echoes similar exploits that have surfaced in the recent past. The 2023 Outlook vulnerability demonstrated the effectiveness of these attack vectors when targeting NTLM authentication.
In response to the discovery, Microsoft issued a patch as part of their January 2024 Patch Tuesday release. This update introduced checks to validate whether a path is a UNC path and whether the system policy permits the use of UNC paths for theme files. Additionally, a new registry value, “DisableThumbnailOnNetworkFolder,” was introduced to further mitigate the risk. However, the implementation raised eyebrows, as Akamai’s investigation suggested that the mere viewing of a specially crafted file, contrary to Microsoft’s claims, was sufficient to trigger the vulnerability.
Moreover, there are additional preventative measures organizations should consider:
- NTLM Policy Controls: Windows 11 users can fortify their defenses by blocking NTLM authentication in SMB transactions with external entities through Group Policy adjustments. Microsoft’s “Restrict NTLM” policy offers another layer of protection, hampering the effectiveness of such attack vectors.
- Network Segmentation: Microsegment your network to create clearly defined zones with controlled traffic flows. This helps to contain the potential damage of an NTLM compromise by preventing lateral movement within your network.
- End-User Education: Train and remind your users to be cautious of suspicious files from untrusted sources, including uncommon file types like themes.





