CVE-2024-21326 (CVSS 9.6): One Click Could Compromise Microsoft Edge

Microsoft has released a security update for its browser, Microsoft Edge, addressing vulnerabilities revealed in Chromium and implementing its unique fixes. Following the release of Chromium 121.0.6167.85/.86, Microsoft unveiled MS Edge 121.0.2277.83 based on these versions.
In Chromium, 11 vulnerabilities were rectified based on CVE identifiers. Additionally, six unique vulnerabilities specific to MS Edge were also addressed.
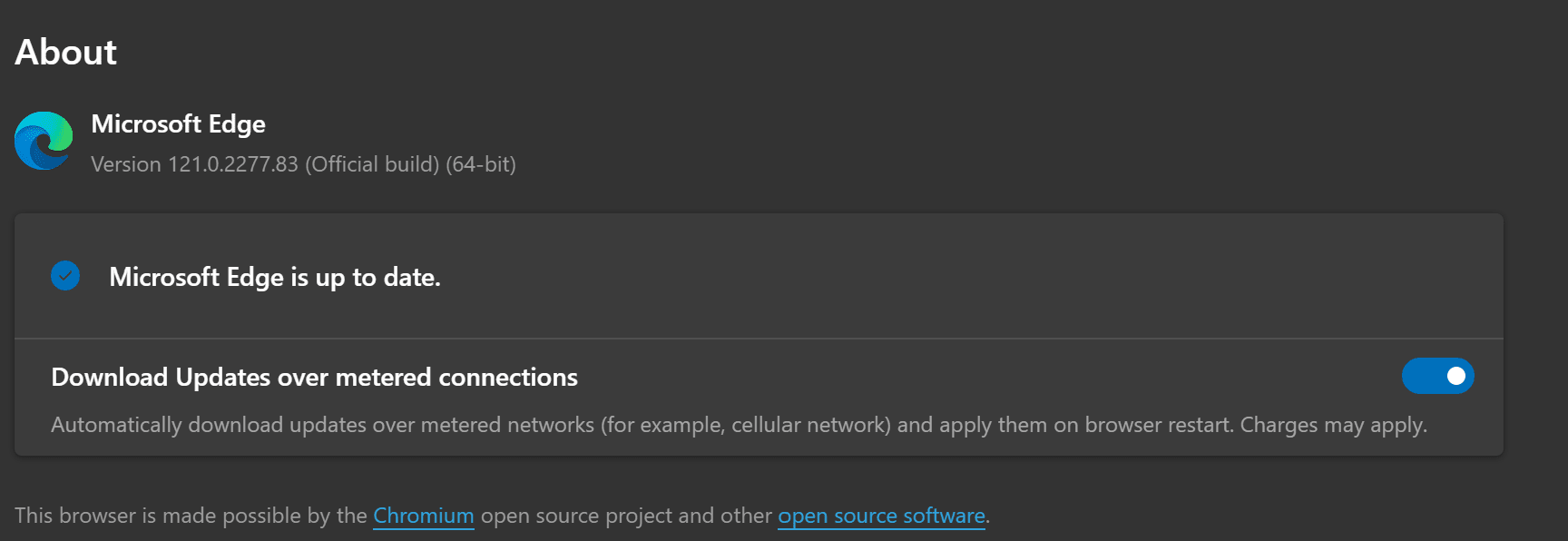
The privilege escalation vulnerabilities CVE-2024-21326 and CVE-2024-21385 were rated as ‘Important.’ Their respective base scores in the CVSSv3.1 are 9.6 and 8.3.
“In a web-based attack scenario, an attacker could host a website (or leverage a compromised website that accepts or hosts user-provided content) that contains a specially crafted file that is designed to exploit the vulnerability. However, an attacker would have no way to force the user to visit the website. Instead, an attacker would have to convince the user to click a link, typically by way of an enticement in an email or Instant Messenger message, and then convince the user to open the specially crafted file,” Microsoft explains in the CVE-2024-21326 description.
“Successful exploitation of this vulnerability could lead to a full compromise of the browser,” the company added.
Moreover, two vulnerabilities each with a severity of Moderate and Low were resolved. The vulnerabilities corrected in Microsoft Edge 121.0.2277.83 are as follows. A new extended stable version, Microsoft Edge 120.0.2210.160, has also been made available:
- High CVE-2024-0807: Use after free in WebAudio. Reported by Huang Xilin of Ant Group Light-Year Security Lab on 2023-11-25
- High CVE-2024-0812: Inappropriate implementation in Accessibility. Reported by Anonymous on 2023-09-19
- High CVE-2024-0808: Integer underflow in WebUI. Reported by Lyra Rebane (rebane2001) on 2023-11-24
- Medium CVE-2024-0810: Insufficient policy enforcement in DevTools. Reported by Shaheen Fazim on 2023-10-26
- Medium CVE-2024-0814: Incorrect security UI in Payments. Reported by Muneaki Nishimura (nishimunea) on 2023-07-11
- Medium CVE-2024-0813: Use after free in Reading Mode. Reported by @retsew0x01 on 2023-08-30
- Medium CVE-2024-0806: Use after free in Passwords. Reported by 18楼梦想改造家 on 2023-11-25
- Medium CVE-2024-0805: Inappropriate implementation in Downloads. Reported by Om Apip on 2024-01-01
- Medium CVE-2024-0804: Insufficient policy enforcement in iOS Security UI. Reported by Narendra Bhati of Suma Soft Pvt. Ltd. Pune (India) on 2024-01-03
- Low CVE-2024-0811: Inappropriate implementation in Extensions API. Reported by Jann Horn of Google Project Zero on 2023-10-21
- Low CVE-2024-0809: Inappropriate implementation in Autofill. Reported by Ahmed ElMasry on 2023-10-31
- Low CVE-2024-21383: Microsoft Edge (Chromium-based) Spoofing Vulnerability
- Moderate CVE-2024-21382: Microsoft Edge for Android Information Disclosure Vulnerability
- Moderate CVE-2024-21387: Microsoft Edge for Android Spoofing Vulnerability
- Low CVE-2024-21336: Microsoft Edge (Chromium-based) Spoofing Vulnerability