CVE-2024-21633: The Critical Flaw in Apktool and How to Mitigate It
In the intricate world of Android application development, tools like Apktool have been indispensable for developers and reverse engineers. Apktool, known for its ability to reverse engineer third-party, closed binary Android apps, has hit a stumbling block that exposes users to significant security risks.
Recently identified with the CVE identifier CVE-2024-21633 and scored 7.8 on the CVSS scale, this vulnerability is a glaring example of the risks associated with software tooling. The core issue lies in Apktool’s method of handling resource files during the decoding process.
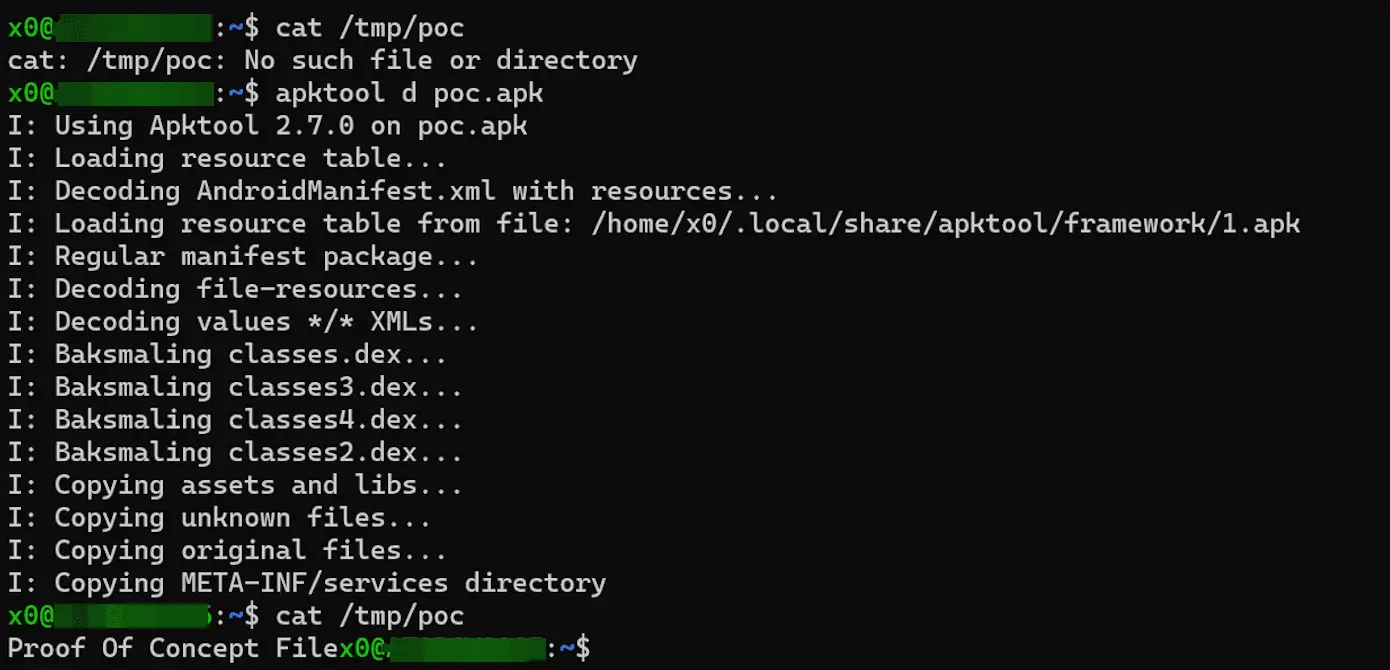
Apktool infers the output path of resource files based on their names, following the pattern [output-dir]/res/[type]/[resource-name]+[extension of (resource-file)]. For instance, a resource named “foo” with the path “res/raw/bar” would typically be extracted to res/raw/foo. However, the catch is that Apktool never sanitizes the resource name. Consequently, altering the resource name to something like “../../../../../../../../../../../../tmp/poc” results in the “res/raw/bar” file being placed in the /tmp/poc directory in Linux systems. The vulnerability also exists in Windows and potentially in macOS, though it hasn’t been explicitly confirmed for the latter.
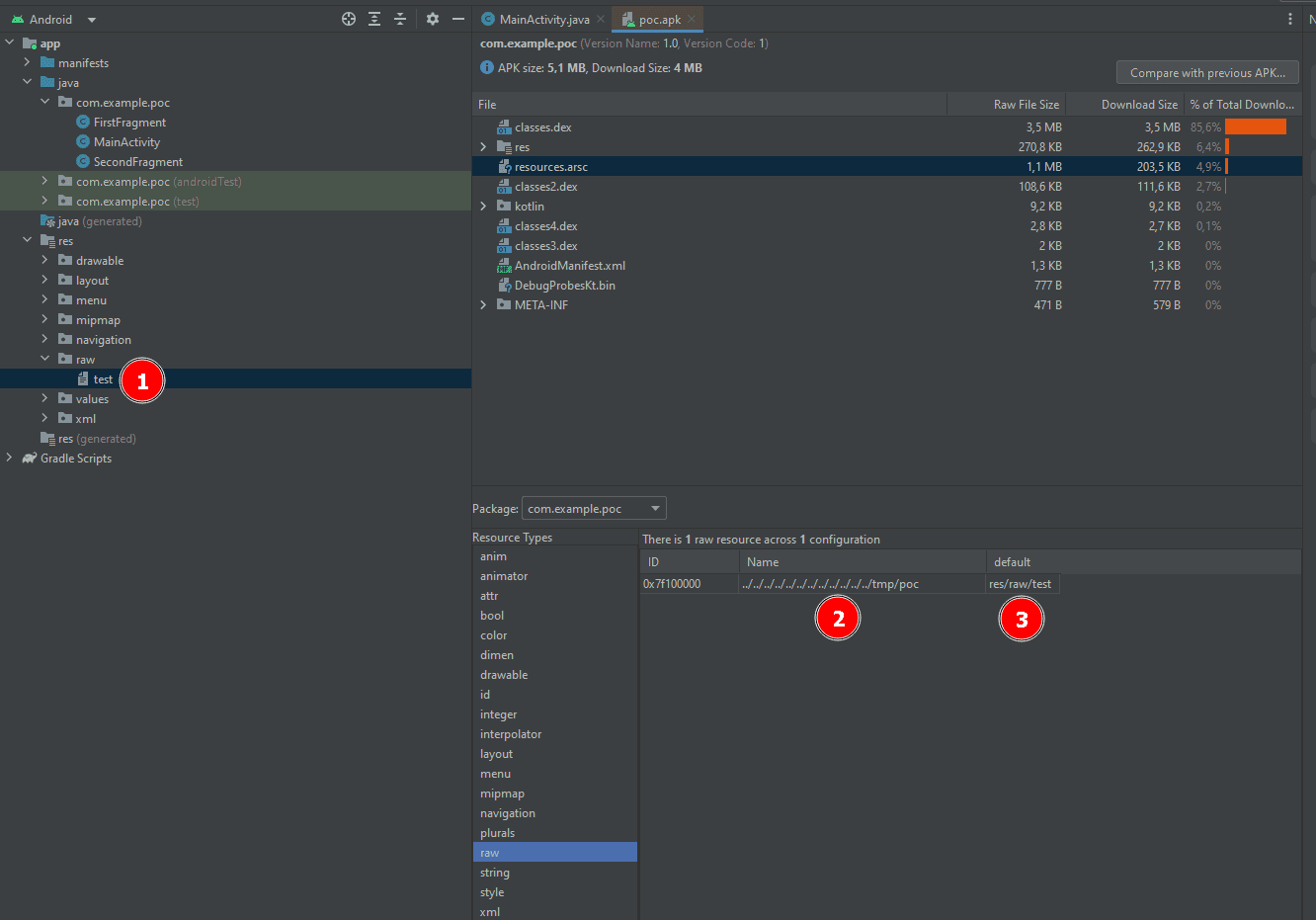
Generate Payload
This vulnerability allows an attacker to write or overwrite any file to which the user has access. Under certain conditions, this could even extend to critical system files like shell init files or authorized keys. Notably, an APK may contain up to 65535 raw resources, providing attackers ample opportunity to brute-force their way to a target file.

PoC
CVE-2024-21633 impacts Apktool versions up to and including 2.9.1. However, the good news is that this issue has been patched in version 2.9.2. Users of Apktool are strongly advised to update to this latest version to safeguard against potential exploitation.
For developers and reverse engineers relying on Apktool, updating to version 2.9.2 is not just recommended, it’s essential to ensure the security and integrity of their work.





