CVE-2024-22734 – Critical Flaw in Trux Software: Hackers Can Take Over Systems
Security researchers at Redline Cyber Security have revealed a severe security flaw (CVE-2024-22734) within Trux, a widely used waste management ERP software suite developed by AMCS Group. This vulnerability could allow attackers with local network access to take complete control of the application and gain unrestricted access to sensitive ERP databases.
The Flaw:
The heart of the problem lies in the Trux software’s use of a static, hard-coded AES encryption key and Initialization Vector (IV) pair. AES is a robust encryption standard when implemented correctly, but hard-coding the key and IV means that the same cryptographic values are used across every installation of Trux, regardless of the client’s specific environment.
This creates a predictable vulnerability. Anyone with access to the Trux program files could reverse engineer the encryption process, ultimately decrypting essential application secrets – including the credentials used to connect to the backend database. With those credentials in hand, an attacker would have a direct path into potentially sensitive client data.
Discovery:
The security issue was initially uncovered during a routine penetration test performed by Redline Cyber Security for a client utilizing the Trux software. Security analysts noted the predictable encryption implementation and lack of secure key storage.
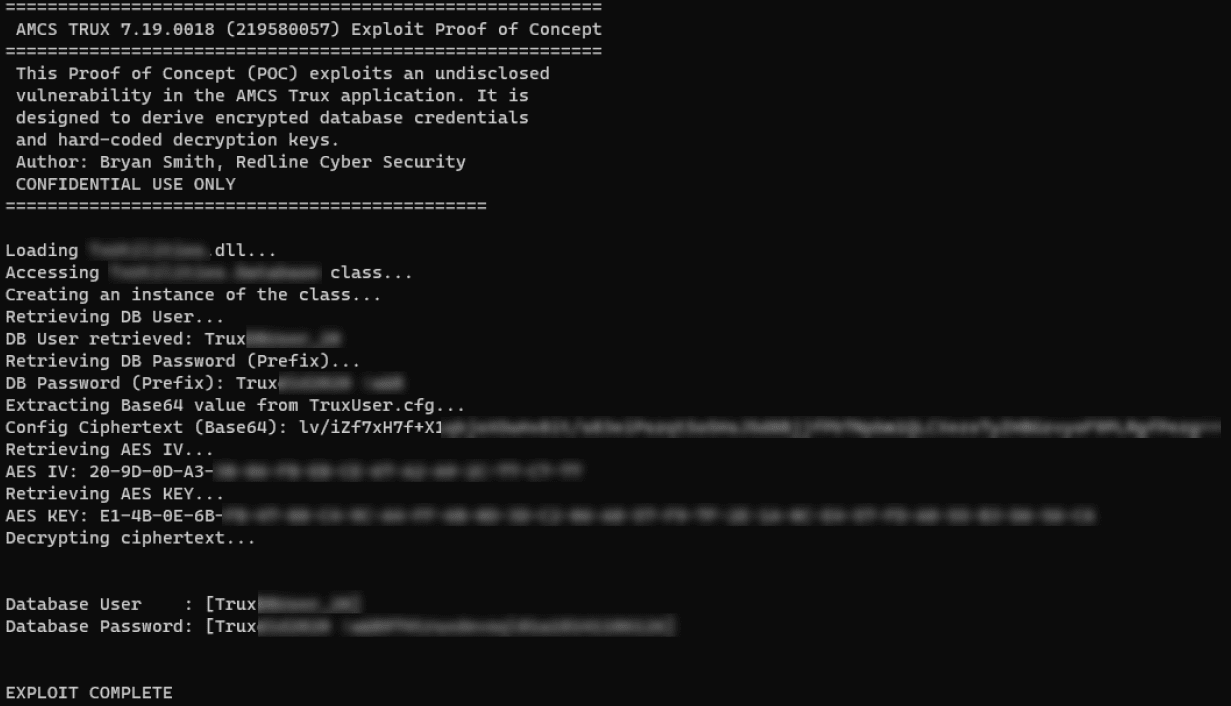
The flaw was pinpointed through meticulous assembly analysis and debugging of the Trux software. Utilizing tools like dnSpy, a .NET application decompiler, and Procmon, researchers tracked how the application processed encrypted configuration files upon launch. The TruxUser.cfg configuration file, in particular, was found to contain encrypted strings essential for database connectivity. By reverse-engineering the software’s assemblies, Redline’s team discovered that a hard-coded prefix was embedded within the application code, which remained constant despite changes to the encrypted configuration.

Image: Redline Cyber Security
Exploitation of CVE-2024-22734 involved leveraging C# reflection to bypass access controls and inspect internal structures of the TxUtilities.dll assembly. This process enabled the researchers to dynamically load the assembly and access private fields containing the critical AES Key and IV. The exposed cryptographic keys allowed the decryption of the cipher-text from the configuration file, revealing the full database credentials used by the Trux software.
The Risk:
- Data Compromise: An attacker could potentially intercept and decrypt communications between the Trux client and database, revealing sensitive waste management operational data.
- Further Exploitation: The exposed database credentials could be leveraged to access additional corporate systems or networks, increasing the scope of the attack.
- Reputational Damage: A data breach resulting from this vulnerability could lead to lost client trust, regulatory fines, and financial losses for any organization utilizing Trux.
Call to Action
AMCS Group has released a security update that addresses the vulnerability. Redline Cyber Security and AMCS Group strongly urge Trux clients to apply the patch immediately to protect their systems and data.





