CVE-2024-25089: RCE Risk in Malwarebytes Binisoft Windows Firewall Control
Recently, two security vulnerabilities have been identified in Malwarebytes Binisoft Windows Firewall Control, a widely-used tool that enhances the capabilities of the Windows Firewall. These vulnerabilities tracked as CVE-2024-25089 and CVE-2023-36631, pose significant risks to users and their systems.
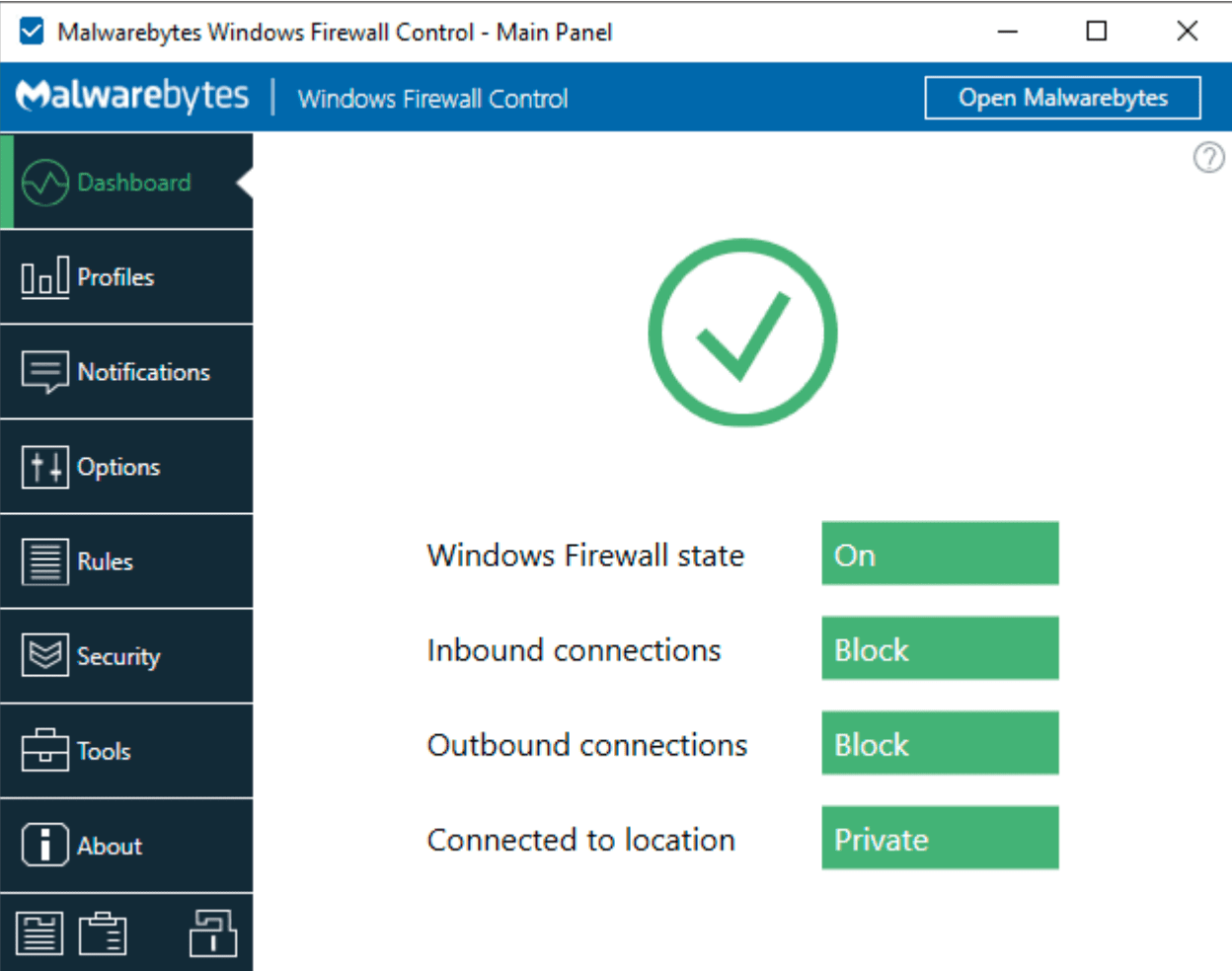
Malwarebytes Binisoft Windows Firewall Control Overview

Malwarebytes Binisoft Windows Firewall Control extends the features of the native Windows Firewall, providing users with enhanced control and additional functionalities. It simplifies firewall management, allowing users to make quick adjustments without navigating through the intricacies of the Windows Firewall interface.
CVE-2024-25089: Remote Code Execution Vulnerability
CVE-2024-25089 is a critical security vulnerability discovered in Malwarebytes Binisoft Windows Firewall Control before version 6.9.9.2. This vulnerability allows remote attackers to execute arbitrary code through gRPC named pipes. While specific technical details have not been disclosed to the public, the potential implications of remote code execution are alarming.
Remote code execution vulnerabilities provide malicious actors with the capability to take control of a system from a distance, potentially leading to data theft, system compromise, and other severe consequences. The ability for attackers to exploit this vulnerability poses a significant threat to individuals and organizations relying on the Windows Firewall Control tool.
CVE-2023-36631: Bypassing Windows Firewall Restrictions
Another vulnerability tracked as CVE-2023-36631, was addressed in version 6.9.9.2 of Malwarebytes Binisoft Windows Firewall Control. This vulnerability allows local unprivileged users to bypass Windows Firewall restrictions via the user interface’s rules tab. The root cause of this vulnerability was the lack of access control in the wfc.exe component of the software.
The implications of this vulnerability are particularly concerning, as it enables local users to bypass security measures that are meant to protect the system from unauthorized access. This could potentially lead to unauthorized access to sensitive data, escalation of privileges, and further exploitation of the compromised system.
Reporting and Disclosure
Both CVE-2024-25089 and CVE-2023-36631 were reported via the HackerOne platform [1, 2], a trusted venue for security researchers and white-hat hackers to report vulnerabilities to software vendors. However, at the time of writing, detailed information about these vulnerabilities has not been made public, highlighting the importance of responsible disclosure.





