CVE-2024-27135: Apache Pulsar Remote Code Execution Vulnerability
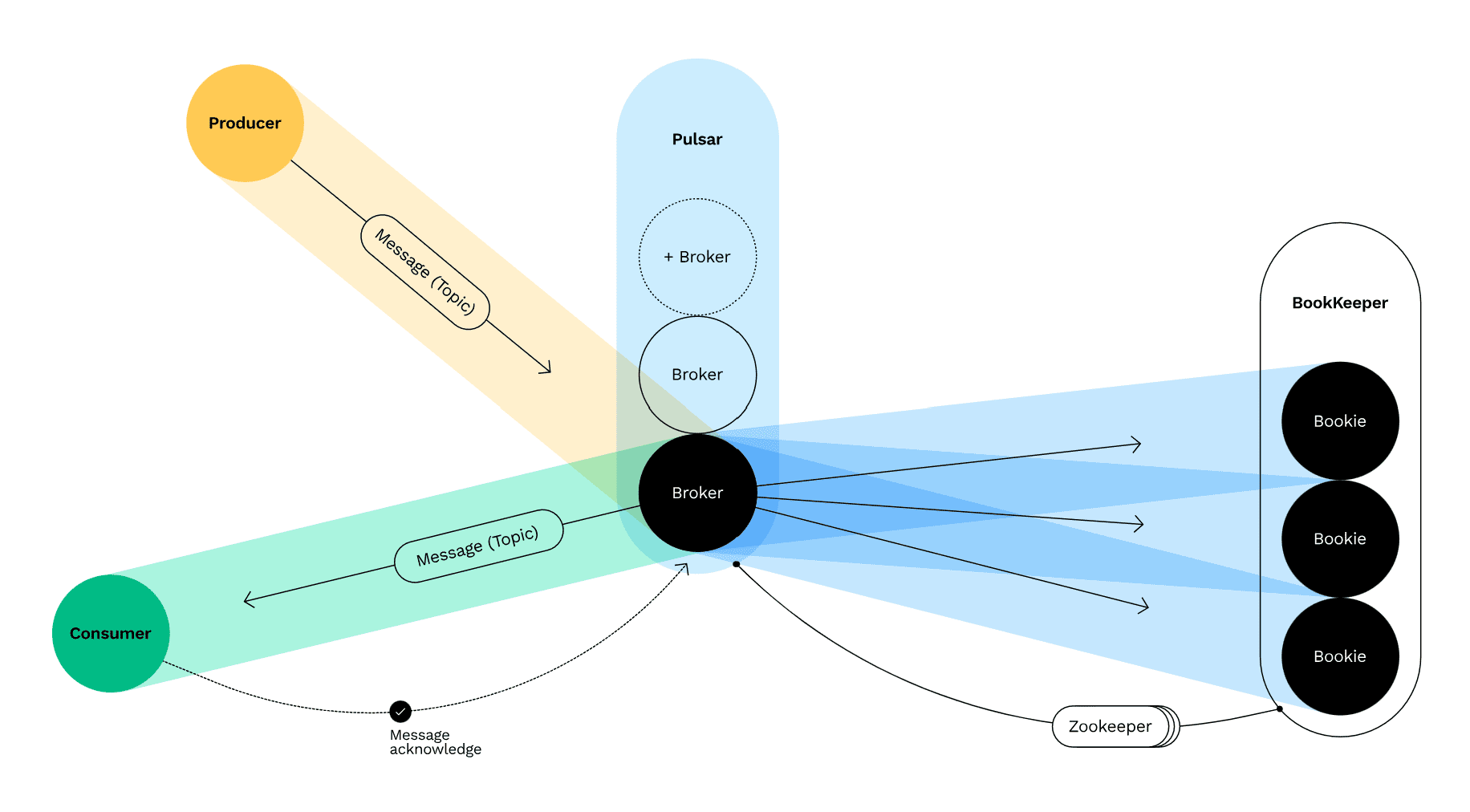
The Apache Software Foundation has released urgent patches for Apache Pulsar, its versatile messaging and streaming platform. These security updates address five vulnerabilities, including potential remote code execution, unauthorized data access, and improper authentication issues. Organizations and individuals utilizing Apache Pulsar must prioritize installing these patches as soon as possible to mitigate significant risks.
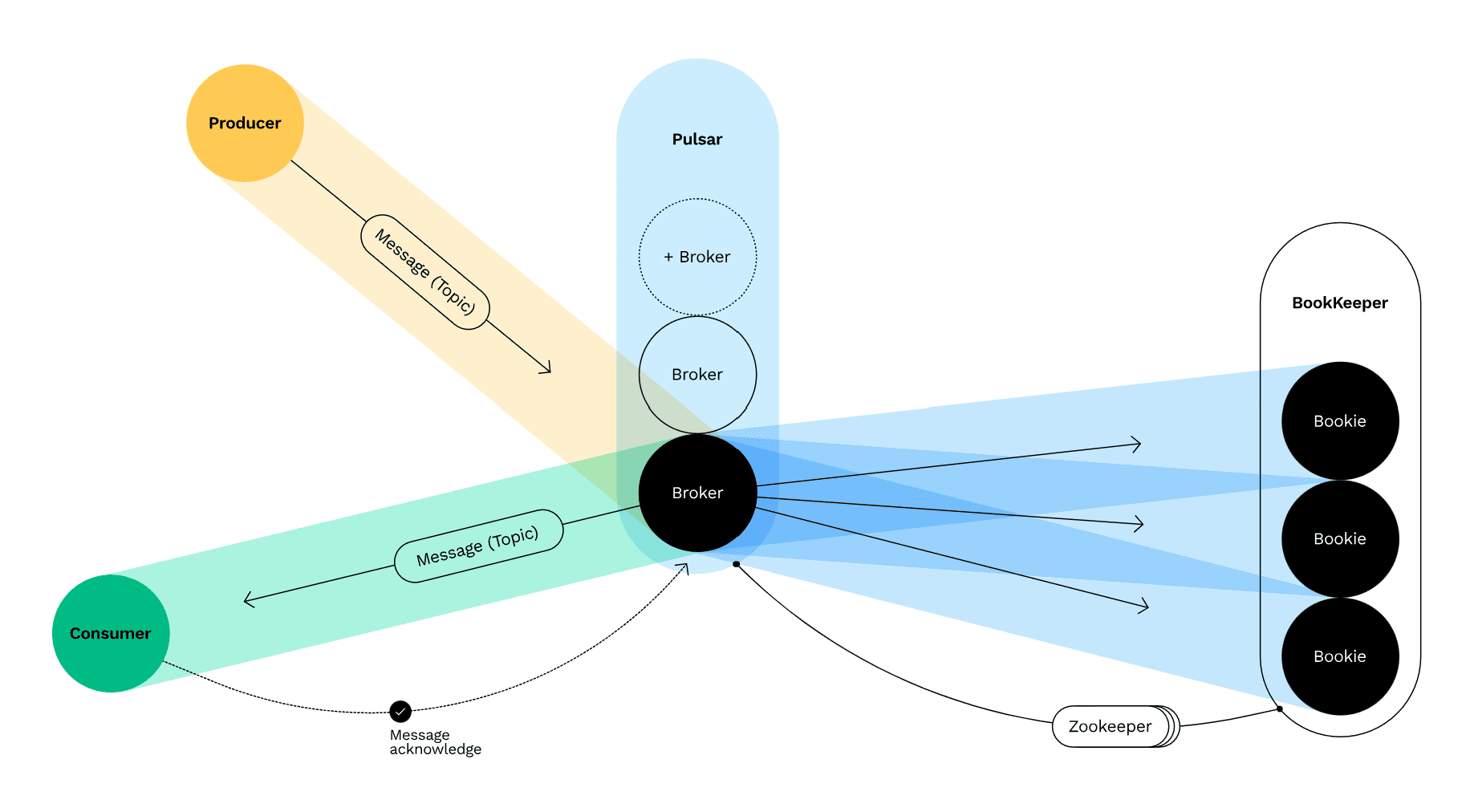
Vulnerabilities in Detail
-
CVE-2022-34321: Proxy Statistics Endpoint Exposed
An improper authentication flaw allows attackers to connect to the Pulsar Proxy’s /proxy-stats endpoint without authorization. This could reveal sensitive connection statistics and potentially allow denial-of-service attacks by manipulating logging levels. Affected versions range from 2.6.0 to 3.1.0 across different releases. -
CVE-2024-27135: Remote Code Execution in Functions Worker
Input validation weaknesses permit authenticated users to execute code on a Pulsar Function Worker or Broker configured with Functions enabled. This vulnerability also affects the Pulsar Broker under certain configurations, affecting versions from 2.4.0 to 3.2.0. CVE-2024-27135 is marked as a high-severity flaw. -
CVE-2024-27317: Directory Traversal in File Extraction
Maliciously crafted uploaded jar or nar files could exploit this vulnerability, allowing attackers to modify files outside the intended location. This issue also extends to the Pulsar Broker when configured to enable the Functions Worker, affecting versions from 2.4.0 to 3.2.0. -
CVE-2024-27894: Unauthorized File Access and HTTP(S) Proxying
A vulnerability in the Pulsar Functions Worker could allow attackers to access arbitrary files readable by the process and use the Worker as a proxy for HTTP/HTTPS requests. This flaw is present in versions from 2.4.0 to 3.2.0. -
CVE-2024-28098: Topic-Level Policy Modification Loophole
Users with only produce or consume permissions could modify topic-level configuration like retention and offloading policies. This security lapse affects versions from 2.7.1 to 3.2.0.
Mitigation
To address these vulnerabilities, upgrades to specific Pulsar versions have been recommended. For instance, users of the 2.10 Pulsar Proxy should upgrade to at least version 2.10.6, while those on the 3.1 Pulsar Function Worker should move to version 3.1.3 or newer. Crucially, remember that the Apache Pulsar Proxy should not be exposed directly to the internet and operate within a secure network.
Additional Considerations
The updated Pulsar Functions Worker restricts the creation of functions using URLs by default. Users who depend on this feature can enable it with granular control using the “additionalEnabledConnectorUrlPatterns” and “additionalEnabledFunctionsUrlPatterns” configuration keys.
Call to Action
Rapidly applying these security patches is essential to safeguard your Apache Pulsar deployments. Failure to update could leave your systems and data exposed to substantial cyber threats.





