CVE-2024-31819: Critical Flaw in Popular Video Platform AVideo Could Allow Full System Takeover

Security researchers are sounding the alarm about a dangerous new critical vulnerability uncovered within the popular open-source video platform, AVideo. This vulnerability, designated as CVE-2024-31819, lies within the platform’s WWBNIndex plugin and has the alarming potential to allow a remote attacker to seize complete control of vulnerable systems.

Understanding the Threat: What Makes This Vulnerability So Dangerous
- Remote Code Execution (RCE): At its core, this flaw grants attackers the frightening ability to execute any malicious code they choose on affected AVideo servers. This opens the door to a wide array of destructive scenarios, including data theft, malware installation, and the use of compromised servers as launchpads for further attacks within a network.
- AVideo’s Reach: A Larger Attack Surface: AVideo’s popularity and widespread adoption mean thousands of platforms could be vulnerable. This translates to a massive potential impact should attackers weaponize this exploit on a large scale.
- The Ease of Exploitation: Threat actors don’t need any special permissions or authentication to take advantage of the vulnerability. This drastically lowers the barrier to entry, increasing the likelihood of exploitation attempts.
Proof of Concept and Exploit Tools
For those interested in the technical details, the vulnerability is classified as a Remote Code Execution (RCE) vulnerability. It’s located specifically within AVideo’s WWBNIndex plugin.
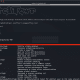
The severity of this vulnerability is underscored by the existence of a readily available Proof of Concept (PoC). This PoC provides a blueprint demonstrating how easy it could be to exploit the flaw. Security researchers have even developed tools, like a Metasploit module and a Python exploit script, specifically tailored to CVE-2024-31819. While initially intended for research purposes, these tools could also be misused by malicious actors.
Experts have shared exploit tools and details to aid further research:
- Metasploit Module: A module within the popular Metasploit framework could make exploitation easier for attackers.
- Python Exploit Script: Researchers have provided a script demonstrating the exploit
What Can You Do?
- Patch Immediately: If you use AVideo, your top priority is to check for an official patch from the developers and apply it the moment it’s released.
- Temporary Measures: If a patch isn’t immediately available and your AVideo instance is critical, strongly consider isolating the server from sensitive parts of your network. If at all possible, taking the platform offline temporarily is the safest option until patched.