CVE-2024-34082: Grav CMS Vulnerability Opens Door to Account Takeovers
Grav, a popular open-source content management system (CMS) known for its speed and flexibility, has a critical security flaw that could expose websites to malicious account takeovers and unauthorized access to sensitive files.
The Vulnerability: CVE-2024-34082
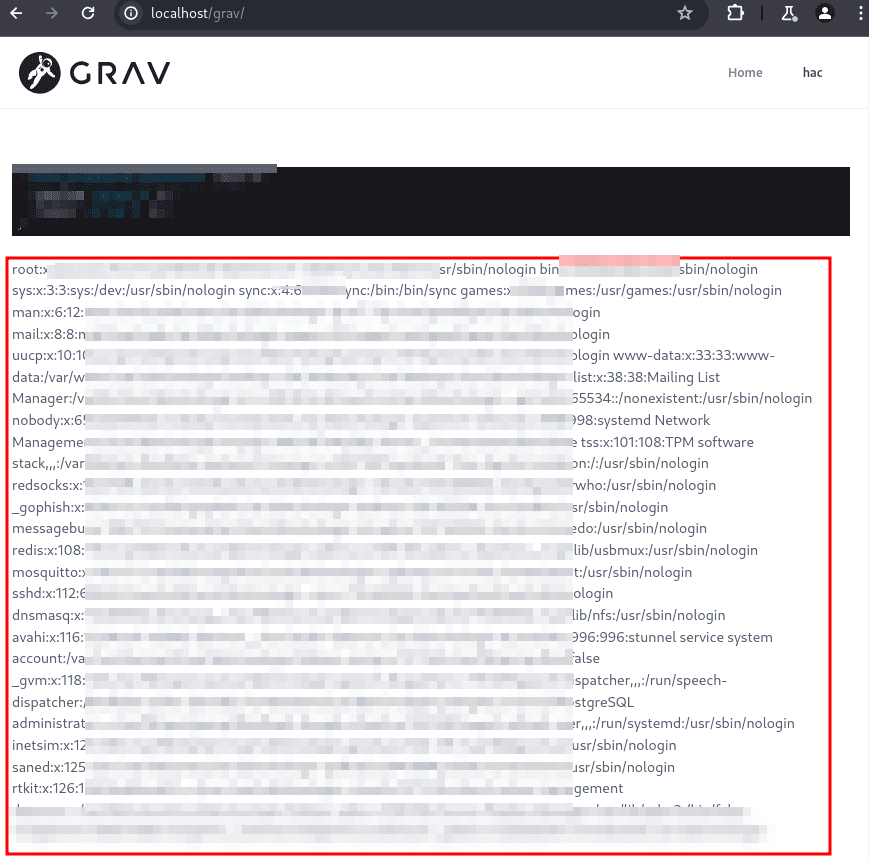
Tracked as CVE-2024-34082 (CVSS 8.5), the vulnerability stems from Grav’s use of the Twig templating engine. Security researcher Riyush Ghimire discovered that users with low-level privileges, such as the ability to edit pages, could exploit this flaw to read arbitrary files on the server. This includes Grav’s user account files, which store hashed passwords, two-factor authentication secrets, and password reset tokens.
Impact: Full Account Takeover and Data Exposure
Armed with this information, attackers can:
- Hijack Any Account: Take over any user account on the website, including those with administrative privileges, granting them complete control.
- Access Sensitive Files: Read any file on the server, potentially exposing confidential data, configuration details, or even source code.
Proof of Concept Demonstrates Severity

Ghimire provided a proof-of-concept exploit that demonstrates how easily an attacker can read the authentication details of a Grav administrator simply by inserting a specific Twig syntax into a page. This highlights the severity of the vulnerability and the urgency for website owners to take action.
Affected Versions and Patch
All Grav versions prior to 1.7.46 are vulnerable. The issue has been patched in version 1.7.46, and all users are strongly urged to update immediately.
Recommendations for Grav Users:
- Upgrade to 1.7.46: Immediately update Grav to the latest version to mitigate the risk.
- Review User Permissions: Carefully assess the permissions granted to users, ensuring that only trusted individuals have access to sensitive functions.
- Monitor for Suspicious Activity: Be vigilant for any unusual activity on your website, such as unauthorized changes to content or user accounts.





