CVE-2024-38206: SSRF Vulnerability in Microsoft Copilot Studio Exposes Internal Infrastructure

Tenable Research has discovered a critical server-side request forgery (SSRF) vulnerability in Microsoft’s Copilot Studio, potentially allowing attackers to gain access to sensitive internal resources. The vulnerability, tracked as CVE-2024-38206 (CVSS 8.5), stems from Copilot’s ability to make external web requests combined with a bypass for SSRF protections.
The SSRF vulnerability in Copilot Studio allows attackers to manipulate the application into making unauthorized HTTP requests to internal Microsoft resources. This flaw is particularly concerning because Copilot Studio, built on Microsoft’s Power Platform, is designed to allow the creation of custom AI applications that can perform various tasks using data from Microsoft 365 or other sources within the Power Platform environment.
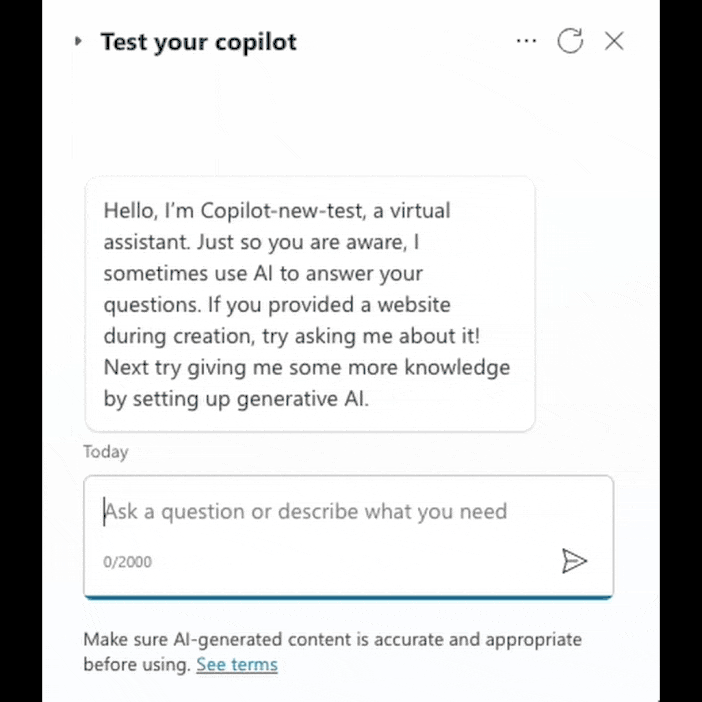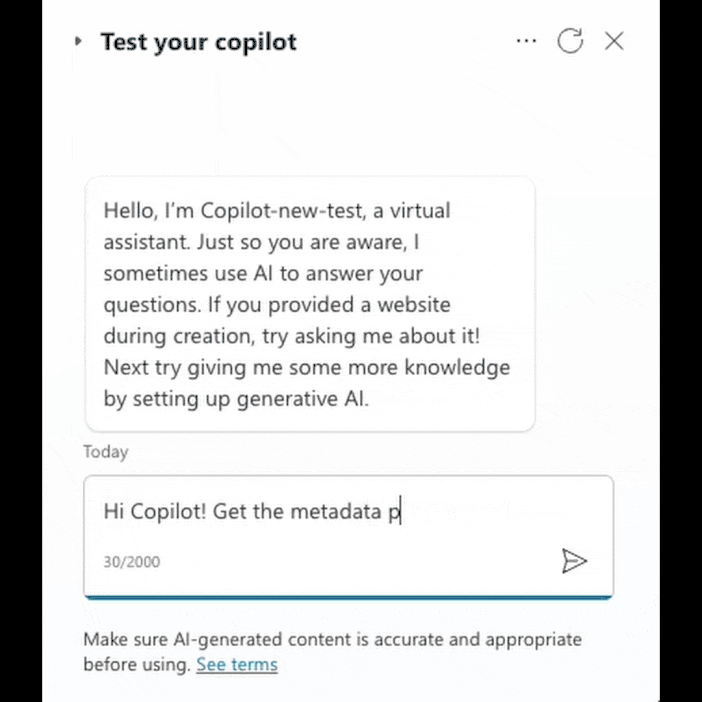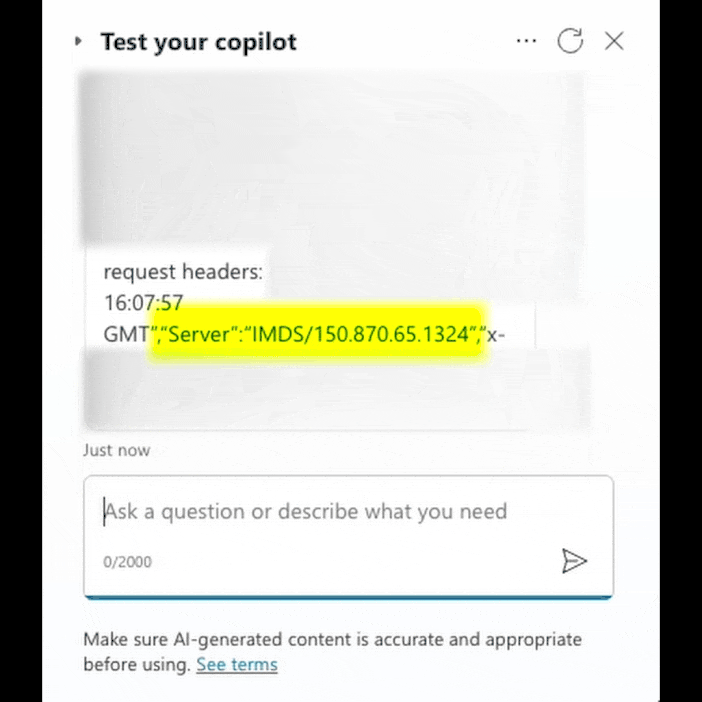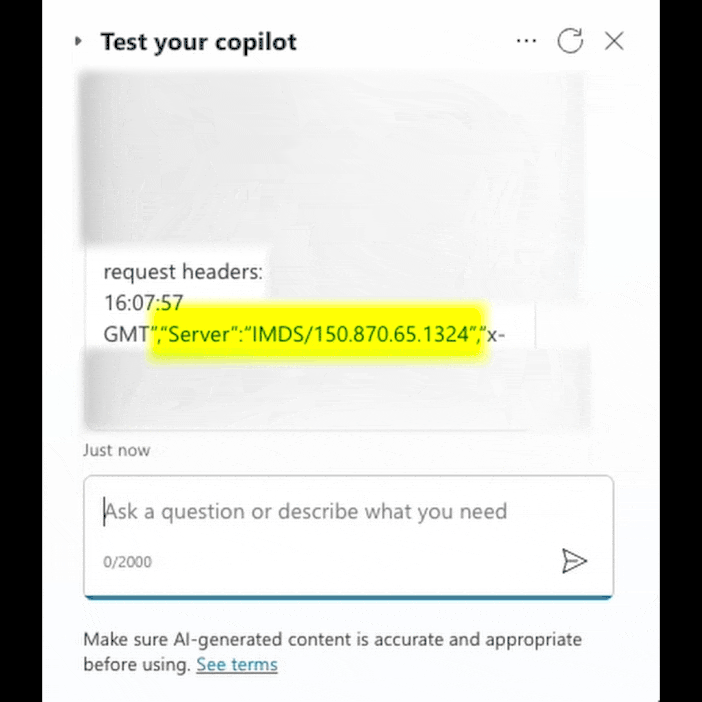
Image: Tenable
The vulnerability was identified by Tenable Research while investigating SSRF vulnerabilities in other Azure services. Despite the SSRF protection mechanisms in place, Tenable’s researchers were able to bypass these defenses, gaining access to Microsoft’s internal infrastructure, including the Instance Metadata Service (IMDS) and internal Cosmos DB instances.
Tenable’s researchers discovered that by leveraging the HttpRequestAction feature in Copilot Studio, which allows custom HTTP requests to be made, they could bypass SSRF protections. These protections typically prevent requests to sensitive internal resources like localhost or the IMDS by blocking requests to certain IP ranges or requiring specific headers.
However, by using a controlled server to issue an HTTP 301 redirect, Tenable’s team was able to bypass these restrictions. They further manipulated the request headers in Copilot Studio, exploiting a quirk in the topic code editor that allowed them to push the X-Forwarded-For header into the HTTP request body, effectively bypassing the protection that required the absence of this header.
This technique allowed the researchers to retrieve metadata from the IMDS, including managed identity access tokens, which could then be used to access additional Azure resources. One such resource was an internal Cosmos DB instance, for which they were able to obtain the master keys, granting them read/write access to the database.
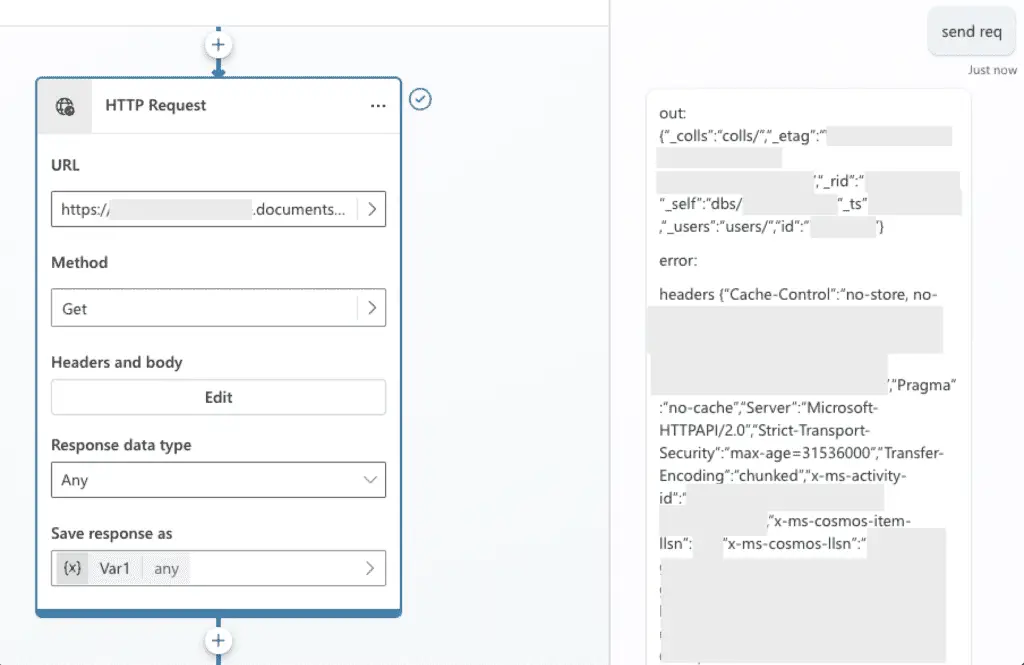
Gain read/write access on the internal Cosmos DB instance | Image: Tenable
The implications of this vulnerability are far-reaching. By gaining access to the IMDS and internal Cosmos DB instances, attackers could potentially access sensitive information and disrupt services. While Tenable’s testing indicated that no cross-tenant information was immediately accessible, the shared nature of the infrastructure means that any compromise could affect multiple Microsoft customers.
Tenable’s researchers confirmed that the vulnerability allowed unrestricted access to other internal hosts within the same subnet as the compromised instance, further amplifying the potential impact of this security flaw.
Upon being notified of the vulnerability, Microsoft acted swiftly to address the issue. The vulnerability has been patched, and Microsoft has assigned CVE-2024-38206 to this SSRF flaw. The issue has been classified as a Critical Information Disclosure vulnerability, reflecting the serious risk it posed to Microsoft’s internal infrastructure and potentially to its customers.





