CVE-2024-39091: Critical Vulnerability in MIPC Camera Framework Puts Millions at Risk
A high-severity vulnerability (CVE-2024-39091, CVSS 8.8) has been discovered in the MIPC camera framework, a widely-used software platform for home security cameras. This vulnerability could allow attackers to gain complete control of affected cameras, putting users’ privacy and security at risk.
The MIPC Camera Framework, developed by MIPC Technology Co., LTD / Shenzhen Fujikam Industry Development, is commonly integrated into various security camera brands, including ANNKE, SANNCE, INKERSCOOP, KAMEP, and COOAU. The framework hosts an HTTP service on port 80, facilitating communication between the camera and other devices, such as smartphone apps, via a proprietary protocol.
However, researchers discovered that one of the functions provided by this service processes user input without requiring authentication and fails to perform proper input validation. The vulnerability resides in the ccm_debug_m function, which invokes OS shell commands using user-controlled input. Due to the lack of validation and running under root privileges, an attacker could exploit this flaw to inject and execute arbitrary commands on the underlying Linux OS.
While the CVE-2024-39091 vulnerability was initially identified in the Annke Crater 2 camera, the MIPC framework is used by numerous other camera manufacturers. Popular brands like SANNCE, INKERSCOOP, KAMEP, and COOAU are potentially affected, leaving millions of users vulnerable.
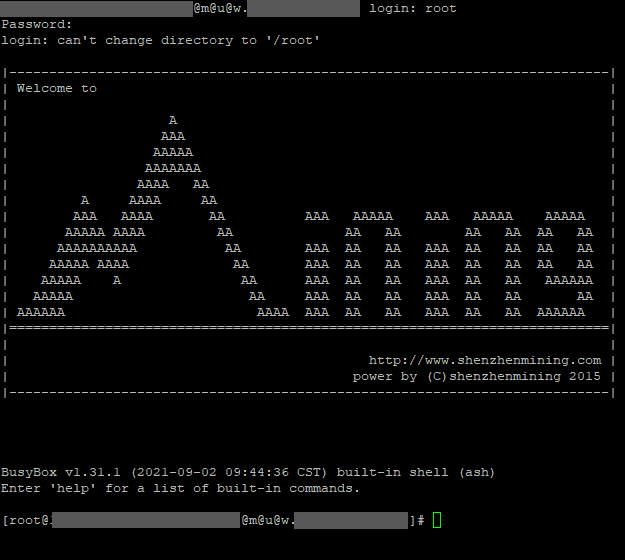
By crafting a malicious HTTP request that invokes the ccm_debug_m function, an attacker could change the root password and start a telnet service, gaining full access to the device’s root console. This level of access could enable further attacks, including unauthorized surveillance, manipulation of camera feeds, and compromising the security of the entire network.
The vulnerability was responsibly disclosed to both Annke and MIPC support teams, who responded promptly and professionally. However, as of now, no official patch or mitigation has been released by MIPC / Fujikam to address this issue.
If you own a camera from any of the mentioned brands, check with the manufacturer for firmware updates that address this vulnerability.





