CVE-2024-4215 & CVE-2024-4216: Security Flaws Patched in Popular PostgreSQL Tool pgAdmin
pgAdmin, renowned as the leading open-source administration and development platform for PostgreSQL, the world’s most advanced open-source database, recently addressed two significant security vulnerabilities. These vulnerabilities, identified in versions up to and including 8.5, posed serious risks to users by potentially allowing unauthorized actions and script executions within the application. The flaws, tracked as CVE-2024-4215 and CVE-2024-4216, both carried a severity rating of 7.4 on the CVSS.
CVE-2024-4215: Authentication Bypass Flaw
Rated as high-severity, this vulnerability presents a serious risk. Attackers could exploit this flaw to completely bypass multi-factor authentication (MFA), a crucial security measure designed to prevent unauthorized access. Even if you’ve diligently implemented MFA, older pgAdmin versions remain exposed. With just a user’s login information, attackers could gain control of the pgAdmin instance, manipulating data, exfiltrating sensitive information, and potentially launching further attacks.
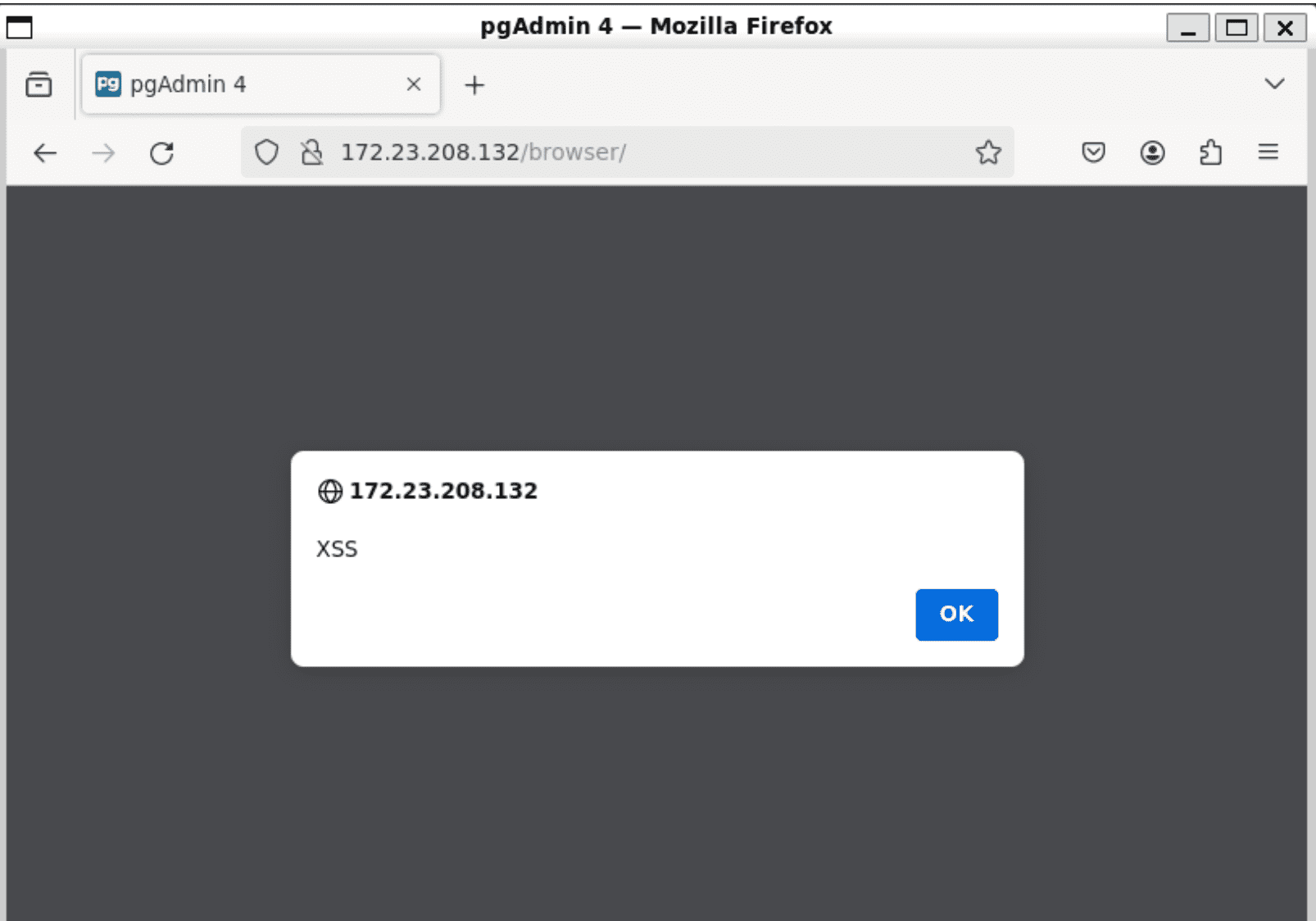
CVE-2024-4216: Cross-Site Scripting (XSS) Vulnerability
Also carrying a high-severity rating, this vulnerability lies within pgAdmin’s settings API. If exploited, an attacker could inject malicious code that executes in the victim’s browser.
The reproduction of the XSS vulnerability involved the following steps:
- Utilizing a man-in-the-middle proxy like mitmproxy.
- Intercepting the POST request to /settings/store.
- Modifying the request body to include malicious JavaScript code (
... \"children\": [{\"id\":\"+3'-alert('XSS')-'\", ...). - Reloading the pgAdmin homepage to trigger the script execution.

Image: felixtoe
Critical Action: Update to pgAdmin 8.6
Both vulnerabilities were resolved with the release of pgAdmin version 8.6. Users of pgAdmin are strongly advised to update to the latest version to protect against the potential exploitation of these vulnerabilities. As always, maintaining updated software is crucial in safeguarding against known security threats.
Beyond Updates: Proactive Security for PostgreSQL Environments
Software patches are essential, but a robust security posture requires a multi-layered approach. Consider these additional best practices:
- Strong Password Policies: Mandate complex passwords for pgAdmin, and consider a password manager for users.
- Principle of Least Privilege: Grant users and applications only the permissions necessary for their functions.
- Regular Auditing: Conduct security audits to identify potential vulnerabilities and misconfigurations.
- Network Segmentation: Limit the potential impact of a breach by isolating sensitive systems.
- Incident Response Plan: Have a plan in place to respond effectively to security incidents.





