CVE-2024-43044: Critical Jenkins Vulnerability Exposes Servers to RCE, PoC Exploit Published
A security researcher from Conviso Labs published the technical details and a proof-of-concept (PoC) exploit for a critical CVE-2024-43044 vulnerability in Jenkin.
Jenkins is integral to many development pipelines, making it a prime target for attackers. If compromised, Jenkins servers can become a launchpad for widespread damage, including credential theft, unauthorized code modifications, and disrupted deployments. The newly disclosed CVE-2024-43044 vulnerability exemplifies the severity of such risks.
CVE-2024-43044 is classified as an arbitrary file read vulnerability, which allows an agent to read files from the Jenkins controller. The root cause lies in the Jenkins feature that permits the controller to transmit JAR files to its agents. The vulnerability exists because the ClassLoaderProxy#fetchJar method, invoked on the controller, fails to restrict the file paths that agents can request. This lack of restriction enables unauthorized file access on the controller’s file system.
The researchers from Conviso Labs have provided a detailed breakdown of how this vulnerability can be exploited. The exploitation process begins by leveraging the hudson.remoting.RemoteClassLoader, which loads class files from a remote peer via a channel. Through this, the attacker accesses a Proxy object within the RemoteClassLoader, linked to a hudson.remoting.RemoteInvocationHandler. This handler then invokes the fetchJar method, triggering a Remote Procedure Call (RPC) to the controller.
On the controller side, the vulnerability is further exposed as the fetchJar method reads resources without validating the user-controlled URL. This critical oversight allows an attacker to bypass the Agent -> Controller Access Control system—a security feature designed to prevent unauthorized agent access to the controller, which has been active by default since Jenkins version 2.326.
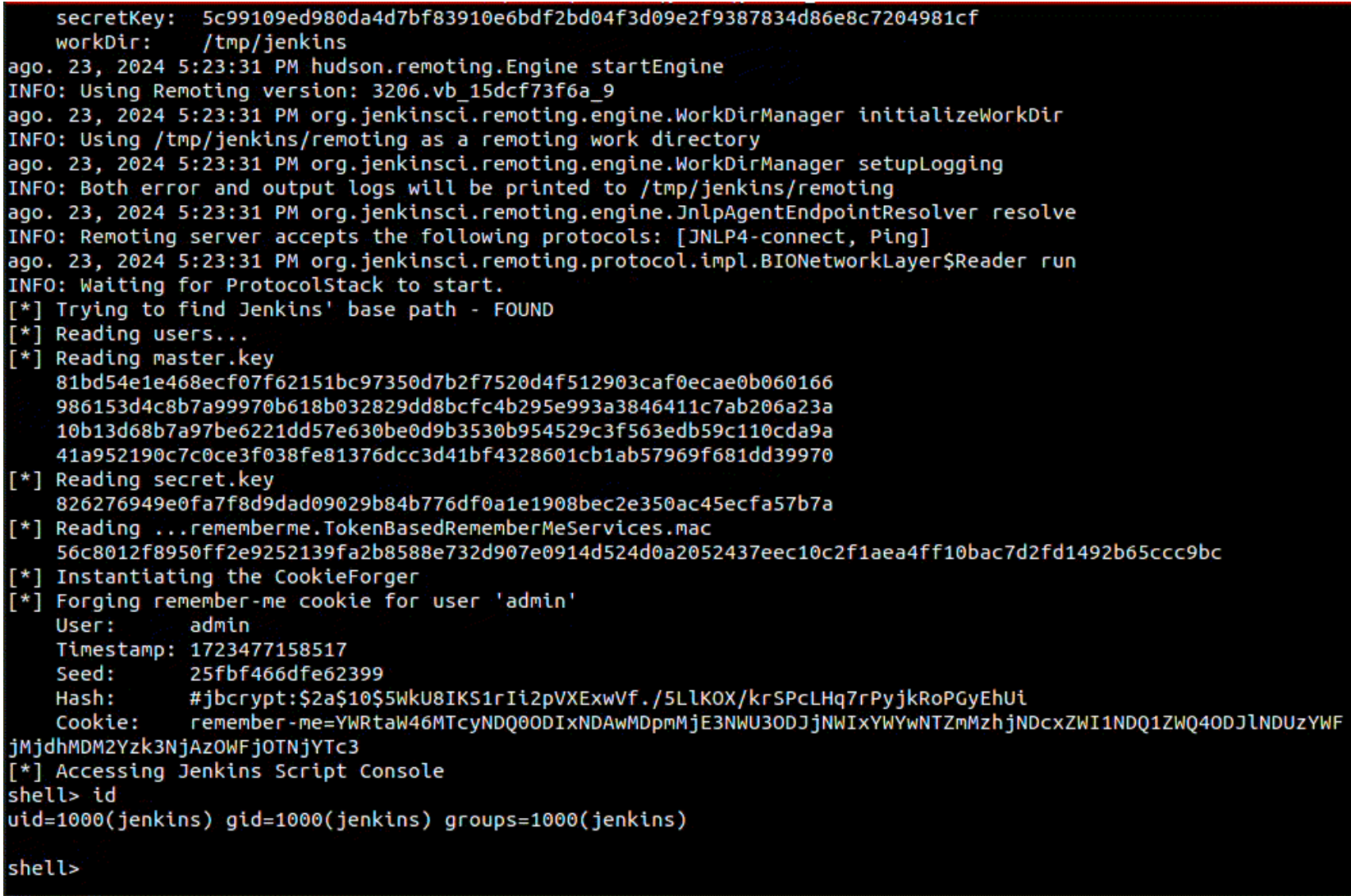
Conviso Labs’ proof-of-concept (PoC) exploit demonstrates the serious implications of CVE-2024-43044. The attack sequence is as follows:
- Reference Acquisition: The exploit first acquires a reference to the
hudson.remoting.RemoteClassLoader. - File Reading: Using this reference, the attacker creates a file reader to access specific files from the controller.
- Data Extraction: The attacker reads three critical files to forge a cookie for a given user.
- User Enumeration: The exploit then reads a list of Jenkins users, including detailed information like ID, timestamp, seed, and hash.
- Cookie Forging: Using the gathered data, the attacker forges a “remember-me” cookie for various users until access to the Jenkins Scripting Engine is obtained.
- Command Execution: With access to the scripting engine, the attacker can execute system commands on the Jenkins server.
- Credential Dumping: Finally, the exploit dumps usernames and hashes in a format ready for cracking using tools like John the Ripper.
This vulnerability has been addressed in Jenkins version 2.471, and in the long-term support (LTS) versions 2.452.4 and 2.462.1. Organizations using Jenkins are strongly advised to update to these versions immediately to mitigate the risk posed by this vulnerability.
Related Posts:
- CVE-2024-43044: Critical Jenkins Vulnerability Exposes Servers to RCE Attacks
- Hackers earn $3 million by exploiting Jenkins servers and inserting mining Monero scripts
- Misconfigured Jenkins Servers Targeted in Cryptojacking Attacks
- RansomEXX Group Exploits Jenkins Vulnerability (CVE-2024-23897) in Major Indian Banking Attack
- Jenkins Security Vulnerabilities: What You Need to Know





