CVE-2024-46483 (CVSS 9.8): Xlight FTP Server Flaw Leaves Users Exposed to Remote Attacks, PoC Published
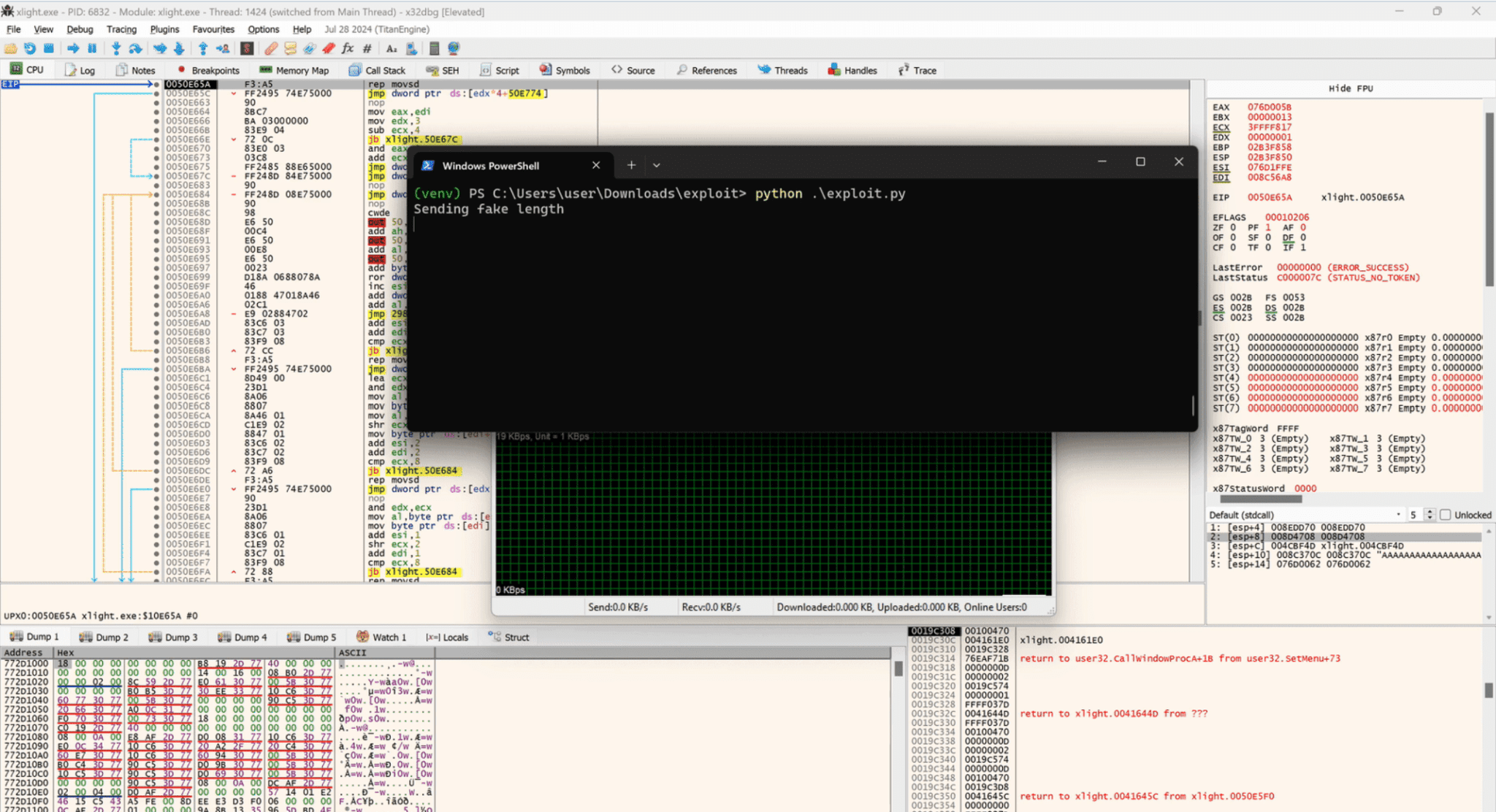
A severe security vulnerability has been identified in the Xlight SFTP server, a popular Windows-based FTP and SFTP solution designed for secure, high-performance file transfer. Designated as CVE-2024-46483, this pre-authentication heap overflow vulnerability has earned a CVSS score of 9.8, reflecting its critical impact potential. The flaw affects Xlight versions 3.9.4.2 and earlier for both 32-bit and 64-bit architectures, allowing unauthenticated attackers to achieve remote code execution or trigger a denial of service.
The vulnerability stems from a heap overflow issue within the SFTP protocol implementation. When processing strings sent by clients, Xlight fails to properly validate the length, leading to an integer overflow. This allows attackers to craft malicious packets that trigger a massive memory copy operation, writing data beyond the allocated buffer.
The impact of this vulnerability depends on the version of Xlight being used:
- 32-bit Versions: Attackers can overwrite critical data structures on the heap, potentially leading to code execution.
- 64-bit Versions: While code execution is less likely on 64-bit systems, the vulnerability still allows for crashes, resulting in denial of service.
Adding to the concern, a proof-of-concept exploit is publicly available on Github, making it easier for malicious actors to exploit this flaw.
Users of Xlight versions 3.9.4.2 and earlier are strongly urged to update to the latest version immediately. The vendor has addressed this vulnerability in subsequent releases.





