CVE-2024-5035 (CVSS 10) in TP-Link Archer C5400X Routers Exposes Users to Remote Hacking
In a recent security analysis conducted by a researcher at ONEKEY, a critical vulnerability has been identified in the TP-Link Archer C5400X router. The flaw, tracked as CVE-2024-5035, has been given a maximum CVSS score of 10, indicating its potential for severe impact. This vulnerability allows for remote code execution (RCE) due to command injection and buffer overflow issues in the rftest binary, which is used for radio frequency testing.

Image: ONEKEY
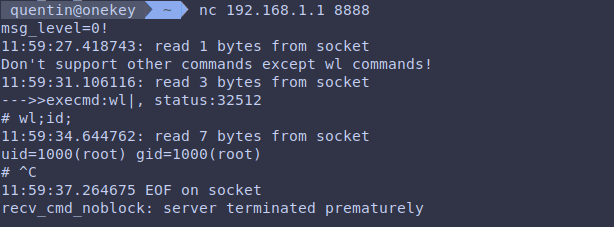
The CVE-2024-5035 vulnerable rftest binary, designed for wireless interface self-assessment, exposes a network listener on three TCP ports (8888, 8889, and 8890). Unfortunately, this listener is susceptible to command injection attacks. This means an attacker could remotely send malicious commands through these ports, effectively taking control of the router without any authentication.
ONEKEY researchers found that while the router attempts to limit the types of commands it accepts, attackers can easily bypass these restrictions using common shell meta-characters like semicolons (;), ampersands (&), or pipes (|). This allows them to inject and execute arbitrary commands, potentially leading to a full-blown compromise.
By exploiting this flaw, an unauthenticated remote attacker can gain arbitrary command execution on the device with elevated privileges. This could allow the attacker to take full control of the router, potentially compromising any connected devices and intercepting or manipulating network traffic.
TP-Link has addressed the issue in version 1_1.1.7 of the router’s firmware. Users are strongly advised to upgrade to this version immediately to protect themselves from this vulnerability. The upgrade can be performed through the router‘s web interface.