CVE-2024-8105: An UEFI Flaw Putting Millions of Devices at Risk

A significant vulnerability, CVE-2024-8105, dubbed PKfail, has surfaced within the UEFI ecosystem. With a CVSS score of 8.2, this flaw exposes critical UEFI security mechanisms to compromise, making systems vulnerable to malicious attacks that can bypass even the most fundamental protections like Secure Boot.
The Unified Extensible Firmware Interface (UEFI) is a critical component that bridges the gap between a computer’s firmware and its operating system. It employs a Public Key Infrastructure (PKI) to establish trust among the platform owner, firmware, and the operating system, with the Platform Key (PK) serving as the cornerstone of this trust model. Ideally, these keys are securely generated and managed using Hardware Security Modules (HSMs) by Original Equipment Manufacturers (OEMs).
However, the complexity of the modern supply chain, involving numerous Independent BIOS Vendors (IBVs) and third-party partners, has led to a lax implementation of this security protocol. In practice, many UEFI software and drivers are developed using temporary test keys or “softkeys” that are hard-coded into the firmware for ease of development and testing. Alarmingly, these softkeys have been inadvertently included in production firmware, creating a significant security loophole.
The PKFail vulnerability exploits these hard-coded, untrusted Platform Keys that have been mistakenly shipped within production firmware. Attackers who gain access to the private portions of these test keys can sign malicious UEFI software, allowing them to execute code with the highest privileges during the early boot phases of a system, even when Secure Boot is enabled.
This unauthorized access enables attackers to:
- Bypass UEFI Security Features: Neutralizing protections like Secure Boot, which are designed to prevent unauthorized software from loading during the boot process.
- Establish Persistent Malware: Installing stealthy and resilient malware that can survive reboots and even operating system reinstalls, making detection and removal exceedingly difficult.
- Exfiltrate Sensitive Data: Creating covert backdoors and communication channels to steal confidential information undetected.
- Cause System Disruption: Potentially damaging hardware, corrupting data, or initiating permanent shutdowns of affected devices.
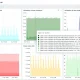
The list of impacted vendors includes major names like Acer, Dell, HP, Intel, Lenovo, and more. It’s estimated that millions of devices could be vulnerable.
While the CVE-2024-8105 vulnerability poses a serious threat, organizations can take several steps to mitigate the risk:
- Update UEFI Firmware: It is critical to ensure that systems are running the latest version of UEFI firmware provided by the manufacturer. Vendors are already releasing updates to address this vulnerability.
- Assess the Impact Using Research Tools: Tools like those provided by Binarly can help administrators assess the presence of untrusted Platform Keys and determine the vulnerability status of their systems.
- Leverage Automatic Firmware Updates: Many operating systems, including Linux and Windows, support automatic firmware updates. Using tools like fwupdmgr or OEM mechanisms to regularly check and apply updates is a crucial step in securing systems.