CVE-2024-8353 (CVSS 10): Critical GiveWP Flaw, 100k WordPress Sites at Risk
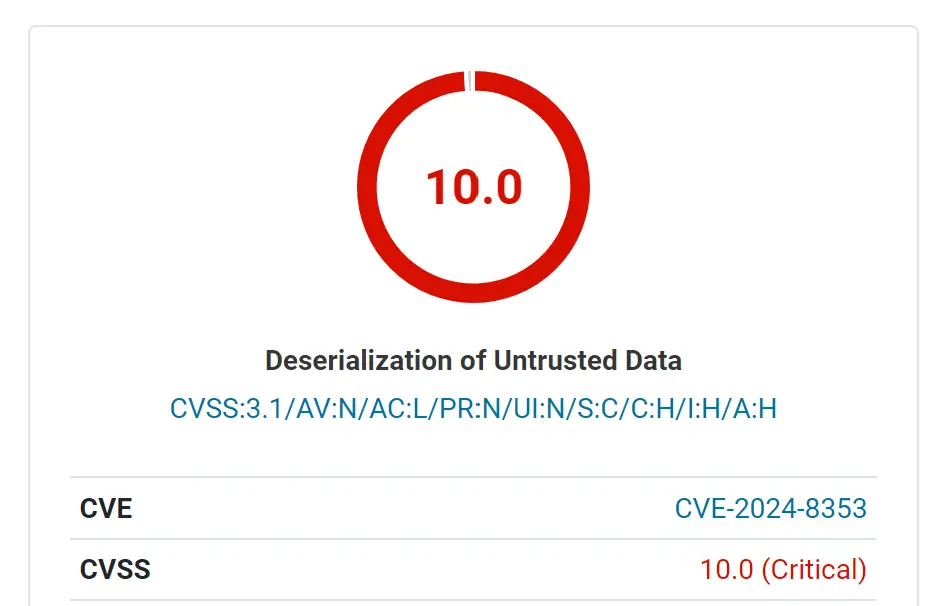
A critical vulnerability has been discovered in the popular GiveWP donation plugin for WordPress, potentially allowing unauthenticated attackers to take complete control of affected websites. The flaw, tracked as CVE-2024-8353 and assigned a maximum severity score of 10, stems from a PHP Object Injection vulnerability that can lead to remote code execution.
CVE-2024-8353 is a PHP Object Injection vulnerability that occurs due to improper handling of untrusted input, specifically during the deserialization of several parameters, such as ‘give_title’ and ‘card_address’. This flaw allows unauthenticated attackers to inject a malicious PHP object into the system. The additional presence of a POP (Property Oriented Programming) chain allows attackers to leverage this vulnerability to delete arbitrary files and gain remote code execution on the target website.
This vulnerability is nearly identical to CVE-2024-5932, but with one key difference: the use of stripslashes_deep on user_info bypasses the is_serialized check, enabling attackers to exploit the deserialization process. Despite a partial patch in version 3.16.1, further hardening was required to mitigate the vulnerability addressed in version 3.16.2 fully.
All versions of GiveWP up to and including 3.16.1 are vulnerable. With over 100,000 active installations, this represents a significant security risk to a large number of WordPress websites that rely on this plugin for their fundraising efforts.
Immediate action is crucial. Update GiveWP to version 3.16.2 or later as soon as possible. This release contains the necessary patches to address the vulnerability and mitigate the risk of exploitation. Website administrators should monitor their logs for any suspicious activity, particularly deserialization errors or unexplained file deletions. Employing additional security layers, such as web application firewalls (WAFs) and intrusion detection systems (IDS), can help mitigate the risk of future vulnerabilities.





