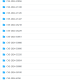
CVE-2024-8522 & CVE-2024-8529 (CVSS 10): LearnPress SQLi Flaw Leaves 90K+ WordPress Sites at Risk
Two critical SQL injection vulnerabilities have been discovered in LearnPress, a popular WordPress plugin used to create and manage online courses. The flaws, tracked as CVE-2024-8522 and CVE-2024-8529, carry a maximum CVSS score of 10, indicating their severity. This vulnerability could allow unauthenticated attackers to execute malicious SQL queries, potentially gaining access to sensitive information stored within the affected WordPress databases.
With over 90,000 active installations, LearnPress is a widely used plugin, making the impact of this vulnerability significant. Attackers could exploit this flaw to steal user data, modify course content, or even take complete control of vulnerable websites.
The vulnerability resides in the LearnPress REST API endpoint, specifically in the handling of the ‘c_only_fields’ and ‘c_fields’ parameters. Insufficient escaping and inadequate preparation of SQL queries allow attackers to inject malicious SQL code.
With a CVSS score of 10—the highest severity rating—CVE-2024-8522 & CVE-2024-8529 present a critical risk to websites using LearnPress. Successful exploitation could result in:
- Extraction of sensitive information, including user credentials, personal data, and course-related information.
- Database tampering, which may include modifying, deleting, or corrupting stored data.
- Further compromise of the WordPress site, potentially leading to full control over the site’s data.
Given the simplicity of the attack, as it can be executed by unauthenticated users, any WordPress site running a vulnerable version of LearnPress is at immediate risk.
The developers of LearnPress have released version 4.2.7.1 to address this critical vulnerability. All users are strongly urged to update their LearnPress plugin to the latest version immediately.