Cyber Shadows: Decoding APT-K-47’s Sophisticated Attacks
In the complex and shadowy world of cyber espionage, the emergence of APT-K-47, also known as Mysterious Elephant, marks a significant addition to the global landscape of Advanced Persistent Threats (APTs). First brought into the limelight by the Knownsec 404 Advanced Threat Intelligence Team, APT-K-47 has quickly garnered attention for its sophisticated cyber-attack techniques, which bear similarities to other notorious APT groups in South Asia, including Sidewinder, Confucius, and Bitter.
APT-K-47’s modus operandi is characterized by its adept use of social engineering tactics, particularly phishing attacks tailored around current events. These attacks often exploit vulnerabilities in CHM files, document vulnerabilities like CVE-2017-11882, and WinRAR software vulnerabilities, showcasing the group’s technical prowess. The organization’s primary targets span across Russia, Pakistan, Bangladesh, and the United States, indicating its wide geopolitical interest and the potential high-stakes information it seeks.

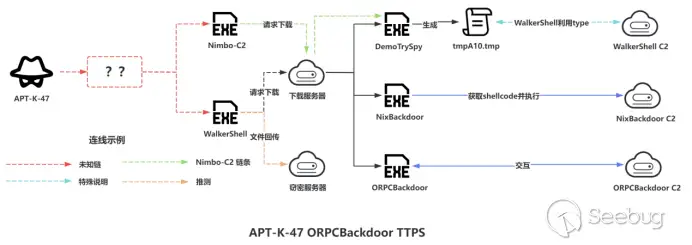
Overall Attack Chain
In August 2023, the Knownsec 404 Team disclosed ORPCBackdoor, a tool associated with APT-K-47, which marked the beginning of a closer observation of this group’s activities. Subsequent discoveries have revealed a toolkit comprising undisclosed Trojans like WalkerShell and Nimbo-C2, alongside other malicious payloads designed for data exfiltration and long-term access to compromised systems.
WalkerShell and DemoTrySpy, two of the tools in APT-K-47’s arsenal, demonstrate the group’s focus on stealing sensitive information, such as browser passwords, and ensuring persistent access to victim’s networks. This approach not only underscores the technical sophistication of APT-K-47 but also highlights its strategic intent to infiltrate and monitor targeted entities over extended periods.
APT-K-47’s emergence and evolving tactics reflect a broader trend in the cyber threat landscape, where APT groups continually adapt and refine their strategies to evade detection and achieve their objectives. As cybersecurity professionals and organizations worldwide strive to counter these threats, the case of APT-K-47 serves as a stark reminder of the need for vigilance, advanced threat intelligence, and robust defense mechanisms in the digital age.