Cybercriminals Exploit DocuSign API to Send Convincing Phishing Invoices at Scale
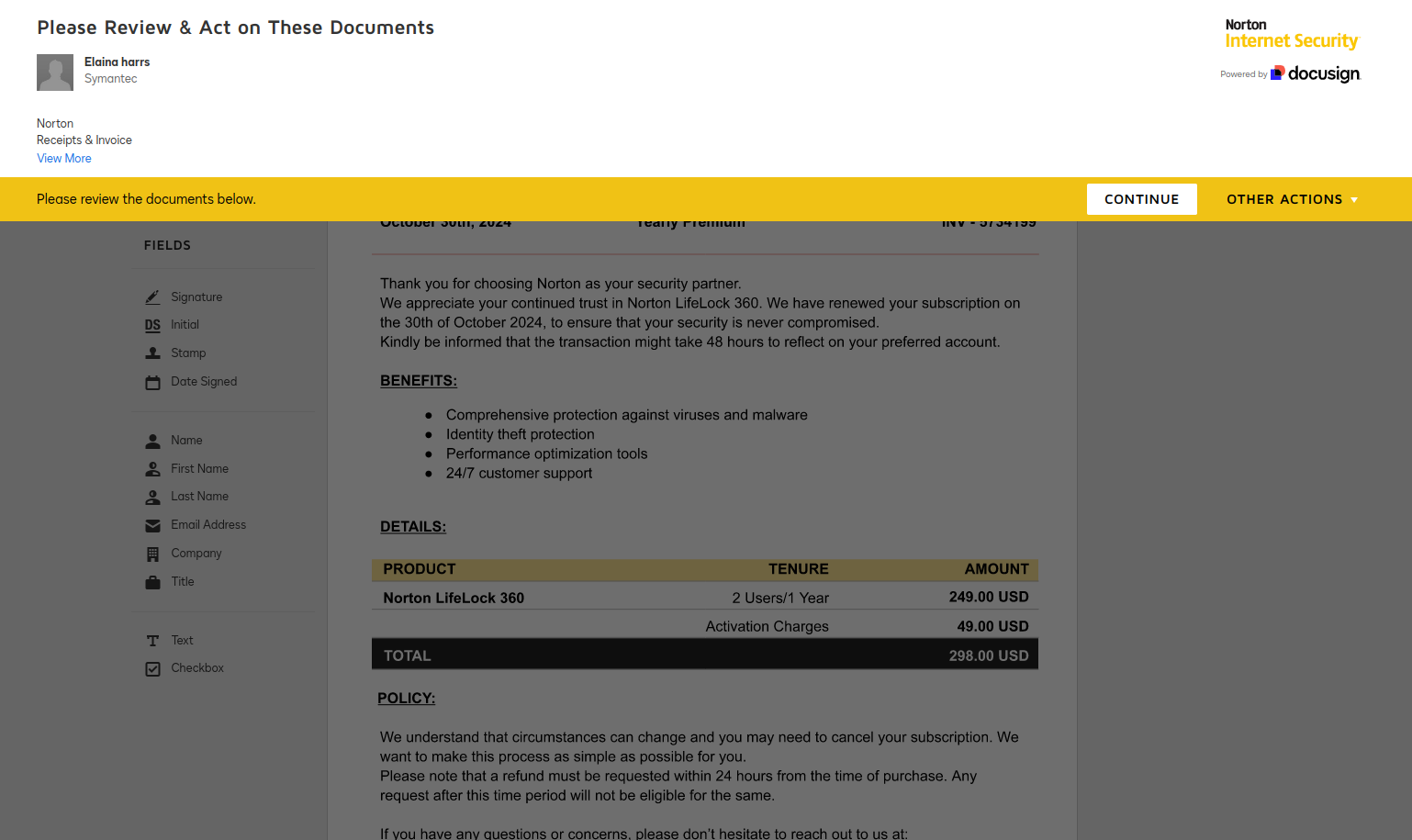
In a sophisticated twist on phishing, cybercriminals are now leveraging DocuSign’s API to send fraudulent invoices that appear alarmingly authentic, according to a new report from Wallarm security researchers. Unlike traditional phishing schemes, these attacks exploit legitimate DocuSign accounts and templates to mimic reputable brands, making detection far more difficult for both users and security systems.
“These incidents use genuine DocuSign accounts and templates to impersonate reputable companies,” Wallarm explains, highlighting that attackers are going beyond simple spoofed emails and malicious links. By embedding themselves within a trusted service, these attackers can bypass common email and spam filters. For instance, some attackers have been observed creating invoices that mimic Norton Antivirus branding, complete with genuine-looking layouts and accurate pricing information, which add a $50 activation fee or direct payment instructions to further lure victims.
Attackers create legitimate, paid DocuSign accounts, enabling them to manipulate templates and directly interact with the API. “An attacker creates a legitimate, paid DocuSign account that allows them to change templates and use the API directly,” Wallarm notes. Through DocuSign’s Envelopes API, the attacker can automate the creation and dispatch of large volumes of invoices that are nearly indistinguishable from genuine requests.
These invoices, sent through DocuSign’s secure environment, do not contain traditional red flags like malicious links or attachments. Instead, the danger lies in the seemingly legitimate request for payment. Users who unwittingly “e-sign” the document might unknowingly authorize payments that flow directly into attackers’ accounts.
Over recent months, reports of such schemes have surged within DocuSign’s community forums. Wallarm points out that this increase in malicious activity highlights a concerning pattern: “attackers are not just impersonating companies, but are embedding themselves within legitimate communication channels to execute their attacks.”
Wallarm emphasizes the importance of a multi-layered defense to counter this emerging threat. Key recommendations include:
- Verify Sender Credentials: Double-check any incoming DocuSign communications, scrutinizing email addresses, especially if they originate from personal domains like Outlook or Gmail.
- Implement Internal Approvals: Require approvals for financial transactions across multiple departments or team members, making it harder for attackers to exploit a single point of failure.
- Raise Employee Awareness: Conduct training sessions to ensure employees recognize that authentic-looking emails from trusted platforms might still be fraudulent.
- Monitor for Anomalous Requests: Be vigilant for unexpected invoices, unusual charges, or changes in vendor accounts. Even subtle details, like unexpected capitalizations, can be signs of foul play.
The Wallarm report also urges service providers to reassess the security of their APIs. “Understanding where your APIs might be abused is key,” the report advises, recommending API rate limiting and behavior profiling tools to detect suspicious activities. By implementing targeted restrictions on API usage, providers like DocuSign can help mitigate the risk of large-scale abuse.




