Cybercriminals Leverage Docusign Phishing Templates in Sophisticated Attacks
Abnormal Security, a leading cybersecurity firm, has issued a warning regarding a significant increase in Docusign-themed phishing attacks. The firm’s research reveals that cybercriminals are exploiting customizable templates available on the dark web to craft highly convincing phishing emails, deceiving unsuspecting victims into divulging sensitive information or clicking on malicious links.
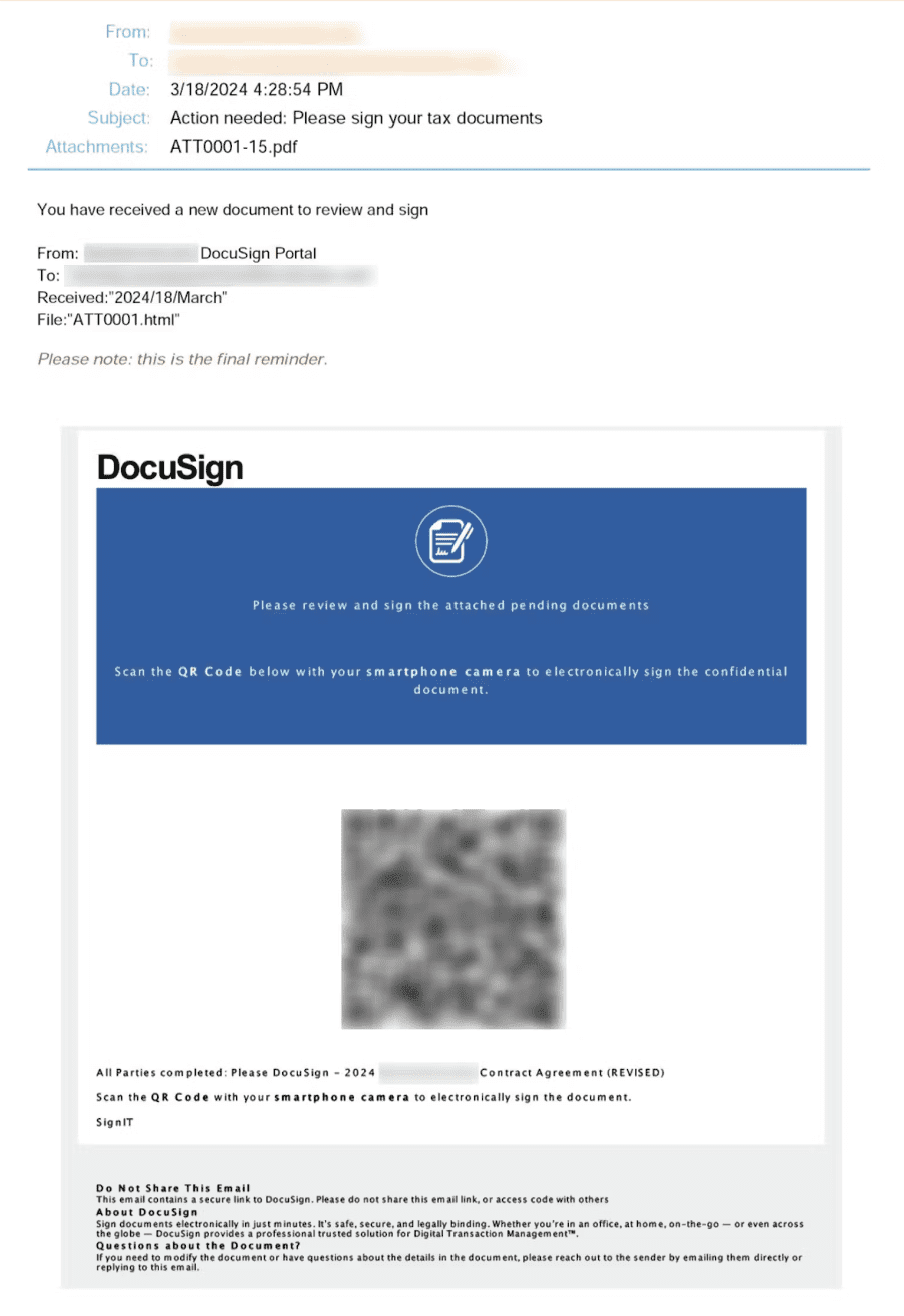
These fraudulent emails closely mimic legitimate Docusign document signing requests, capitalizing on the platform’s widespread adoption and trusted reputation. The surge in these attacks is attributed to various factors, including Docusign’s popularity across industries, the growing sophistication of cybercriminal tactics, and the availability of readily accessible phishing templates on underground forums.

Example of a Docusign phishing email | Image: Abnormal Security
Investigations by Abnormal revealed that these phishing templates are being traded on cybercrime forums, particularly on a Russian cybercrime forum. The templates are designed to closely resemble authentic Docusign documents, enabling a range of malicious activities such as phishing attacks, identity theft, and financial fraud.
In one instance, Abnormal discovered a forum thread where a user offered custom template modifications for a fee, even providing templates for other services like DHL. This indicates a well-organized marketplace for phishing tools, where cybercriminals can buy ready-made templates to streamline their operations.
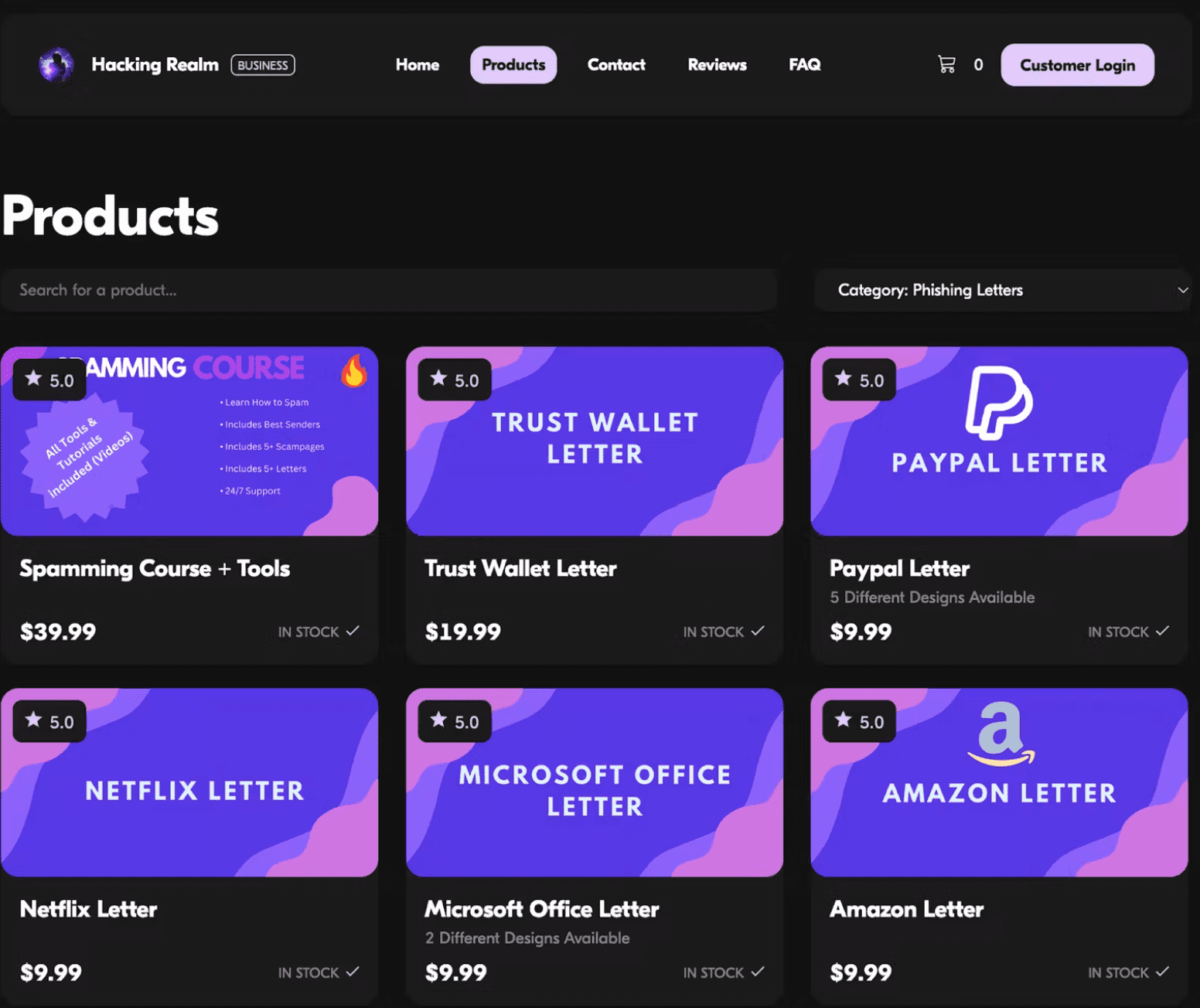
Phishing products and letters sold in bulk for cybercriminals | Image: Abnormal Security
For cybercriminals, authenticity is crucial to maximize the success of their phishing campaigns. They have two primary options: purchase templates from reputable sellers on cybercrime forums or sign up for Docusign to obtain genuine templates directly. While purchasing saves time and effort, it requires the seller to accurately replicate the template and maintain exclusivity. Obtaining templates directly ensures authenticity but takes more time and poses privacy risks.
Many cybercriminals lack the technical skills to create convincing phishing templates from scratch. Purchasing ready-made templates allows them to focus on executing their phishing campaigns rather than investing resources in template creation. This also enables them to launch multiple campaigns simultaneously, targeting different vendors and services, which would be resource-intensive if they had to create unique templates for each target.
Stolen Docusign credentials, often harvested through phishing attacks, are frequently used to launch Business Email Compromise (BEC) attacks. Cybercriminals exploit compromised accounts to access confidential information, impersonate company personnel, and manipulate business partners into transferring funds to fraudulent accounts. The use of forged Docusign documents adds a veneer of legitimacy to these scams, increasing their success rate.
To safeguard against Docusign phishing emails, Abnormal Security recommends a multi-layered approach:
- Scrutinize Email Details: Carefully examine sender email addresses, ensuring they originate from the official “docusign.net” domain. Be wary of generic greetings, spelling errors, and grammatical inconsistencies.
- Verify Security Codes: Authentic Docusign security codes are lengthy and complex. Short or simple codes are indicative of phishing attempts.
- Inspect Links and Attachments: Hover over links to reveal their destination URLs. Exercise caution with attachments, especially those linked to external services like Google Docs/Drive.
- Utilize Docusign’s Secure Access: Access documents directly through Docusign’s website, bypassing potentially malicious links in emails.
- Implement Advanced Security Solutions: Consider deploying comprehensive security solutions, such as Abnormal Security’s platform, which leverages artificial intelligence and machine learning to detect and mitigate sophisticated phishing and BEC threats.




