Czech Officials Targeted in Sophisticated Malware Campaign Disguised as NATO Documents
Seqrite Labs APT-Team has uncovered a sophisticated malware campaign, dubbed “Operation Oxidový,” that targets the Czech government and military officials. The campaign, which began in May 2024, employs NATO-themed decoy documents to lure victims into executing a series of malicious payloads, ultimately compromising their systems. The malware ecosystem involved in this operation is extensive, leveraging advanced tools such as the Rust-based loader Freeze and the Havoc Command-and-Control framework. This operation appears to be the work of a Russian threat actor group, likely motivated by geopolitical tensions in the region.
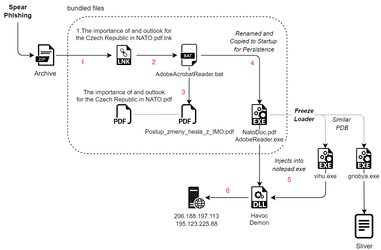
The campaign was first detected on August 4, 2024, when Seqrite Labs identified a malicious ZIP file circulating on platforms like VirusTotal. The file contained decoy documents designed to appear legitimate, with titles such as “The importance of and outlook for the Czech Republic in NATO.” These documents, written in Czech, aimed to deceive high-profile targets by discussing the importance of NATO-Czech relations and offering seemingly official guidelines for password changes within the Czech Ministry of Defense.
One of the decoy documents, Postup_zmeny_hesla_z_IMO.pdf, presented itself as a guide for changing passwords on the Ministry of Defense’s internal network. The other, The importance of and outlook for the Czech Republic in NATO, detailed geopolitical advantages of NATO-Czech relations, providing a convincing cover for the malicious content hidden within the ZIP file.
The attack begins with the execution of a malicious LNK file, deceptively named “The importance of and outlook for the Czech Republic in NATO.pdf.lnk.” This file triggers a batch script, AdobeAcrobatReader.bat, which in turn spawns the decoy document on the victim’s screen while simultaneously executing a more sinister payload in the background. The batch script renames a disguised executable file to AdobeReader.exe and moves it to the startup folder, ensuring the malware’s persistence on the system.
At the core of Operation Oxidový is a Rust-based loader known as Freeze, a tool originally developed for red-team operations but now repurposed by threat actors for malicious activities. The loader employs advanced techniques, such as ETW patching and DLL unhooking, to evade detection by endpoint security solutions. It then decodes and decrypts a compressed shellcode, which is subsequently written into memory and executed.
The final payload, delivered by the loader, is a DLL linked to the Havoc Command-and-Control framework, a powerful post-exploitation tool that allows attackers to maintain control over compromised systems. This payload, known as Demon DLL, is configured to communicate with a Command-and-Control server, exfiltrating sensitive data and executing further commands as directed by the threat actors.
Seqrite Labs’ analysis of the campaign infrastructure, including unique PDB paths and timestamps, suggests that the threat actor behind Operation Oxidový has been active since at least May 2024. The use of open-source offensive tools like Freeze and Havoc, combined with the geopolitical focus of the decoy documents, points to a Russian origin for the campaign. The involvement of Russian interests in the Czech region, coupled with the heavy reliance on sophisticated malware tools, supports this attribution with medium confidence.





