DanaBot Bank Trojan Targets Bank Customers through Phishing Scam
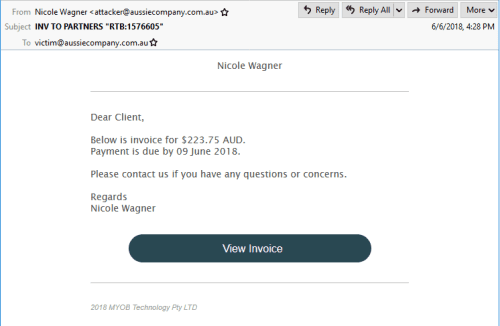
A phishing campaign by the DanaBot Bank Trojan has recently occurred, and criminal elements send emails to potential victims claiming that the content of the email is MYOB’s invoice. MYOB is an Australian multinational company that provides tax, accounting, and other business services software for SMEs. But in fact, the letter contains a dropper file that downloads the DanaBot Bank Trojan. Once downloaded, the Trojans steal private and sensitive information and send screenshots of the machine system and desktop to the command and control server.
MYOB’s Australian customers have discovered a series of phishing email scams. Phishing emails use a standard MYOB-like html invoice template masquerade to convince the user; the content tells the customer that the invoice has expired and asked them to “view invoice” via the button at the bottom of the email.

Image: Trustwave
Karl Sigler, threat intelligence manager at Trustwave, analyzes that criminals may buy or mine a list of MYOB customers. Given that people share a lot of information publicly on various occasions, especially social networks, it is not difficult to get a list. However, Trustwave does not have any information about the number of victims of this activity.
Interestingly, these messages are not linked using the more common HTTP application layer protocol, but instead, utilize File Transfer Protocol (FTP) to point to the attacked FTP server (mainly using the Australian domain). The researcher said: “In clicking this ‘View Invoice’ button a zip archive is pulled down from what we believe is a compromised FTP server of an Australian company. FTP credentials are supplied in the FTP link that is embedded in the ‘View Invoice’ button.” From this point of view, criminals may have invaded the FTP server of an Australian company and used it to spread malware. This may be just for the convenience and use of their resources at the time.
The compressed file contains a JavaScript downloader that downloads the DanaBot Trojan when the archive is executed.
DanaBot, a banking Trojan discovered in May this year, attacked Australian users via emails containing malicious urls, initially discovered by researchers at the Proofpoint. So far, it has become one of the most significant cybercrime events in 2018.
DanaBot is a sample of the latest malware, focusing on persistence and stealing useful information that can later be monetized without requiring the victim to request a ransom immediately. DanaBot’s modular nature allows it to download more components, which increases the banker’s flexibility and powerful stealing capabilities as well as remote monitoring capabilities.
In this recent event, the DanaBot malware first put a downloader file into a disk and executed it. Then download the main DLL (dynamic link library, which contains code and data, can be used by multiple programs at the same time). Once downloaded the DanaBot main DLL downloads and decrypted an encrypted file containing various modules and configuration files. The DLL module includes VNC, stealer, sniffer, and TOR. The file names of the DLLs extracted from the encrypted data reveal the true intentions of the attackers. These dlls enable attackers to create and control remote hosts via VNC, steal private and sensitive information, and use hidden channels through Tor.
At the same time, five configuration files (PInject, BitKey, BitVideo, BitFilesX, and Zfilter) will be set using their functions. Sigler told the media, “These files are used by malware as a reference for finding content on the victim’s machine.” PInject has a Web injection profile that points to the Australian bank. BitKey and BitVideo are two other configuration files that contain a list of cryptocurrency processes that the robot will monitor. BitFilesX configures a list of monitored cryptocurrency files. Finally, Zfilter searches for malware that should track the progress of network sniffing.
The researchers also pointed out that the DanaBot malware appears to be hosted on a domain that has been configured with “round robin DNS” that uses multiple IPs to rotate traffic and direct it to the attacker-controlled infrastructure.





