Decoding the Web Injection Malware Campaign of 2023
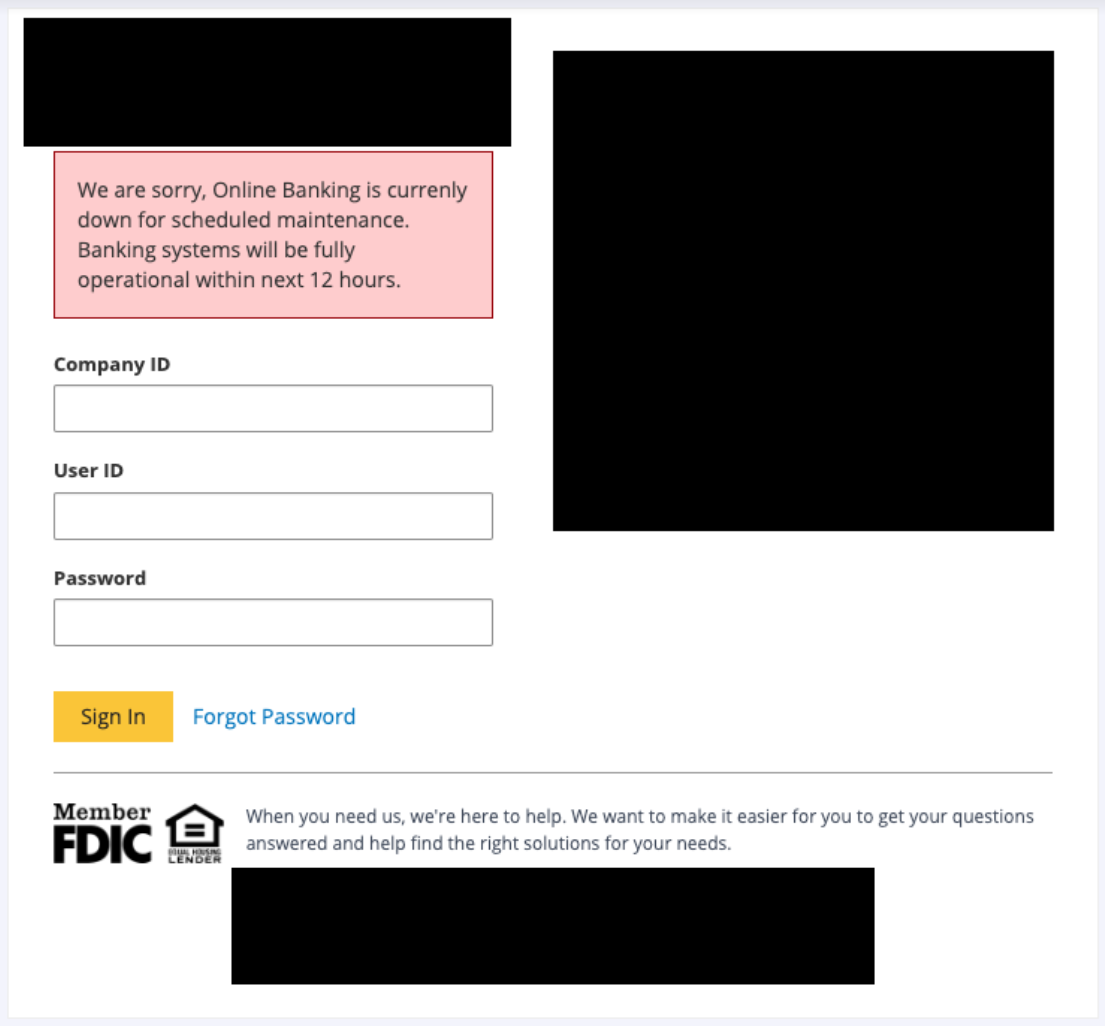
Yesterday, cybersecurity researchers from IBM published a report about a malicious software distribution campaign they uncovered, which uses JavaScript web injections to steal banking data from 40 banks across North America, South America, Europe, and Japan.
The campaign’s genesis dates back to December 2022, with the purchase of malicious domains. By early 2023, the threat actors commenced their orchestration, impacting over 50,000 user sessions. These meticulously executed attacks were not just widespread but notoriously evasive, with possible ties to the notorious DanaBot, though its identity remains shrouded in mystery.
At the heart of this campaign lies the web injection module, designed with a singular focus: to compromise popular banking applications. Once installed, the malware intercepts user credentials and one-time passwords (OTP), granting the attackers unfettered access to, and potentially monetizing, banking information.

Prompting for the received token | Image: IBM
The attackers’ innovation shines in their method of delivering the malicious script. Instead of direct injections, they employed an external resource hosted on the attacker’s server, retrieved by injecting a script tag into the victim’s browser. To evade detection, the hackers used domains resembling legitimate ones like “cdnjs[.]com” and “unpkg[.]com”. Before executing, the script also checks for the presence of certain antivirus products in the victim’s system, all to avoid detection.
The script specifically targets a page structure common across multiple banks. It springs to action when certain keywords and specific login button IDs are detected, injecting new malicious content.
Adding event listeners to the login button, the malware elegantly executes credential theft. It cleverly waits for the user’s interaction, collecting login credentials and OTP tokens. The subtlety of the attack lies in its ability to remain undetected while dynamically responding to the server’s commands.
Exemplifying a client-server architecture, the script continuously updates the server, adjusting its actions based on the received instructions. This level of sophistication allows the malware to adapt its behavior, maintaining a dynamic and resilient web injection system.
Linking this campaign to DanaBot, a modular banking trojan, paints a picture of an advanced threat, adept at executing man-in-the-browser attacks. DanaBot’s hallmark is its adaptability, modifying its tactics to counteract security measures effectively.
As this malware campaign continues to unfold, affecting numerous financial institutions, IBM urges users and organizations to exercise heightened vigilance. This includes monitoring for suspicious activity, avoiding unknown software sources, and adhering to best practices in the password and email security.
In the grand theatre of cybersecurity, this campaign is a stark reminder of the sophistication and persistence of cyber threats. It underscores the need for continuous innovation in defense strategies to counter these evolving digital adversaries.





