Screenshot
As organizations increasingly embrace cloud-native architectures, the attack surface expands, and the need for robust security measures becomes paramount. Traditional security tools often fall short in addressing the dynamic and ephemeral nature of cloud-native environments. Deepfence ThreatMapper steps in to bridge this gap, providing runtime threat management and attack path enumeration capabilities tailored for cloud-native platforms.
Extending Security into Production
While ‘Shift Left’ initiatives focus on securing applications during development, ThreatMapper extends security into production. By continuously monitoring and analyzing the runtime environment, it identifies and prioritizes threats based on their risk-of-exploit. This proactive approach helps organizations detect and remediate vulnerabilities before they can be exploited by malicious actors.
Comprehensive Threat Discovery
ThreatMapper employs a combination of agent-based and agent-less techniques to discover threats across various layers of the cloud-native stack. It scans running workloads, identifies cloud and infrastructure assets, and generates runtime software bill of materials (SBOMs) to uncover vulnerabilities. It also uncovers exposed secrets, such as unprotected keys and passwords, and evaluates infrastructure configurations against compliance benchmarks to identify weaknesses.
Actionable Information with ThreatGraph
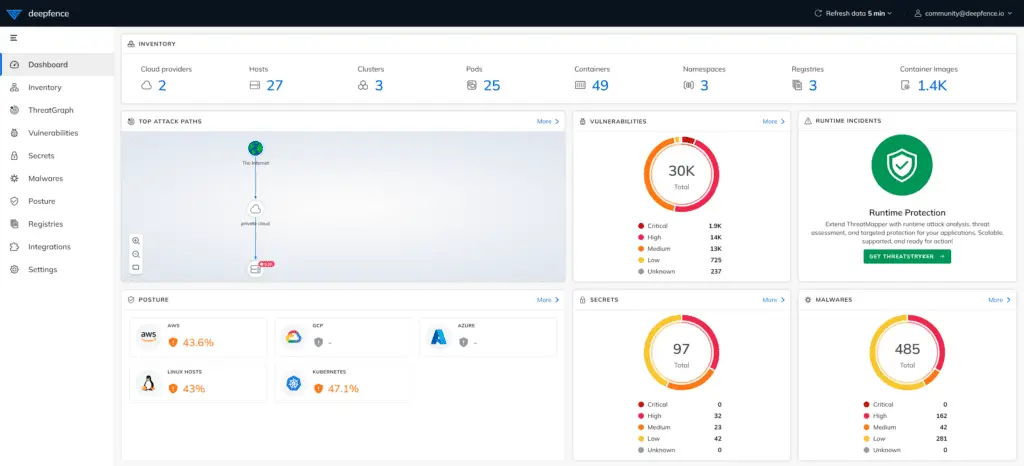
ThreatMapper’s ThreatGraph visualization provides a comprehensive view of the attack surface and the relationships between assets. By ranking threats based on risk-of-exploit, it enables security teams to prioritize remediation efforts and focus on the most critical vulnerabilities. This actionable information empowers organizations to make informed decisions and proactively protect their cloud-native applications.
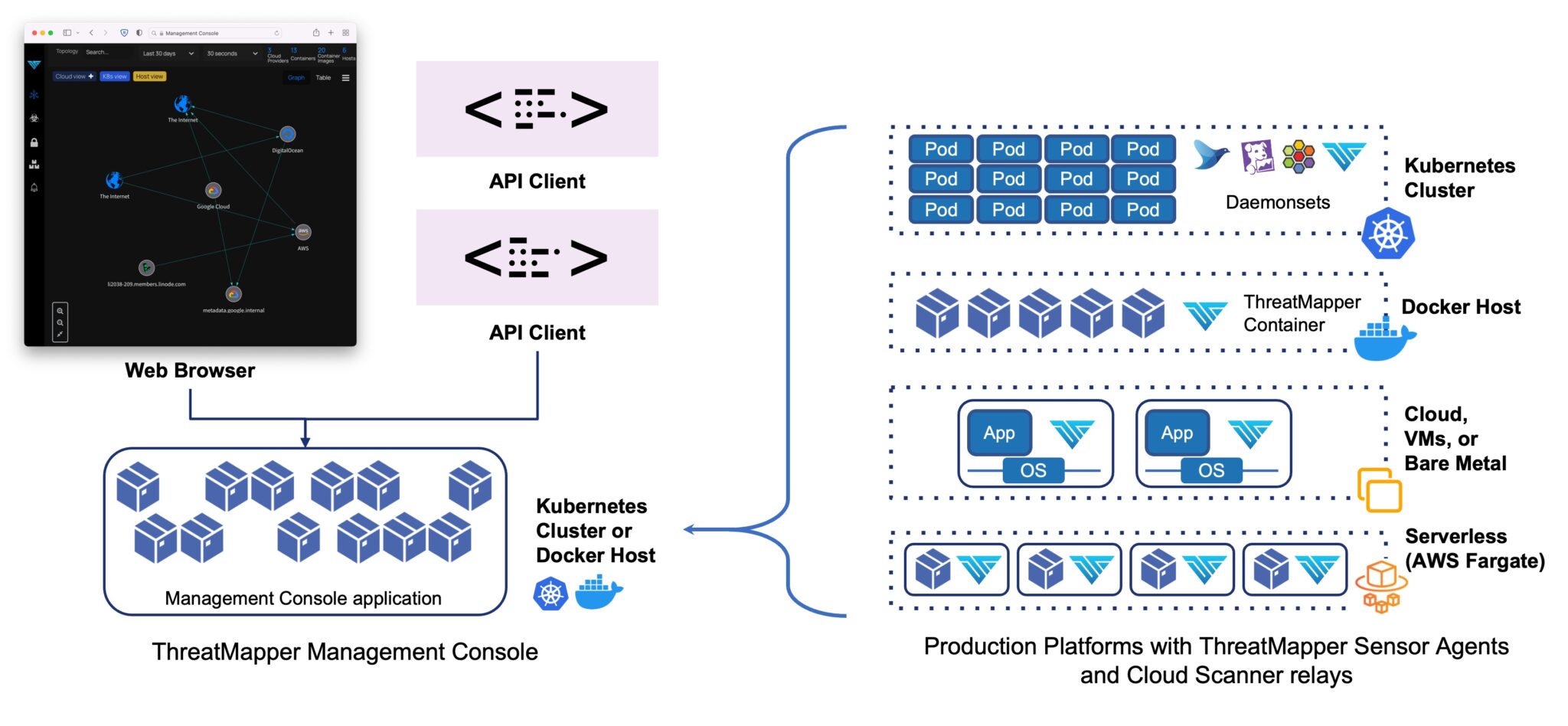
ThreatMapper Architecture
ThreatMapper comprises a Management Console, Sensor Agents, and Cloud Scanner tasks. The Management Console orchestrates the scanning and analysis processes, while Sensor Agents collect data from individual hosts. Cloud Scanner tasks query infrastructure APIs to identify cloud assets and their relationships. This distributed architecture ensures scalability and adaptability to diverse cloud-native environments.
Key Benefits
- Deep Visibility: ThreatMapper provides deep visibility into the runtime environment, uncovering hidden threats and vulnerabilities.
- Prioritization: It ranks threats based on risk-of-exploit, enabling focused remediation efforts.
- Actionable Insights: ThreatGraph visualization empowers security teams to understand attack paths and prioritize mitigation strategies.
- Continuous Monitoring: ThreatMapper continuously monitors the environment, ensuring timely detection and response to threats.
- Compliance: It helps organizations meet regulatory compliance requirements by identifying configuration weaknesses and misconfigurations.
Conclusion
Deepfence ThreatMapper offers a comprehensive solution for runtime threat management and attack path enumeration in cloud-native environments. By providing deep visibility, actionable insights, and continuous monitoring, it empowers organizations to proactively protect their critical assets and data. As the adoption of cloud-native technologies continues to grow, ThreatMapper plays a vital role in ensuring the security and resilience of these complex environments.
For more detailed information and to explore the capabilities of ThreatMapper, refer to the product documentation.