dns parallel prober: find subdomains
What is DNS Parallel Prober?
This is a parallelized domain name prober to find as many subdomains of a given domain as fast as possible.
PLEASE NOTE this script probes DNS servers actively, so please use at your own risk. You are likely to get blacklisted and/or saturate your bandwidth. Whatever you do, it’s your responsibility to make sure you have approval for it.
Hat tip to: Kyle F. for the original idea and to ZephrFish for all improvements and testing.
Quickstart
- Install the requirements:
pip install -r requirements.txt # if you don't want to install stuff as root, do: # virtualenv venv # source venv/bin/activate # pip install -r requirements.txt - Scan all subdomains of
example.comusing the wordlistsubdomains.txt, using 100 threads. Save the results inout.txt:./dns-queue.py example.com 100 out.txt -i subdomains.txt --simulateRemove the
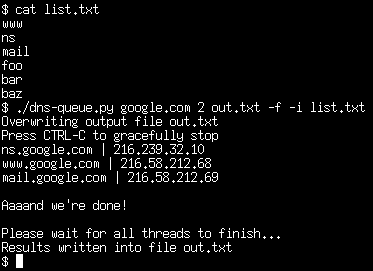
--simulatepart to really scan it. - Example run:
Please note: the
--simulateflag will return random results. This is by design.
Other features
If you want to bruteforce all subdomains (default length: 3), use:
./dns-queue.py example.com 100 out.txt
If you have a very fast upstream and don’t mind flooding DNS servers, use 2000 threads:
./dns-queue.py example.com 2000 out.txt
By default, the script uses the authoritative NS servers for the given domain. To use different DNS servers:
./dns-queue.py example.com 100 out.txt -i subdomains.txt -n ns1.example.com, -n ns2.example.com
For help and other options (e.g. subdomain length, DNS timeouts, etc.):
./dns-queue.py -h
To stop: press ctrl-c – it will wait for the last threads to finish before exiting.
Demo
Copyright (C) 2017 lorenzog
Source: https://github.com/lorenzog/




