dnsbrute v2.0.1: a fast domain brute tool
DNSBrute
Subdomain enumeration is often the first step in penetration testing and is the precondition for collecting IP information and vulnerabilities. Previously testing the subdomain demolition software in the current community is not very satisfactory. The main issues can be summarized as:
- Slow speed
- Incomplete results
- Too unresolved or dealt with pan-analytics
Slow speed
The DNS protocol is simple, the query process is simple, and most language libraries also have functions related to DNS queries. The subdomain explosion is actually a DNS query for each subdomain. The existence of a corresponding resolution record proves that the subdomain exists.
Generally, the query is executed concurrently through a multi-threaded/multi-process approach. The problems with this approach are:
- The upper limit of multi-threaded/multi-process concurrency depends on the limit of the system’s file descriptor (Linux defaults to 1024, manually adjustable: ulimit -n), which makes the actual network IO speed The degree is much smaller than the uplink and downlink bandwidth limit.
- Each query is based on a complete socket connection. Handling connections and waiting for IOs creates a lot of unnecessary time and performance overhead.
Incomplete results
Simply relying on a dictionary will inevitably lead to incomplete blasting results. You can enrich blasting results by collecting some domain interfaces on the Internet, such as hackertarget.com and ptrarchive.com.
Pan-resolution
Pan-Analytics has always been a big issue in domain name blasting. The current solution is to obtain a blacklisted IP based on the exact non-existing subdomain record (md5(domain).domain). The result of the process is blacklisted. However, such a broad filter can easily lead to missed reports. For example, if the ubiquitous record is 1.1.1.1, but an existing subdomain also points to 1.1.1.1, the subdomain may be blacklisted.
Feature
- query over api
- dict based
Advantage
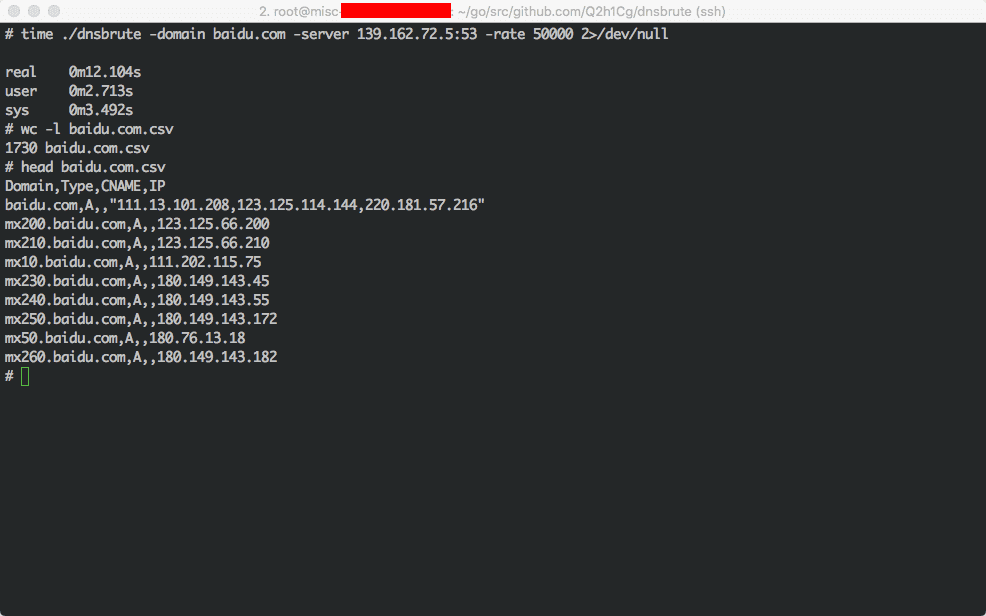
- Fast: 5000~10000+ domains /sec, depending on the network
- Pan-DNS identification
Download
git clone https://github.com/Q2h1Cg/dnsbrute.git
Usage
Source: https://github.com/Q2h1Cg/





