Dr.Web researchers found Triada banking Trojan in over 40 models of cheap Android

According to securityaffairs, reported on March 3, Dr.Web researchers found in more than 40 models of cheap Android machines terrible Triada Bank malware, but also pre-installed. Security researchers at anti-virus software company Dr.Web have uncovered Triada.231 bank malware from 42 cheap Android smartphones.
“In the middle of 2017, Doctor Web analysts discovered a new Trojan Android.Triada.231 in the firmware of some cheap models of Android devices. Since this detection, the list of infected devices has been constantly increasing.“Dr-Web wrote in a blog post. “At the moment, the list contains over 40 models. Doctor Web specialists have monitored the Trojan’s activity and now we can publish the results of this investigation.”

Image: securityaffairs
It is 2016 that the first researchers to discover Triada malware was Kaspersky Lab researchers. At the time, researchers saw it as the most advanced threat to mobile devices.
Hackers in the design of Triada wanted to use it to engage in financial fraud, the most typical is to take this SMS transaction. One of the most interesting features of the malware is that it uses a modular architecture, so in theory, Triada can have a wide variety of destructive capabilities.
Hackers used the Zygote process when the code was embedded in the device, which meant that malware infiltrated each piece of software. There is only one way to eliminate threats: Erase all data on your smartphone and reinstall the entire operating system.
Researchers at Dr.Web pointed out that most of the Android smartphones preloaded with malicious software are small brands, and the hardest hit areas are brands that Advan, Cherry Mobile, Doogee, and Leagoo have not heard of.
Dr.Web also revealed that the culprit of the malware infection was a software developer in Shanghai, and the company was a Leagoo partner. “This company provided Leagoo with one of its applications to be included into an image of the mobile operating system, as well as with an instruction to add third-party code into the system libraries before their compilation. Unfortunately, this controversial request did not evoke any suspicions from the manufacturer. Ultimately, Android.Triada.231 got to the smartphones without any obstacles.” Dr.Web wrote in the post.
The infected application is also being developed by a Chinese company, and security experts point out that the malware code is identical to the software certificate for that infection in 2016.
“The analysis of this application showed it is signed with the same certificate as Android.MulDrop.924. Doctor Web previously wrote about this Trojan in 2016. We can presume the developer that requested adding the additional program into the mobile operating system image can be connected expressly or implicitly with the distribution of Android.Triada.231.” Dr.Web’s blog post said.
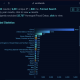
To view the full Android devices that pre-installed Triada banking Trojan, please visit here.
Source: securityaffairs