droopescan v1.45.1 releases: CMS (Drupal, SilverStripe, WordPress) vulnerabilities scanner
droopescan
A plugin-based scanner that aids security researchers in identifying issues with several CMS.
Usage of droopescan for attacking targets without prior mutual consent is illegal. It is the end user’s responsibility to obey all applicable local, state, and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program. Please note that while droopescan outputs the most CMS likely version installed on the remote host, any correlation between version numbers and vulnerabilities must be done manually by the user.
Supported CMS are:
- SilverStripe
- WordPress
Partial functionality for:
- Joomla (version enumeration and interesting URLs only)
- Moodle (plugin & theme very limited, watch out)
- Drupal (plugin discovery partial on new installations of Drupal, patches encouraged)
Changelog v1.45.1
- Updated the database for all CMS.
Installation
Installation is easy using pip:
apt-get install python-pip
pip install droopescan
Manual installation is as follows:
git clone https://github.com/droope/droopescan.git
cd droopescan
pip install -r requirements.txt
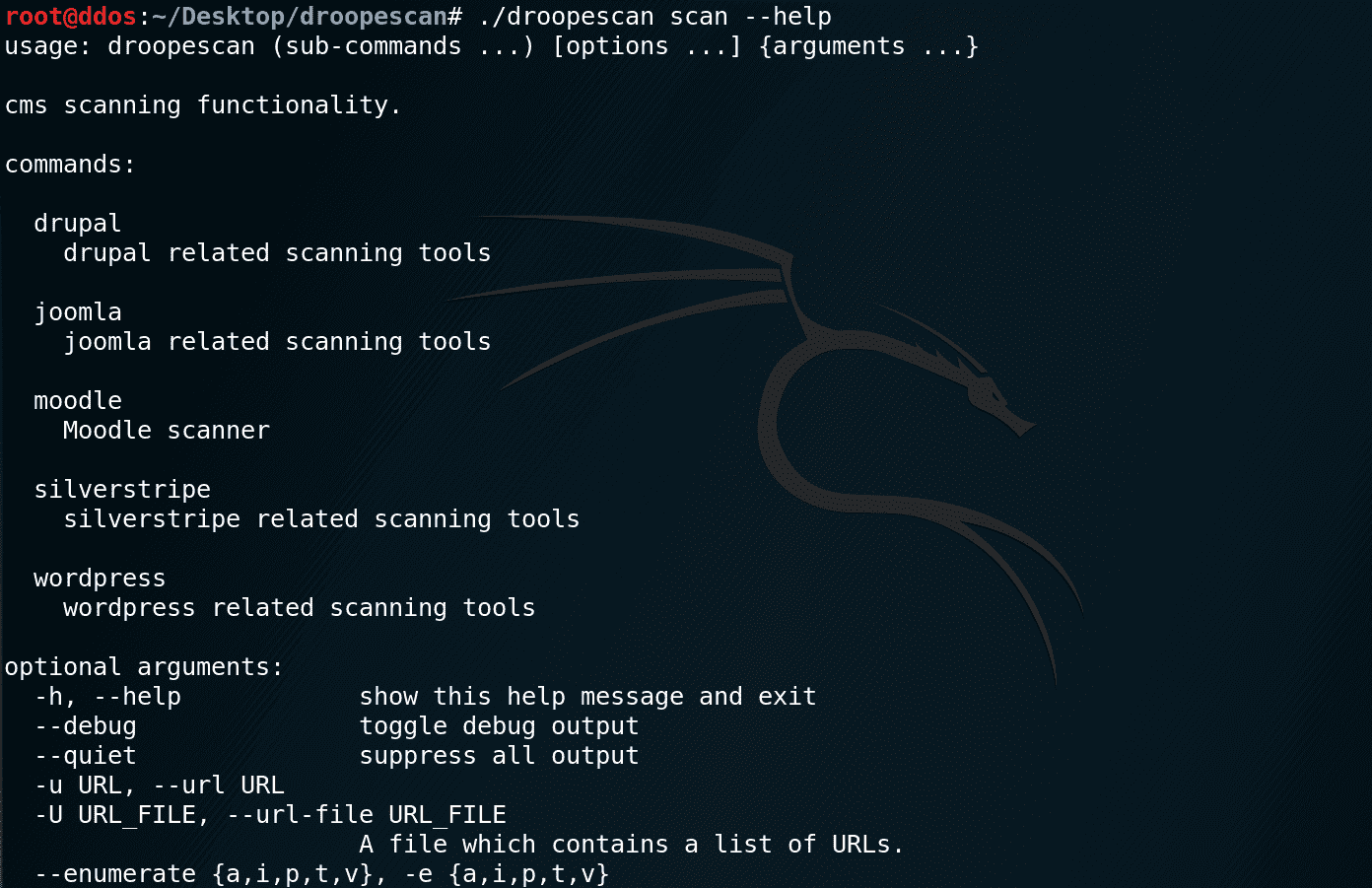
./droopescan scan –help
Features
Scan types
Droopescan aims to be the most accurate by default, while not overloading the target server due to excessive concurrent requests. Due to this, by default, a large number of requests will be made with four threads; change these settings by using the –number and –threads arguments respectively.
This tool is able to perform four kinds of tests. By default, all tests are run, but you can specify one of the following with the -e or –enumerate flag:
- p — Plugin checks: Performs several thousand HTTP requests and returns a listing of all plugins found to be installed on the target host.
- t — Theme checks: As above, but for themes.
- v — Version checks: Downloads several files and, based on the checksums of these files, returns a list of all possible versions.
- i — Interesting url checks: Checks for interesting urls (admin panels, readme files, etc.)
Usage
droopescan –help
Example
Copyright (C) 2015 droope
Source: https://github.com/droope/





