Dupe Key Injector: new XML signature bypass technique
Dupe Key Injector
Dupe Key Injector is a Burp Suite extension implementing Dupe Key Confusion, a new XML signature bypass technique presented at BSides/BlackHat/DEFCON 2019 “SSO Wars: The Token Menace” presentation.
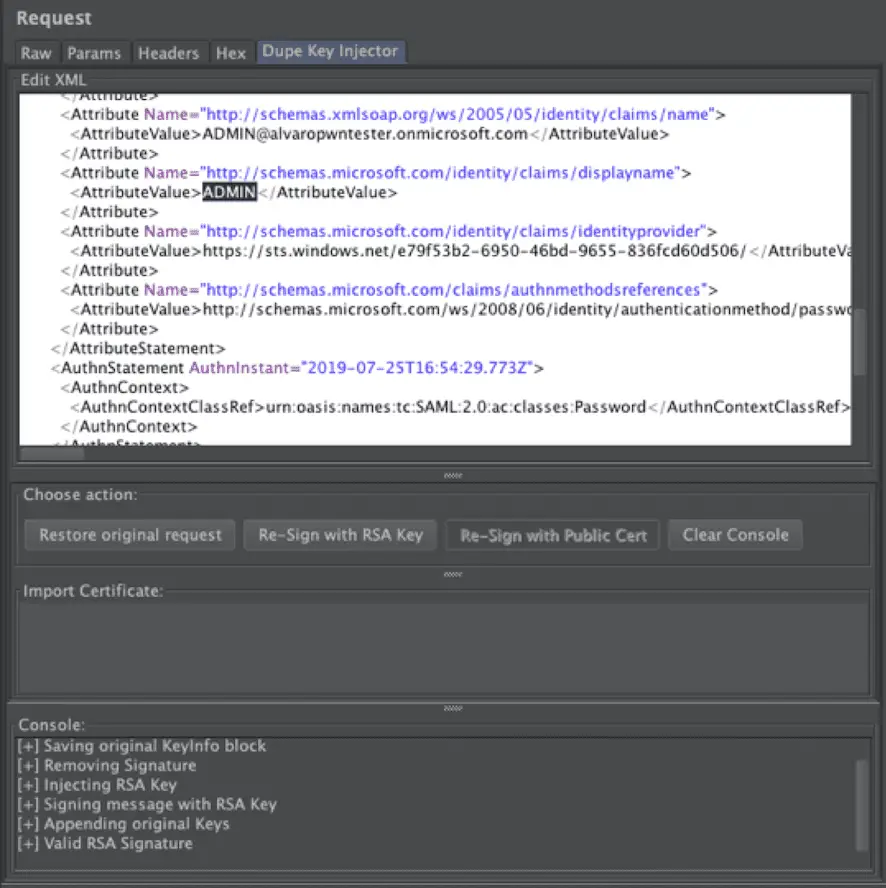
Dupe Key Confusion is a new attack to bypass XML signature verification by sending multiple key identifiers in the KeyInfo section. Vulnerable systems will use the first one to verify the XML signature and the second one to verify the trust on the signing party. This plugin applies this technique to SAML tokens by allowing to modify and then resign the SAML assertion with an arbitrary attacker-controlled key which is then sent as the first element of the KeyInfo section, while the original key identifier is sent as the second key identifier.
For more details about this technique, please refer to the following materials:
- White paper
- Slides
- Exchange RCE Demo
- Exchange Account Takeover Demo
- Sharepoint Privilege Escalation Demo
Install
git clone https://github.com/pwntester/DupeKeyInjector.git
cd DupeKeyInjector
mvn package
Use
Intercept a SAML request and use the Dupe Key Injector tab to modify the assertion and then re-sign it using one of the following techniques:
- Re-sign with RSA key.
- Re-sign with public certificate (only enabled when a public base64 certificate has been imported).
Copyright (c) 2019 Alvaro Muñoz
Source: https://github.com/pwntester/