DVIA-v2: an damn vulnerable iOS application
DVIA-v2
DVIA-v2 written in Swift along with additional vulnerabilities
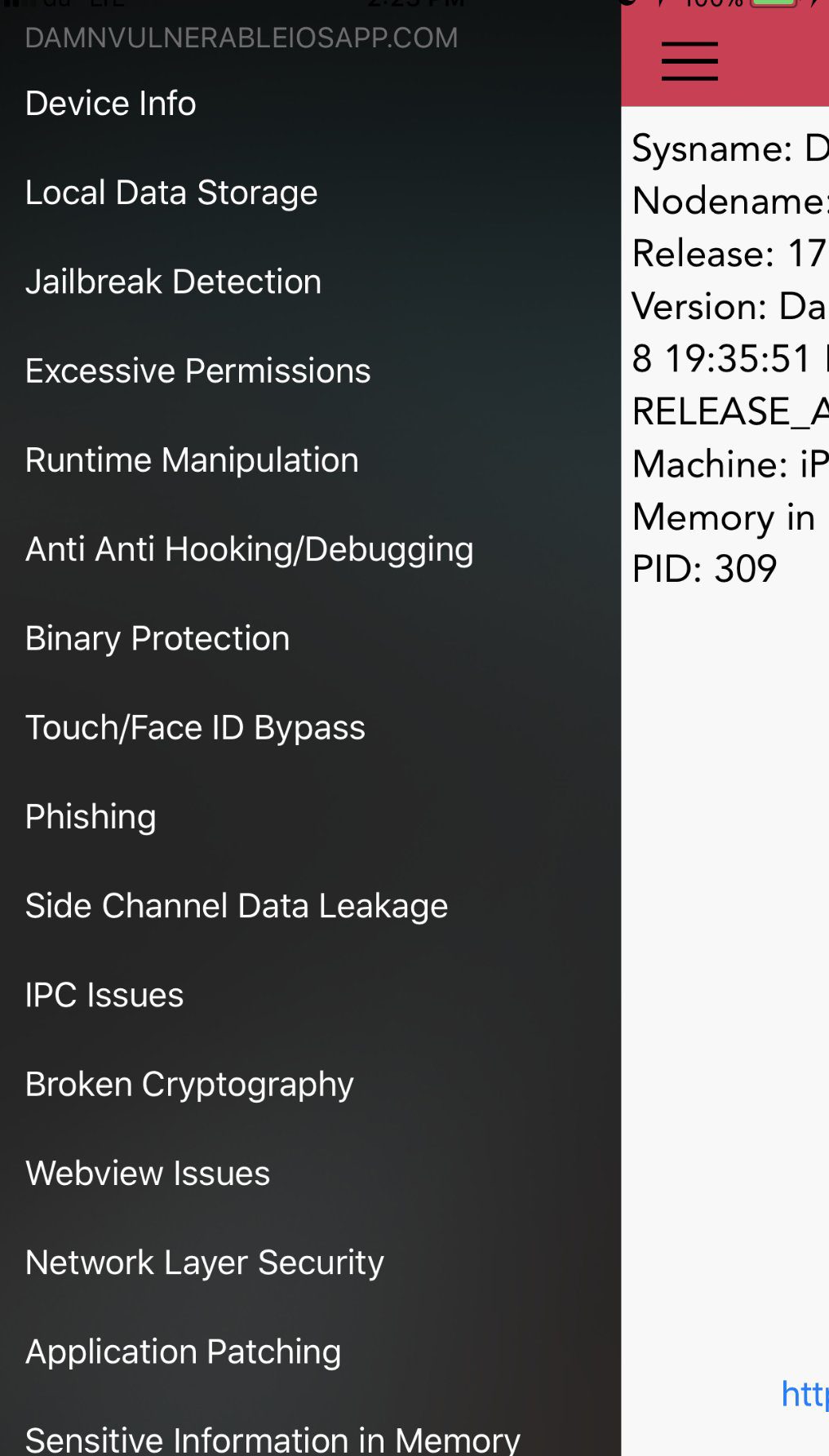
Damn Vulnerable iOS App (DVIA) is an iOS application that is damn vulnerable. Its main goal is to provide a platform for mobile security enthusiasts/professionals or students to test their iOS penetration testing skills in a legal environment. This project is developed and maintained by @prateekg147. The vulnerabilities and solutions covered in this app are tested up to iOS 11. The current version is written in Swift and has the following vulnerabilities.

- Local Data Storage
- Jailbreak Detection
- Excessive Permissions
- Runtime Manipulation
- Anti Anti Hooking/Debugging
- Binary Protection
- Touch/Face ID Bypass
- Phishing
- Side Channel Data Leakage
- IPC Issues
- Broken Cryptography
- Webview Issues
- Network Layer Security
- Application Patching
- Sensitive Information in Memory
Installing DVIA on any iOS device
The best way to install DVIA is using Cydia Impactor
Steps
- Create an Apple ID https://appleid.apple.com/account
- Download Impactor, make sure the device you want to install the app on is connected to your computer. Now drag and drop the IPA file to Impactor.
- Enter your Apple ID credentials. The app will install on the device
- Go to your device, Settings -> General -> Device Management. Select the Apple ID you used to install the app. Click on Verify App under DVIAv2.
Compiling DVIA using Xcode
Steps
- Clone the DVIA repo, git clone https://github.com/prateek147/DVIA-v2
- cd to the project root directory where the Podfile is present (/DVIA-v2/DVIA-v2). Then run pod install
- Open the DVIA-v2.xcworkspace file with Xcode. You can now directly run the app on a simulator.
- For running on the device, go to Project settings in Xcode on the top left, head over to the General tab and under Signing, enter credentials for your Apple ID.
- Now you can build and run the project on the device. You will have to trust the app again by going to Settings -> General -> Device Management.
Copyright (c) 2018 Prateek Gianchandani
Source: https://github.com/prateek147/





