Early Cascade Injection: A Novel Evasion Technique
A new stealthy process injection method, called Early Cascade Injection, has been introduced by security researcher Guido Miggelenbrink from Outflank. This cutting-edge technique offers a new layer of sophistication in evading modern Endpoint Detection and Response (EDR) systems, presenting a significant advancement in the ongoing cat-and-mouse game between attackers and defenders. Combining elements of existing strategies, Early Cascade Injection is set to challenge even top-tier EDRs by avoiding traditional detection methods.
Early Cascade Injection draws upon the well-known Early Bird APC Injection and the EDR-Preloading technique by Marcus Hutchins. Unlike Early Bird APC, which uses cross-process Asynchronous Procedure Calls (APCs), this new technique avoids APC queueing, minimizing remote process interaction and ultimately making it more difficult for EDRs to detect. As Miggelenbrink explains, “This makes Early Cascade Injection a stealthy process injection technique that is effective against top tier EDRs while avoiding detection”.
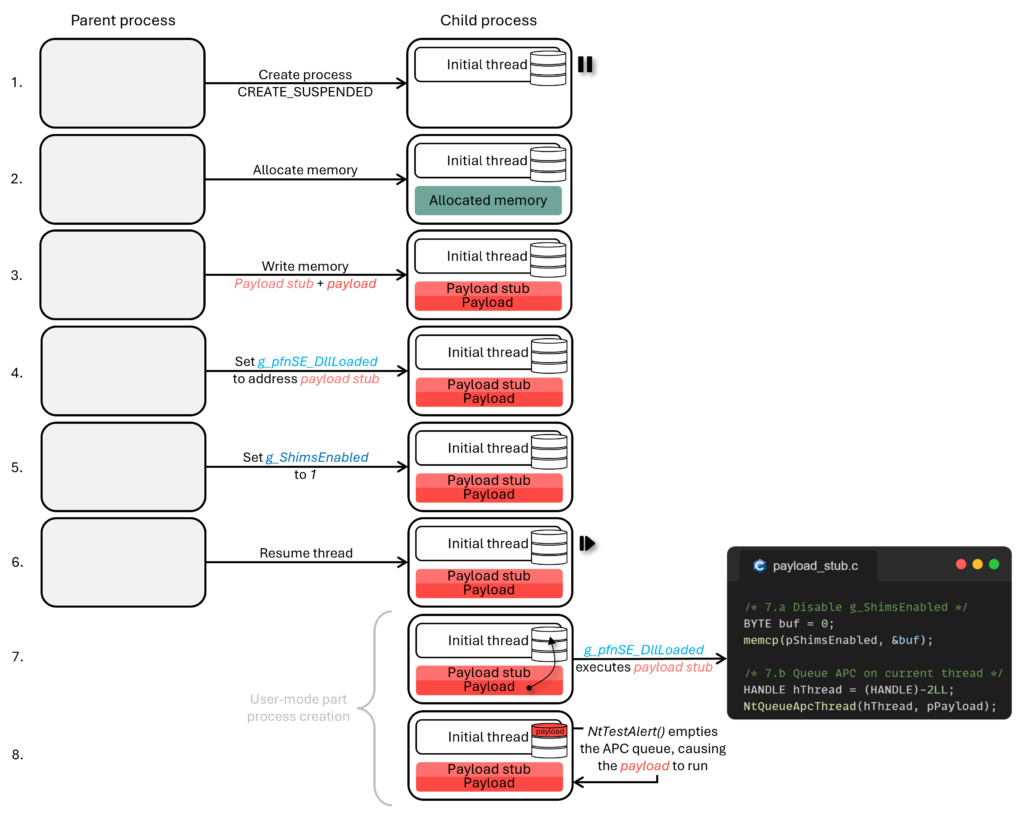
The magic of Early Cascade Injection lies in its timing. It capitalizes on the user-mode part of process creation, intervening at the exact moment before detection measures take hold, enabling the injection of malicious code without triggering security alarms. Specifically, the technique manipulates the Windows process creation flow, using callbacks like g_pfnSE_DllLoaded in ntdll.dll to execute code early in the process lifecycle.
The Early Cascade Injection technique involves the following steps:
- Process Creation in Suspended State: The attacker starts by creating a target process in a suspended state.
- Payload Injection: A two-part payload is injected into the target process. The first part of the payload manipulates g_pfnSE_DllLoaded, a callback pointer, to execute code.
- Queueing the APC: Once the first part of the payload runs, it queues the second part using NtQueueApcThread, ensuring that the main malicious code will execute at the right moment—before the EDR can fully load its hooks.
- Final Execution: As the process resumes, the APC is triggered, and the attacker’s payload runs unobstructed by EDR detection measures
One of the most notable aspects of this technique is its ability to inject code without relying on traditional cross-process interaction, which is often a red flag for security products. Early Cascade Injection only requires memory allocation, protection, and writing, making its footprint much smaller compared to other methods. This approach, as Miggelenbrink highlights, ensures that the technique “does not involve a remote execution primitive (cross-process APC queueing),” which is highly monitored by EDRs.
Furthermore, Early Cascade Injection leverages writable sections of memory like .mrdata and .data, which remain accessible during the process creation phase, eliminating the need for altering memory protections—another behavior that typically raises alarms.
Through extensive testing, Early Cascade Injection has proven to evade multiple leading EDR systems, making it a technique in the attacker’s toolkit. By exploiting timing and minimizing suspicious behavior, this method effectively bypasses traditional detection methods.





