EDRSilencer: The Red Team Tool Turned Cybercriminal Weapon
The Trend Micro Threat Hunting Team has uncovered EDRSilencer, a red team tool designed to disrupt endpoint detection and response (EDR) solutions. Originally intended to help security professionals identify and resolve vulnerabilities in EDR systems, this tool is now being repurposed by cybercriminals to evade detection and carry out undetected attacks.
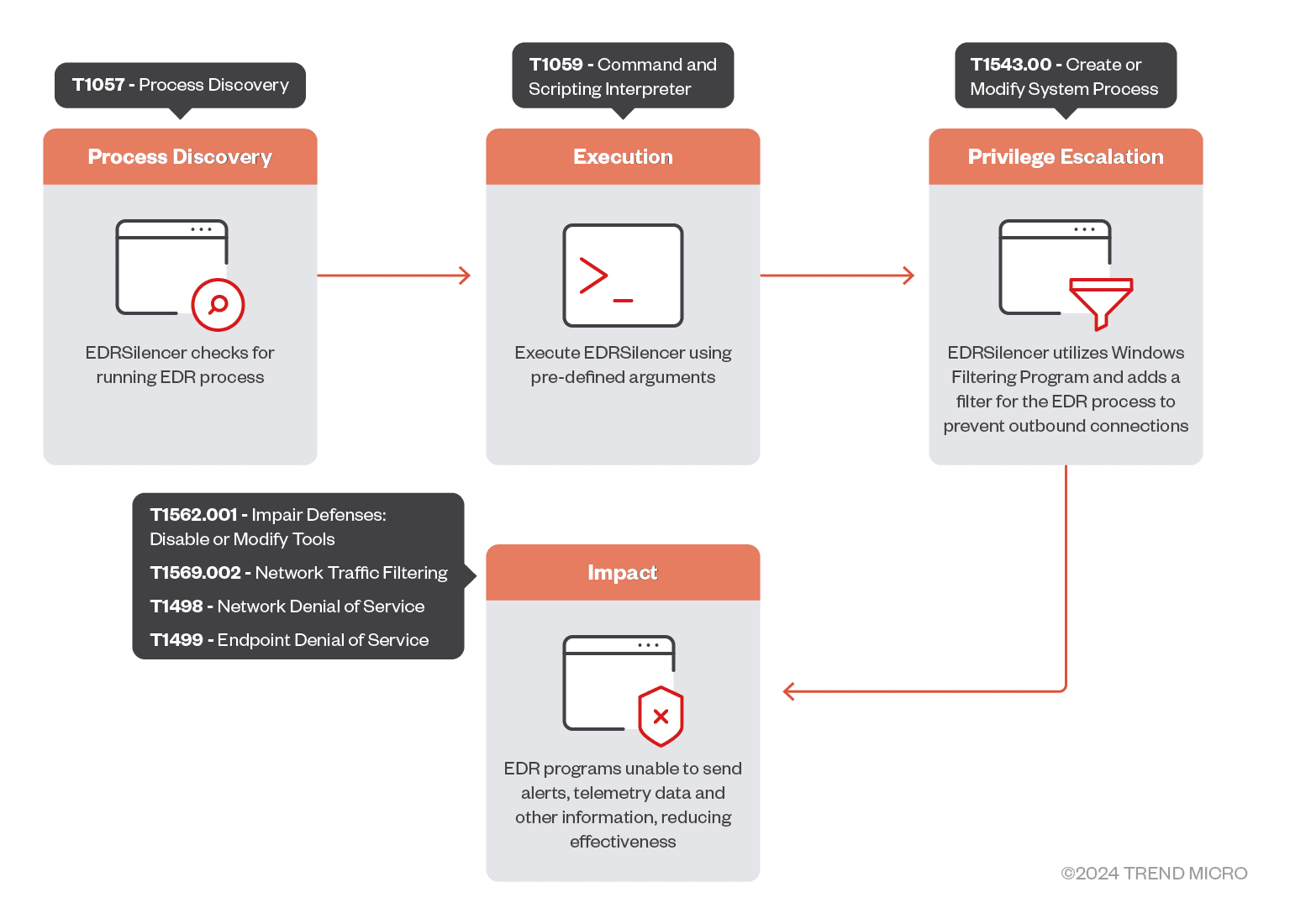
According to the Trend Micro report, EDRSilencer “disrupts the transmission of telemetry or alerts to EDR management consoles,” rendering these security tools ineffective at identifying and removing malware. By leveraging the Windows Filtering Platform (WFP), EDRSilencer blocks network communication from processes associated with various EDR products, creating a blind spot in an organization’s security defenses. This is particularly dangerous as EDR systems are crucial for monitoring endpoint activity for signs of malicious behavior.
EDRSilencer operates by dynamically identifying running EDR processes and creating WFP filters to block their outbound communication. The tool has been found to block processes even beyond its hardcoded list, further demonstrating its effectiveness. During testing, it was observed that “some EDR processes were still able to communicate because they were not included in the hardcoded list,” but after blocking additional processes, the tool successfully prevented logs from being sent to management consoles. This allows attackers to operate undetected, increasing the likelihood of successful breaches.
The tool offers several command-line options, including blockedr, which automatically blocks all detected EDR processes, and block <path>, which allows for targeted blocking of specific processes by providing their full file path. These capabilities allow cybercriminals to adapt their attacks to bypass specific security measures.
EDRSilencer represents a dangerous trend in the repurposing of red team tools for malicious purposes. While red team tools are essential for helping organizations identify weaknesses in their security posture, they can be easily turned into offensive weapons by threat actors. As Trend Micro emphasizes, “threat actors are continuously finding ways to repurpose these tools for malicious purposes,” and EDRSilencer is a prime example of this.
The ability to disrupt EDR solutions, which are critical for detecting and responding to cyber threats, poses a significant risk to organizations. Once an attacker uses EDRSilencer to block EDR traffic, malware can remain hidden on a system, undetected by security teams. This increases the risk of prolonged cyber attacks and data breaches, with potentially catastrophic consequences.





