Source
![]()
Introduction
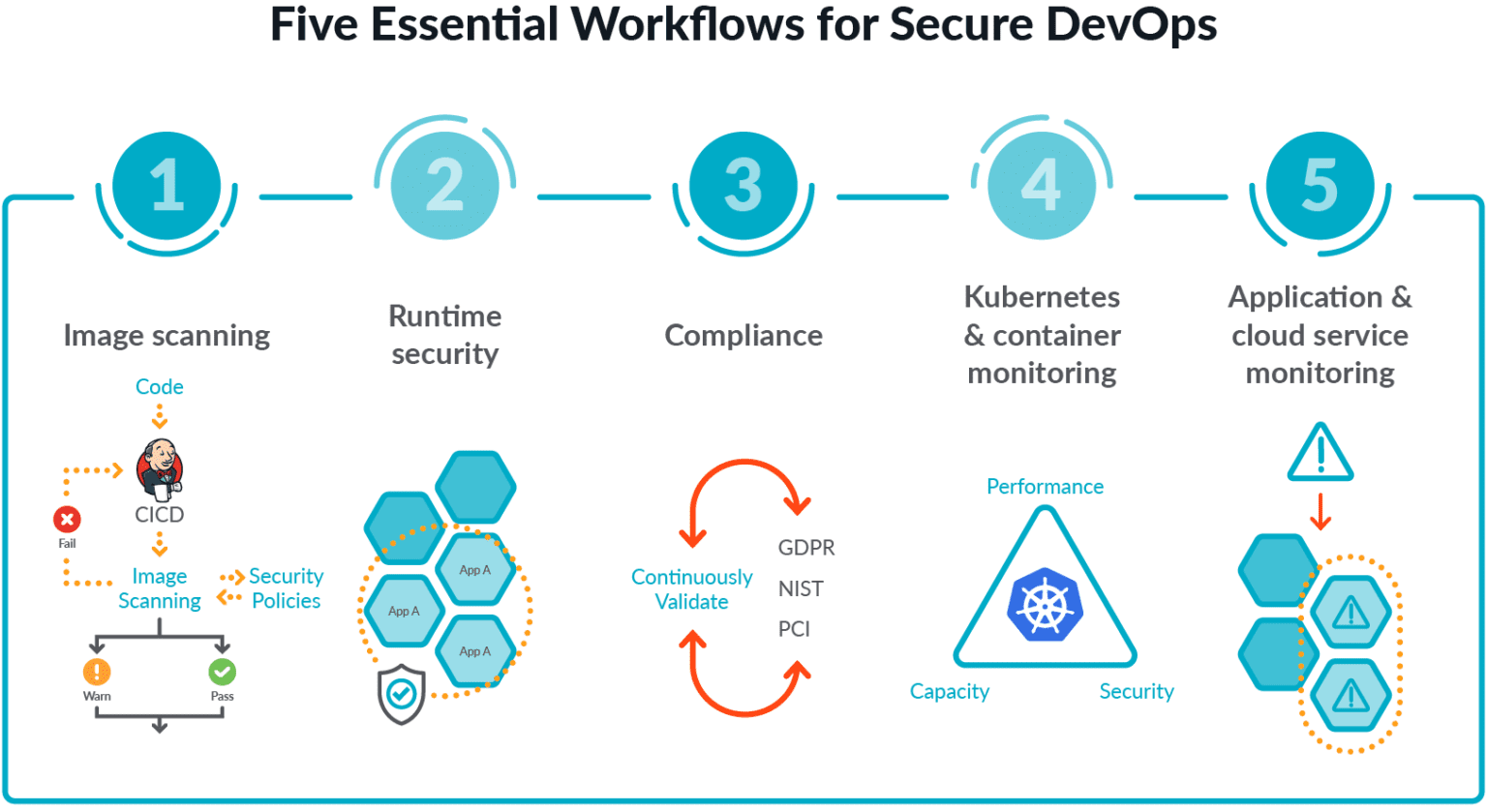
As organizations increasingly adopt containerization technology like Docker to enhance application deployment and scalability, it is crucial to address the security risks associated with it. Docker images serve as the foundation of containerized applications, and any vulnerabilities present in these images can pose serious threats to the entire infrastructure.
In order to address these potential risks, it is crucial to establish strong security measures right from the start. Employing thorough Docker image scanning serves as a potent strategy for guaranteeing the security and soundness of container images at every stage of their development and deployment.
Understanding Docker Image Scanning
Docker image scanning is a security practice that involves analyzing container images for vulnerabilities and potential security risks. The process involves checking the image’s software dependencies, libraries, and other components for known vulnerabilities and ensuring they adhere to established security standards.
By proactively scanning Docker images, developers and operations teams can identify and fix security issues before the images are deployed, minimizing the attack surface and enhancing the overall security posture.
The Benefits of Docker Image Scanning
Docker image scanning offers a critical advantage by proactively identifying vulnerabilities within container images. This process enhances security, enabling timely patching and minimizing potential risks during development and deployment. As a result, organizations can ensure the integrity of their software supply chain and maintain robust protection against potential threats.
Early Detection of Vulnerabilities
First, Docker Image Security Scanning enables developers to identify vulnerabilities during the development phase itself. This is crucial. By integrating scanning tools into the CI/CD pipeline, teams can automate security checks and receive instant notifications about any detected issues. This early detection ensures that vulnerabilities are addressed promptly, reducing the risk of exploitation in the production environment.
Improved Compliance and Risk Management
In industries with strict regulatory requirements, image scanning helps ensure compliance with security standards. It allows organizations to monitor and manage risks effectively, providing clear insights into the security posture of containerized applications.

Enhanced Trust and Confidence
Image scanning provides stakeholders, customers, and end-users with greater confidence in the security of their applications. Demonstrating a commitment to security from the outset fosters trust and improves the organization’s reputation.
Implementing Docker Image Scanning
Let’s explore how to implement Docker image scanning using popular open-source tools Trivy and Docker Security Scanning.
Trivy
Trivy is a simple and comprehensive vulnerability scanner specifically designed for container images. It leverages a vast vulnerability database to scan images for known security issues.
| # Scanning a Docker image with Trivy trivy image <image_name> |
Docker Security Scanning
Docker Hub provides an automated security scanning feature for Docker Official Images. This feature scans Official Images for known vulnerabilities and displays the results on Docker Hub.
| # Enable Docker Security Scanning for an Official Image FROM nginx:latest |
Best Practices for Secure Docker Image Scanning
To ensure the utmost security during Docker image scanning, organizations should adhere to several best practices. Regularly updating base images, integrating scanning into CI/CD pipelines, monitoring image registries, and promptly patching vulnerable images are essential steps for safeguarding containerized applications from potential security threats.
Emphasizing these practices ensures that only trusted and secure images make their way into production environments.
- Regularly Update Base Images: Use the latest and official base images as they often include security patches. Regularly update these images to ensure you are running the most secure versions.
- Implement Image Vulnerability Scanning in CI/CD: Integrate image scanning into your CI/CD pipeline to automatically scan images before deployment. This practice ensures that only secure images make it to production.
- Monitor Image Registries: Keep track of your image registries and set up alerts for any security vulnerabilities or suspicious activities.
- Patch and Rebuild Vulnerable Images: If a vulnerability is found in a base image or any application layer, patch and rebuild the affected images immediately.
Integration with Security Policies and Governance
To achieve comprehensive security and governance in containerized environments, it is essential to integrate Docker image scanning with existing security policies and governance frameworks. This integration ensures that your image scanning aligns with organizational security requirements and regulatory guidelines. Here are some key steps for effective integration:
Define Security Policies
Establish clear and well-defined security policies that specify the minimum security standards for Docker images. These policies should outline the allowed image sources, base image versions, and mandatory vulnerability thresholds.
Implement Policy Enforcement
Integrate the security policies into the image scanning process. The scanning tools should be configured to enforce the defined policies and flag images that fail to meet the security criteria.
Centralized Image Repository
Use a centralized image repository to store approved and scanned images. Implement access controls to ensure that only authorized personnel can push images to the repository, minimizing the risk of malicious or insecure images being deployed.
Continuous Monitoring and Auditing
Regularly monitor and audit the image scanning results and track changes in the vulnerability landscape. Perform periodic reviews of security policies to align them with the evolving threat landscape and compliance requirements.
Incident Response
Create a clearly outlined incident response strategy for addressing security breaches or vulnerabilities detected in production settings. This strategy should encompass protocols to promptly recognize and alleviate security concerns within containerized applications.
Beyond Vulnerability Scanning – Runtime Protection
While Docker image scanning is a crucial step in securing containerized applications, it is not the only line of defense. To ensure comprehensive security, organizations must also implement runtime protection mechanisms. Runtime protection involves monitoring and securing container behavior during execution. Here are some key aspects of runtime protection.

Container Firewall
Implement container firewalls to control network traffic and prevent unauthorized communication between containers. Segmenting container networks based on their trust levels adds another layer of security.
Runtime Behavioral Analysis
Employ runtime behavioral analysis tools that continuously monitor container behavior and detect suspicious activities. Anomalous behavior, such as unauthorized access attempts or unusual network connections, can indicate potential security threats.
Container Image Integrity
Verify the integrity of container images during runtime to detect tampering or unauthorized changes. Technologies like digital signatures and cryptographic checksums can help ensure image integrity.
Least Privilege Principle
Enforce the least privilege principle by restricting container permissions to the minimum required for their intended functions. Restricting privileges minimizes the potential impact of security breaches.
Runtime Patching
Consistently apply updates and patches to active containers in order to resolve recently identified vulnerabilities. Employing continuous integration and delivery pipelines can automate the task of integrating the most recent security patches into containers.
Conclusion
Docker image scanning is a crucial aspect of ensuring security from the ground up in containerized environments. By identifying and addressing vulnerabilities early in the development process, organizations can significantly reduce the risk of security breaches and data compromises.
The implementation of robust image scanning practices, combined with continuous monitoring and timely updates, creates a secure containerization ecosystem, fostering trust and confidence among stakeholders. Emphasizing security throughout the container lifecycle is essential for building a robust and resilient infrastructure in the age of modern application deployment.