ESET Unveils “Bootkitty”: The First UEFI Bootkit Targeting Linux Systems
ESET researchers have unveiled Bootkitty, the first UEFI bootkit designed to target Linux systems, marking a new chapter in the evolution of UEFI threats. While previous bootkits exclusively targeted Windows platforms, Bootkitty signals a paradigm shift, underscoring the expanding scope of UEFI-based attacks.
According to ESET, Bootkitty is currently regarded as a proof of concept rather than an actively deployed malware. However, its existence sends a stark warning: UEFI bootkits are no longer confined to Windows platforms. “its existence underscores an important message: UEFI bootkits are no longer confined to Windows systems alone,” ESET researchers stated.
The bootkit operates by disabling the kernel’s signature verification feature, effectively allowing unsigned kernel modules to be loaded. During its initialization process, Bootkitty preloads two ELF binaries through the Linux init process.
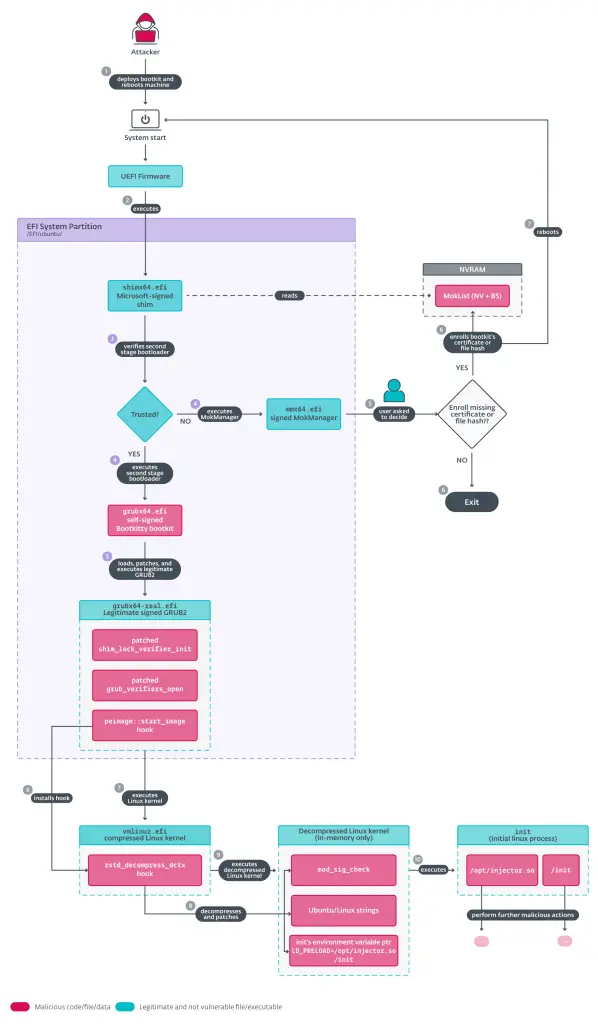
Bootkitty execution overview | Image: ESET
Bootkitty employs intricate techniques to achieve its goals. Upon execution, it hooks into UEFI security authentication protocols, manipulating outputs to bypass integrity verification checks. Subsequently, it modifies the Linux kernel image at hardcoded offsets during the decompression phase. ESET notes, “Due to the lack of kernel-version checks, Bootkitty can patch completely random code or data, potentially crashing the system instead of compromising it.”
Additionally, the bootkit leverages hardcoded byte patterns to identify functions for modification, limiting its effectiveness to specific configurations. Researchers believe this constraint, coupled with unused functions and debug artifacts, reinforces its status as a prototype rather than fully operational malware.
ESET’s investigation uncovered a possibly related unsigned kernel module, dubbed BCDropper, uploaded to VirusTotal alongside Bootkitty. This module embeds and executes an ELF file named BCObserver, which subsequently loads another kernel module post-system startup. Despite certain overlaps, ESET has not confirmed a direct relationship between Bootkitty and BCDropper.
Though currently unrefined, Bootkitty demonstrates a capability to bypass UEFI Secure Boot on Linux systems, a feature designed to prevent unauthorized code execution during system startup. This underscores the growing sophistication of threat actors targeting Linux environments. ESET cautions users, “To keep your Linux systems safe from such threats, make sure that UEFI Secure Boot is enabled, your system firmware and OS are up-to-date, and so is your UEFI revocations list.”
For forensic and preventive measures, a detailed list of indicators of compromise (IoCs) is available in ESET’s GitHub repository.